AOSP Biannual Releases: 2026 Shipping Playbook
Google has moved Android’s public source code schedule to AOSP biannual releases in Q2 and Q4. That’s the headline—and it’s not just trivia for ROM maintainers. If you ship Android apps, operate a device program, or run mobile CI/CD, your 2026 delivery plan just changed. The good news: you can make this work in your favor with a tighter release train, better risk isolation, and clearer stakeholder comms.
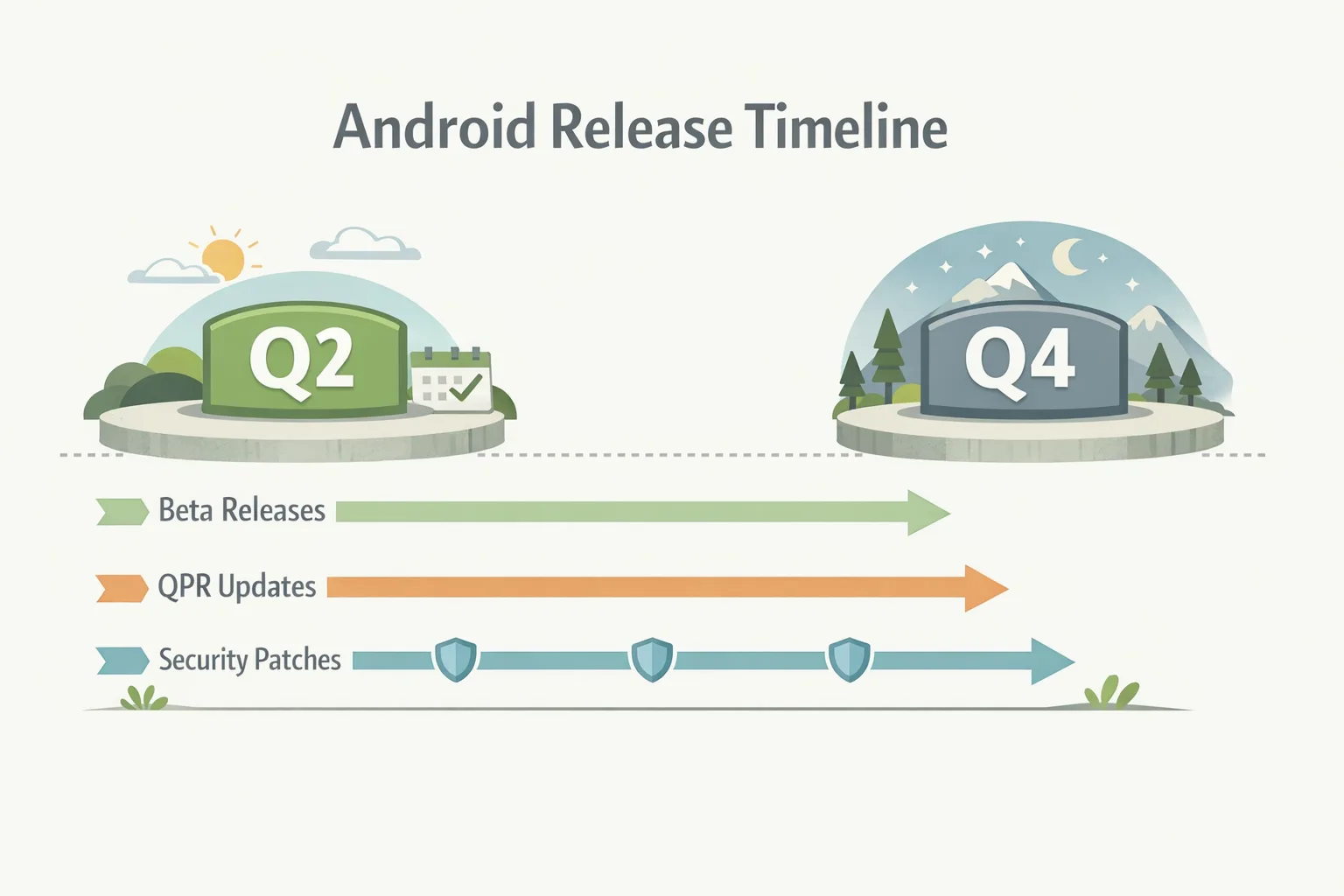
Why AOSP biannual releases matter now
Historically, the Android Open Source Project dropped code four times a year around the quarterly platform releases. In 2026, Google is consolidating those public code drops to twice a year while keeping ongoing development internal and continuing quarterly platform maintenance via QPRs. Security updates continue on their own track; for example, the January 5, 2026 bulletin shipped with the 2026-01-05 patch level, and Pixel’s January update followed a week later. This means your visibility windows into platform-level changes narrow, but your planning windows can actually become cleaner.
Here’s the thing: less frequent public code drops don’t mean fewer platform changes. They mean the external synchronization points are fewer. If your team treats those Q2 and Q4 drops as anchor points—and layers your own preview/Beta testing and security patch intake around them—you’ll reduce thrash and ship more predictably.
Q2/Q4 cadence: what actually changed (and what didn’t)
Three concrete shifts to internalize:
1) Source code drops to AOSP now arrive twice a year: one in Q2 (major) and one in Q4 (minor). Expect a bigger API or platform swing mid-year and a stabilizing drop before holidays.
2) The recommended manifest for platform work is android-latest-release rather than aosp-main. If you build against AOSP, adjust your repo manifests and tooling to track the latest stable branch instead of a fast-moving tip.
3) Security cadence remains separate. Partners and the community still see monthly bulletins and Play system updates. January’s 2026-01-05 patch level is your current baseline for enterprise devices; Pixel’s corresponding update bulletin landed January 12. Keep security budgets and SLAs aligned to that monthly rhythm, not the Q2/Q4 platform rhythm.
What didn’t change? Android will still surface public previews and Betas for app developers to validate behavior and prep for targetSdk changes. QPRs (Quarterly Platform Releases) continue, with Android 16 QPR2 visible in docs as of December. In short, the app-facing lifecycle (SDKs, Betas, Play requirements) remains recognizable even as source governance tightens.
Who’s affected—and how
App product teams: Your biggest risk is late discovery of behavior changes when they consolidate into the Q2 drop. Mitigate by staying on current SDKs, running instrumentation on pre-release builds, and maintaining a rolling canary channel.
OEM/device programs: Your BSP and kernel integration windows now cluster around two code-sync moments. If you sell devices, plan for a mid-year feature uplift and a Q4 stabilization release, with security-only updates in between. Your contract manufacturers will appreciate the predictability.
Custom ROMs and regulators: Fewer public drops can slow community diffs against stock Android, though security bulletins still flow monthly. If you rely on external audits, sync your assessment cycles to those Q2/Q4 events and insist on patch-level attestations monthly.
Enterprise IT and security: Treat January’s 2026-01-05 as your baseline, then enforce monthly SLAs. Don’t wait for Q2 to roll remediations; the platform cadence is not the security cadence.
The 6‑part shipping playbook for 2026
1) Wire your watchlist: channels, dates, and branches
Stop refreshing aosp-main and follow the artifacts that actually predict your work:
• android-latest-release manifest: Update your repo tooling to pull this branch. It always points to the most recent stable AOSP release, which is the anchor you’ll be testing and forking against.
• Monthly security bulletins: Track the patch level string (e.g., 2026-01-05) and map it to SLAs for your fleet or app dependencies. Build dashboards that turn “patch released” into “rollout complete” within your environment.
• QPR notes and platform docs: Android 16 QPR2 is already documented. Bake those changes into your regression suites before Q2 lands.
2) Rebuild your release train around two anchors
Use this “90/60/30” model for the Q2 and Q4 drops:
• T‑90 days: Freeze product scope for the upcoming cycle. Start Beta coverage on supported devices and cloud device farms. Lock dependency bumps (Gradle, AGP, NDK) unless a security patch compels them.
• T‑60 days: Branch for release. Instrument startup, ANR, and jank budgets. Turn on additional logging for runtime-permission flows and storage APIs that tend to regress.
• T‑30 days: Ship a public canary/beta to at least 5% of your audience. Enable server-side feature flags for fallback paths. Draft store listing updates and support macros so customer care can route issues by patch level or model.
After the drop: hold an explicit stabilization sprint. Defer new features for two weeks while you hunt crashes from OEM-specific changes and background restriction tweaks.
3) Strengthen test strategy for a private‑dev world
When more development happens behind closed doors, you compensate with broader runtime coverage and earlier telemetry:
• Maintain two device matrices: a Pixel-first lane (to catch platform changes early) and a diversified OEM lane (Samsung, Motorola, Xiaomi, etc.) for vendor overlays.
• Add policy tests: background execution limits, foreground service types, storage and media permissions, and exact alarms. These often shift subtly between QPRs.
• Monitor Play integrity and app compatibility changes in pre-release notes. Even if source isn’t public, behavior toggles (via feature flags) can surface and impact your app.
4) Feature flags are your friend—use them deliberately
Android calls out “feature launch flags” to keep trunk stable. Mirror that discipline in your app and services:
• Explicit rollback plan: Every new capability ships behind a flag with a documented kill switch. No exceptions.
• Runtime-driven config: Store flags in a signed, cacheable payload with device- and version-targeted rules. Include a policy to auto-disable on crash spike or strict-mode violation.
• Metrics upfront: Attach success criteria to the flag from day one: cold start P95, frame time P95, battery delta, and user-visible crash rate. If it’s worse than baseline by X%, the flag flips off automatically.
5) Separate security from platform upgrades
Teams get into trouble when they bundle security and platform work. Don’t. Treat monthly security intake—like the January 5, 2026 patch level—as a pipeline with its own MTTD/MTTR targets. Platform work rides the Q2/Q4 train; security patches ride an always-on escalator. If you build ROMs or manage enterprise fleets, gate app rollout on both variables: the app version and the device patch level.
6) Vendor dependency management
Kernel modules, GPU drivers, camera stacks—these bits drift. Maintain a vendor compatibility doc that lists your critical device targets, driver versions, and known quirks. When the Q2 drop lands, run a “diff day” where you compare behavior across the same app build on last quarter’s OS versus the new build, device by device. It’s unglamorous, but it’s how you avoid week‑three fire drills.
People also ask
Will fewer AOSP drops slow security patches?
No. Security patch levels continue monthly and are tracked separately from platform code drops. Your process should reflect that separation—monthly security intake, twice-yearly platform stabilization.
What’s the difference between android-latest-release and aosp-main?
android-latest-release always points to the newest stable AOSP branch—the one you should build against for predictable results. aosp-main is a moving target; with more development done internally, it’s less useful as a day-to-day baseline for product teams.
How should custom ROMs plan under the new cadence?
Shift your big merges and feature integration to Q2 and Q4, and run a monthly security merge process keyed to bulletin patch levels. Advertise patch-level strings prominently so users and auditors can see compliance at a glance.
Does this change SDK or Play requirements?
Expect the usual app-facing timelines—SDK previews and Beta seasons—to remain. What changes is your access to full source diffs, which now concentrate around Q2 and Q4. Keep an eye on QPR notes and developer communications to anticipate behavior changes.
Risks and edge cases you should plan for
Hidden behavior toggles: With feature launch flags, behavior can shift without a code drop. Use runtime probes and integration tests to detect changes in notifications, battery restrictions, or media permission prompts.
OEM overlays: A vendor may adopt the Q2 codebase but hold back a policy tweak until a carrier approval. Test on carrier SKUs, not just retail unlocked devices.
Binary compatibility: If you ship native code, track NDK versions and ABI changes across QPRs. Keep a smoke test that loads your most exotic JNI paths on every build of Android 14–16 to catch symbol resolution issues.
GPU regressions: Graphics stacks change frequently and can show up as jank or thermal throttling. Pin representative devices to a soak test with a consistent scene and record frame time deltas week over week.
Enterprise support windows: Your customers will ask whether you “support Q2 drop on day one.” The right answer is a staged rollout with device allowlists. Document it, explain it, and stick to it.
Practical tooling: CI/CD and observability
• Matrix sharding: Split tests by OS and vendor family to get signal fast. If you only have budget for one cloud device farm lane, prioritize Pixel (for platform signal) and your top OEM by MAU (for overlay risk).
• Real user monitoring: Add patch level and build fingerprint to your crash and performance events. That gives you near‑real‑time views of regressions tied to OS updates rolling out in the wild.
• Release notes automation: Generate release notes that summarize behavior changes by OS version and patch level. Tie them to support macros so CS can triage efficiently.

Data points to brief your stakeholders
• AOSP source drops now occur twice per year: once in Q2 and once in Q4.
• January 2026 security patch level is 2026-01-05, with Pixel’s update bulletin dated January 12, 2026.
• Android 16 QPR2 is referenced in official docs as of December, indicating ongoing quarterly stabilization within the major version.
• Manifest guidance shifted to android-latest-release for building and contributing, replacing reliance on aosp-main.
A simple governance checklist for your next cycle
Copy this into your team’s runbook:
• Decision log: At T‑90, record targetSdk, minSdk, AGP, NDK, and Jetpack versions. No silent upgrades mid‑cycle.
• Flag registry: Every user‑visible feature behind a flag with a rollback plan and owners.
• Patch-level SLO: Define “security patch intake to 50% of fleet in ≤14 days” (or your risk tolerance) and track it.
• Two matrices: Pixel lane + OEM lane in CI. Each PR must pass both to merge.
• Staged rollout: 1% internal, 5% public beta, 20% guarded, 100% after two stable weeks and no regression alerts.
• Crash budget: P95 crash-free sessions ≥ 99.8% during ramp. Automatic rollback below threshold.
Adjacent deadlines worth watching
There’s a second reason to reset your 2026 plan: store policy and billing changes still require engineering time, and they love to collide with platform updates. If you’re navigating Google Play’s evolving external link and billing rules, make sure those flows are tested on the same device matrices you use for platform work. Our breakdown of fees and flow models can help you plan resourcing and timelines.
For deeper dives on these policy timelines and platform shifts, see our recent posts: fees and planning for Google Play external links, and how to ship the right flow and model. If you’re aligning engineering and finance calendars, pin those discussions to your Q2 platform train so you don’t derail stabilization.
What to do next
1) Set your anchors: Put the Q2 and Q4 AOSP drops on the roadmap, plus monthly security intake milestones. Share the calendar with product, QA, support, and marketing.
2) Repoint your tooling: Update manifests to android-latest-release, and refresh your device matrices in CI to guarantee Pixel + top OEM coverage.
3) Harden your flags: Audit feature flags. Add crash‑based auto‑rollback. Make sure support and SRE know the playbook.
4) Run a pre‑Q2 fire drill: Simulate the Q2 drop with your current canary. Can you detect and mitigate a permission behavior change within 48 hours?
5) Invest in security hygiene: Use January’s 2026-01-05 patch level to benchmark your fleet. If you manage devices, align SLAs to monthly patch levels. If you ship apps, verify performance under the latest Pixel firmware.
Want a second set of eyes on your 2026 plan? Our team ships apps and platforms for a living. Explore our services, review case studies in the portfolio, and browse more deep dives on the blog. For Android‑specific timelines, our take on AOSP’s new biannual cadence and the January 2026 security bulletin fix plan pairs nicely with this playbook.

Zooming out: this move is consistent with a trunk‑stable philosophy—fewer public branches, more controlled launches, and clearer integration points. If you operate like a platform team, you’ll be fine. If you operate like every release is a one‑off, 2026 will be painful. Choose the first path.
Ship smart.






Comments
Be the first to comment.