Android Developer Verification 2026: What to Do Now
Android developer verification is arriving in 2026, and it reaches beyond Google Play. Identity checks will be required for developers who distribute apps to certified Android devices, including via sideloading and alternative stores. Early access launched in late 2025, verification opens to everyone in March 2026, and the first enforcement lands in September 2026 across Brazil, Indonesia, Singapore, and Thailand, with global expansion following in 2027. If you publish binaries outside Play or run large-scale internal testing via direct APK links, this policy touches you.
Android developer verification: what changes in 2026
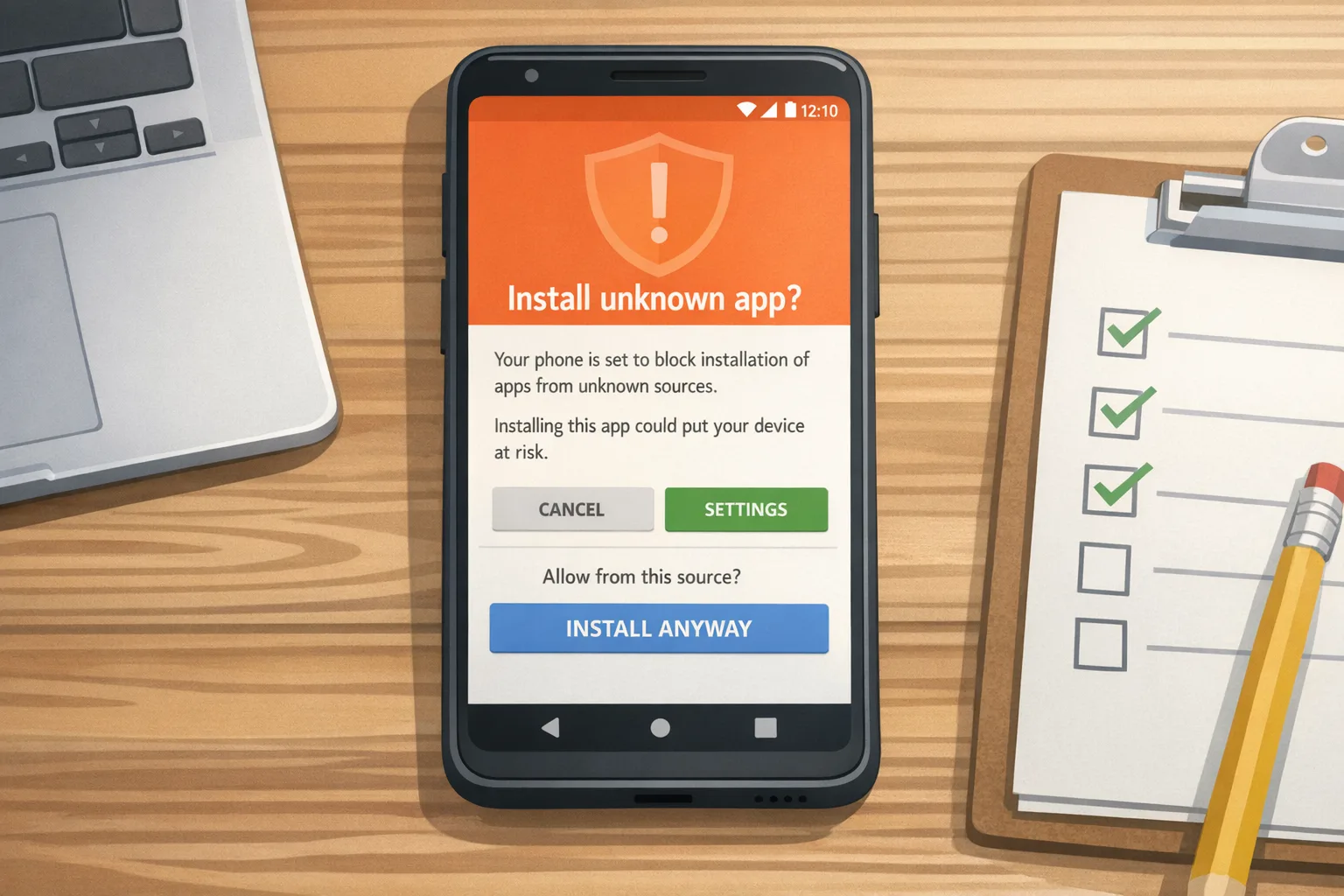
Here’s the thing: the open nature of Android isn’t going away, but anonymous distribution to users will. Google is introducing identity verification for any developer whose apps end up on certified Android devices. That means:
• If you already publish through Play Console, you likely meet most identity requirements—expect process refinements rather than a wholesale change.
• If you distribute outside Play, you’ll use a new Android Developer Console to verify your identity and register packages you intend to ship.
• Real-world impact shows up when your users install from links, mirrors, enterprise portals, or third-party stores. Those installs will check the app’s developer identity.
Key dates matter. Early access invites began rolling out in October 2025, verification opens for all developers in March 2026, and enforcement starts September 2026 in four countries before a broader global push in 2027. That’s your migration runway.
Will I still be able to sideload apps?
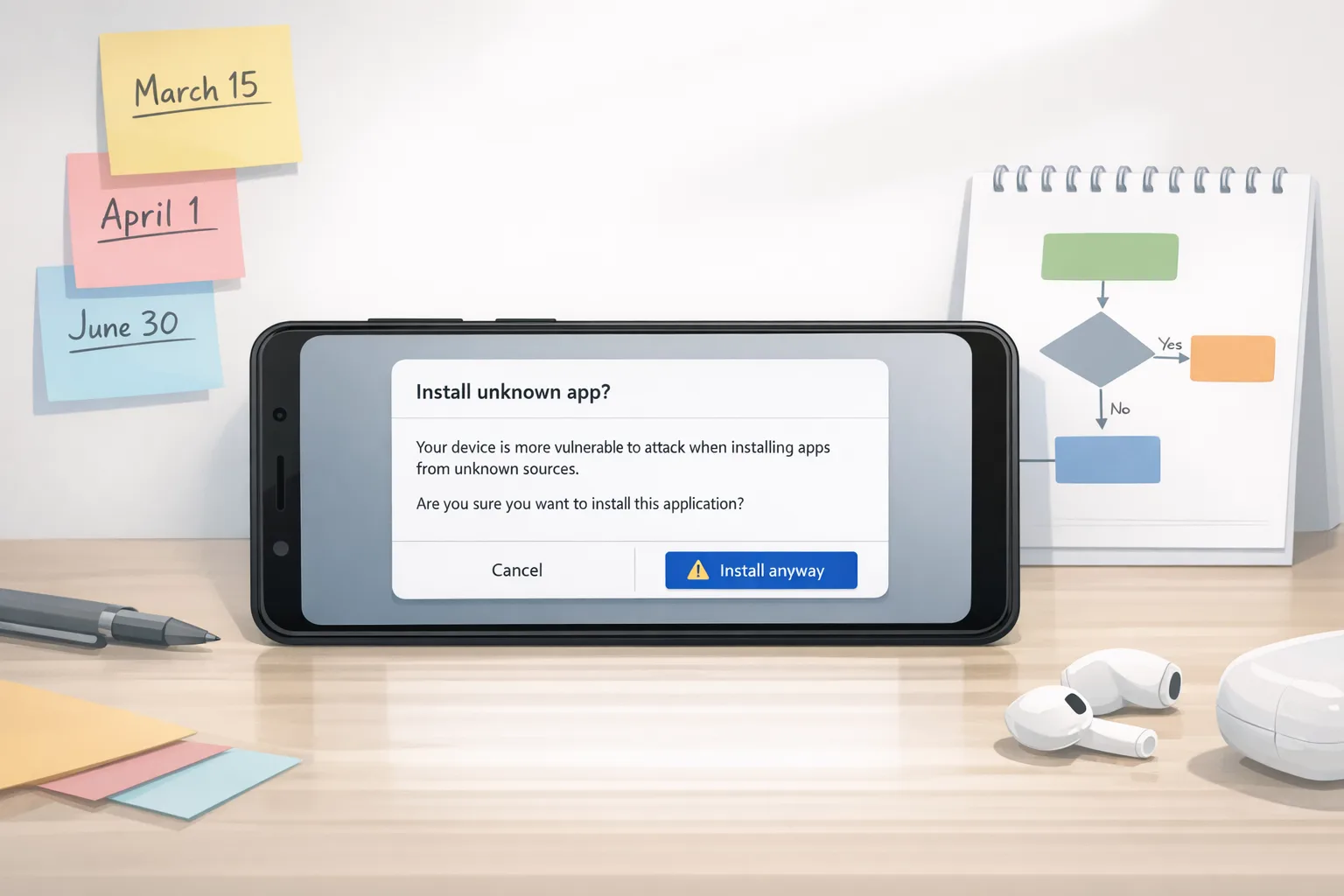
Yes—with boundaries. By default, apps must come from verified developers to install on certified devices. Google also plans an “advanced” flow that lets experienced users knowingly install unverified software after passing through explicit warnings designed to resist social engineering. In other words, power users keep an escape hatch, but scammers don’t get a free ride.
Who needs to act—and when?
• Indie and open source maintainers: If users install your APKs directly, you’ll need verification and package registration. If your distribution is purely source code and users self-build via adb, nothing changes.
• Startups running private betas: Firebase App Distribution, Play Internal Testing, or direct links to testers will require a verified identity and package registration unless all installs happen via adb from Android Studio.
• Enterprises: If you distribute internally to employee devices outside Play, treat this as a compliance project. EMM/MDM flows will need to align with verified packages, key management, and device trust policies.
• Alternative app stores: Expect store operators to surface clear verification status for onboarded apps and require publisher identity before listing.
The five‑part prep checklist
Use this pragmatic sequence. It’s how we guide clients when we audit their mobile release pipeline.
1) Inventory distribution and packages
Map where your binaries come from and how they reach users: Play, mirrors, private portals, OEM partnerships, enterprise tools, or side channels. For each app, list package name, signing key, build flavors, and target geographies. Pay special attention to any user base in Brazil, Indonesia, Singapore, or Thailand for September 2026 enforcement.
2) Decide how you’ll present your identity
Verification asks for legal name, address, email, and phone. If you’re a solo developer, consider forming an LLC to avoid exposing personal addresses. If you’re a company, designate an owner for the identity workflow and ensure contact continuity (group email, not a single employee’s inbox).
3) Register packages and lock down signing
Register every package name you ship outside Play. Rotate or confirm signing keys and document where they live. If you’re moving from legacy jarsigner/apksigner workflows, standardize on Android Gradle Plugin signing configs with protected keystores and hardware-backed signing where available.
4) Update CI/CD and testing flows
If testers install via direct links or QR codes, expect those flows to check your verification status. Move short-cycle QA to adb-based installs from Android Studio and emulators for day-to-day work, and use verified internal tracks (Play Internal Testing, enterprise distribution) for broader cohorts. Automate artifact provenance: generate SBOMs and attach build metadata so you can prove where a binary came from.
5) Communicate and measure
Draft a plain-English update for users and partners: what changes, why it’s safer, and what to expect during installation. Add a support macro for the new prompts users may see. Track install failures by country to catch early enforcement issues and unverified mirrors.
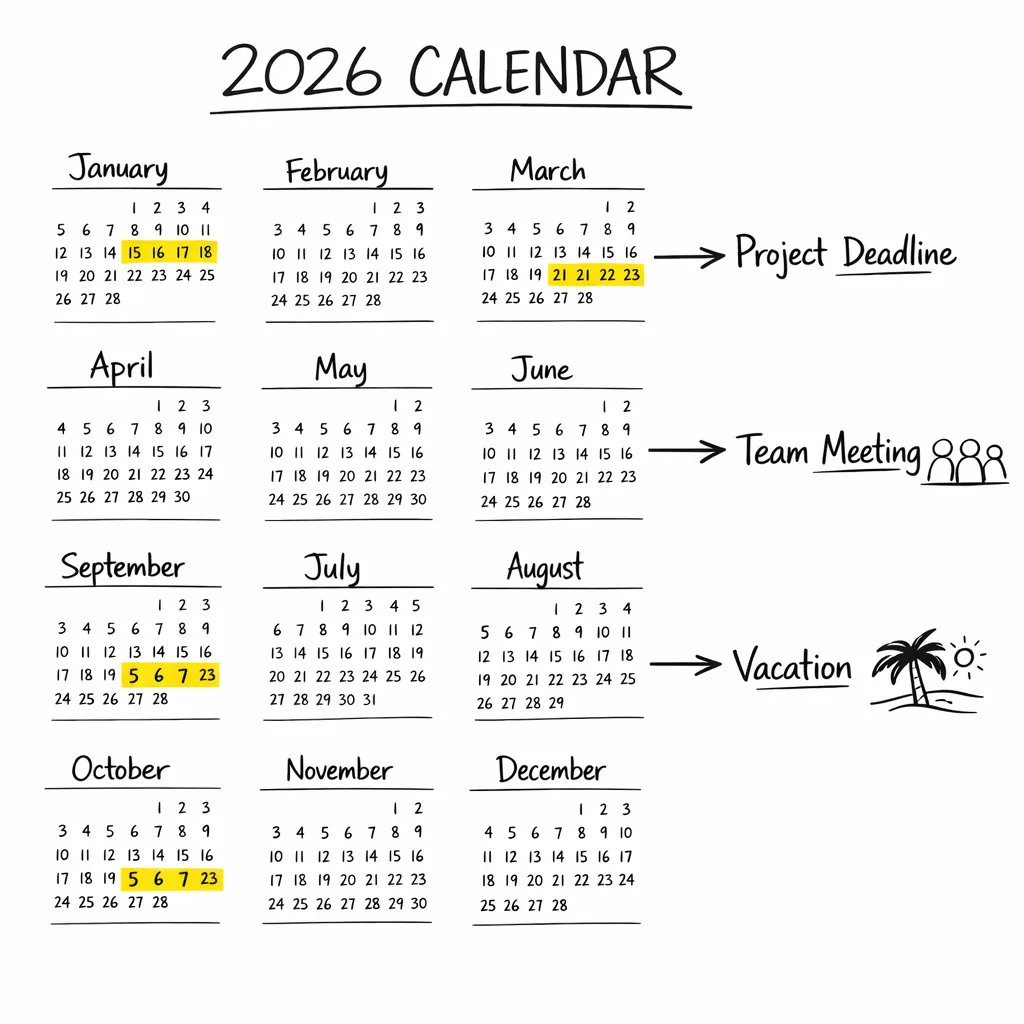
Security and policy calendar you should copy
Deadlines cluster in Q1 2026, so coordinate across product, legal, and release engineering:
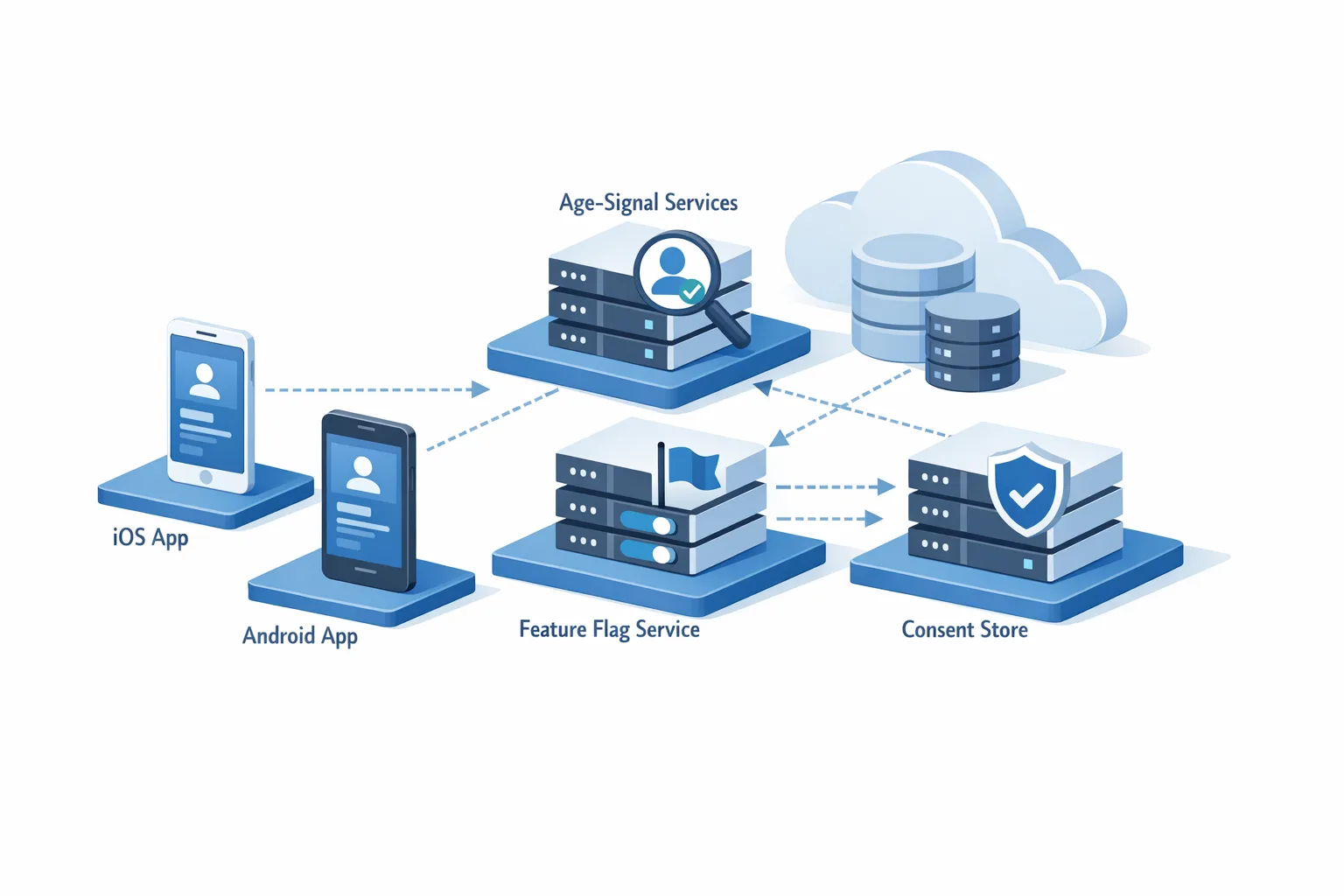
• January 1, 2026: Age Signals API data use narrows to the app receiving the data. If you rely on cross-app sharing, refactor now.
• January 5, 2026: The Android Security Bulletin sets patch level 2026‑01‑05; make sure fleet baselines and enterprise compliance dashboards reflect it.
• January 28, 2026: Crypto exchanges and software wallet apps must submit country-specific forms in Play Console for certain regions to continue operating.
• March 2026: Android developer verification opens to all developers; set up your organization, register packages, and test flows.
• September 2026: Enforcement in Brazil, Indonesia, Singapore, and Thailand; installs must come from verified developers on certified devices.
• 2027: Global expansion. Treat 2026 as your de‑risking window.
Parallel to this, Android’s public source releases shift to a twice‑yearly cadence in 2026 (major in Q2, minor in Q4). If you care about platform forks, OEM updates, or AOSP-based stacks, plan engineering milestones around that biannual rhythm. For product managers, it’s a welcome simplification.
For a deeper look at the cadence change, see our take on the biannual AOSP roadmap and how it affects OEMs and app compatibility testing.
How this impacts QA, CI/CD, and internal testing
Most teams don’t realize how often they bypass Play during pre-release. Testers grab APKs from CI artifacts, Slack, or a staging portal—and that’s exactly where verification checks will surface.
Practical adjustments:
• Make adb install your default for developer and QA devices. Android Studio and emulators are unaffected.
• For wider cohorts, move to Play Internal Testing or Firebase App Distribution with a verified account and registered packages. Validate that your tester enrollment and invite flows still “just work.”
• If you ship enterprise apps outside Play, coordinate with your EMM to ensure verified package metadata is recognized and logged.
Example workflows you can copy
• Small team beta: Build → GitHub Actions → sign → upload to Play Internal Testing → auto-rollout to 100 testers → collect vitals → promote to Closed Testing. Keep a parallel adb path for engineers.
• Enterprise internal: Build → sign with HSM-backed key → push to EMM app catalog → require minimum patch level 2026‑01‑05 on managed devices → enforce verified package install policy → staged rollouts by department.
• Open-source project: Build reproducible release → publish on GitHub Releases → verify identity via Android Developer Console and register the package → post SHA‑256 and provenance → document how power users can opt into the advanced unverified install flow at their own risk.
Business strategy: fewer scary prompts, better conversion
This isn’t just a security story—it’s a growth story. Every scary install prompt is churn. Verified identity reduces friction, especially in markets where users are trained to distrust sideloaded apps. If your app relies on direct downloads to avoid store fees for certain flows, tighten the UX now.
We’ve written separately about Play’s rules for external links and payments. If your monetization strategy includes self-serve checkout or account top-ups, read our guidance on Google Play external links and fees so you don’t trade security gains for conversion losses.
People also ask
Does this make Android “like iOS”?
No. Sideloading and third-party stores remain allowed on certified devices. The shift is from anonymous to accountable distribution. Power users still retain an advanced, opt-in path for unverified apps, but it comes with prominent warnings.
What about alternative stores and F‑Droid?
Store operators will likely enforce identity checks on publishers and surface verification status to users. For end users, the installation decision remains; for maintainers, expect updated publisher onboarding and compliance documentation.
Will local development break?
No. Builds installed via adb for development and debugging are unaffected. Your day-to-day Android Studio workflow doesn’t change.
We’re a hobby project—do we need a company?
Not necessarily. Google has signaled dedicated account types for students and hobbyists. That said, many maintainers will still prefer a simple LLC for privacy and continuity.
Risks, edge cases, and gotchas
• “Certified devices” matters: extremely low-cost or non-certified devices may behave differently. If you target regions with a gray market for devices, test there early.
• Mirrors and aggregators: even if you don’t publish to certain sites, your APKs might be scraped and rehosted. Verification reduces install risk, but you should still publish checksums and provenance data to help users spot tampering.
• Key rotations: if you change signing keys, some enterprise install tools will treat updated packages as new apps. Document a migration path and notify admins.
• Regional communications: for Brazil, Indonesia, Singapore, and Thailand, prep localized FAQ pages and in-app education. Assume rollout weeks can affect support volume.
Let’s get practical: the one‑page plan
Below is a one-page artifact we drop into client wikis. Steal this and adjust names.
• Owner: Security Engineering (backup: Release Engineering)
• Goal: All Android packages verified and registered by June 30, 2026; install flows validated in pre-enforcement countries by August 15, 2026.
• Scope: All APKs/AABs distributed outside Play, including enterprise-only apps.
• Milestones: inventory (Feb 7), LLC/identity finalized (Mar 1), console setup and package registration (Mar 15), CI/CD changes live (Apr 5), comms prepared (May 1), pilot in Indonesia (Jul 1), go/no-go (Aug 10).
• Success metrics: install failure rate under 0.2% in target regions; zero support tickets about blocked installs after enforcement begins.
Cross‑platform heads‑up
If you ship iOS too, you’re already juggling App Store policy shifts this month. Our walkthrough of the App Store age rating update due by January 31 pairs well with this Android workstream. Treat policy compliance as a shared, cross-platform capability, not a last-minute chore on each app team.
What to do next
1) Book a one-hour working session with engineering, security, legal, and product to assign owners and dates.
2) Enroll for verification in March and register every package you plan to distribute outside Play.
3) Move broad tester cohorts to verified channels; keep adb for developer devices.
4) Prepare localized user comms for early enforcement countries and add install troubleshooting to your Help Center.
5) Track install telemetry and support queues by country; be ready to adjust mirrors and distribution links if you see a spike in blocked installs.
If you want a second set of eyes on your rollout plan or need hands-on help with CI/CD, key management, and distribution, our team does this work every week. Check our mobile release and compliance services, browse recent app launches we’ve shipped, or reach out via contacts.



Comments
Be the first to comment.