Third‑Party Cookies in Chrome: Your 2026 Playbook
The headline is simple: third‑party cookies in Chrome are still here in 2026. That doesn’t mean the old playbook magically works across all browsers—or that you can ignore consent, identity, and measurement changes. It means you need a pragmatic, cross‑browser plan that acknowledges Chrome’s status quo while building for Safari and Firefox realities. This is that plan.

Chrome kept cookies: what changed, when—and why it matters
Here’s the compressed timeline. In late 2023, Chrome tested third‑party cookie restrictions with a small cohort. Through 2024, Google floated a choice prompt for users. On April 2025 timelines, Chrome pivoted: no deprecation and no new standalone prompt. By October 17, 2025, UK regulators closed the oversight commitments tied to deprecation. Arriving at January 2026, Chrome still supports third‑party cookies by default in standard browsing.
But there’s a catch. Safari has blocked cross‑site cookies by default for years via Intelligent Tracking Prevention (ITP). Firefox ships Enhanced Tracking Protection with Total Cookie Protection, partitioning or blocking cross‑site cookies by default. And Chrome’s Incognito mode continues to block third‑party cookies, with clearer disclosures and stricter data handling.
Translation: your analytics and ad tech might “work” in Chrome’s normal mode, then silently degrade in Safari, Firefox, and private modes. The organizations winning right now are designing their data flows to be browser‑agnostic and consent‑first, rather than playing whack‑a‑mole with individual features.
Are third‑party cookies going away in 2026?
Not in Chrome’s regular mode. Expect continued support—and continued scrutiny. That said, treating Chrome as the baseline is a trap. If your remarketing, conversions, or identity depend on unpartitioned third‑party cookies, you’re already losing signal in Safari and Firefox and in any privacy-centric user journeys.
Here’s the thing: the best strategy now is not “wait and see,” it’s to build for the strictest environment, then benefit from the extra signal where it exists. That means designing for ITP/ETP first and considering Chrome an upside, not a dependency.
What this means for engineering, data, and growth teams
Let’s get practical about impact areas.
Measurement: Client‑only tags tied to third‑party cookies will under‑report on Safari/Firefox and in private modes. You’ll need consented, first‑party storage and server‑side collection to stabilize conversion attribution. In the EU/EEA, ensure your Consent Mode v2 implementation actually emits the required signals; otherwise, Google’s systems down‑level your measurement and remarketing.
Identity and login: Federation flows that relied on third‑party cookies should move to modern standards. Chrome’s Federated Credential Management (FedCM) is production‑ready; major identity providers are migrating. If you still depend on iframe‑based cookies for SSO, you’ll need the Storage Access API for Safari/Firefox and clear UX to request access.
Advertising and remarketing: Retargeting lists built purely on third‑party cookies will be uneven across browsers. You’ll recover performance with first‑party audiences: authenticated sessions, hashed email (with consent), and on‑site behavioral cohorts stored as first‑party data.
Embedded third‑party features: For legitimate cross‑site state—think chat widgets, maps, or embedded content—Chrome supports partitioned cookies (CHIPS). These scope cookies per top‑level site, preserving functionality while curbing tracking.
Third‑party cookies in Chrome: building a resilient architecture
You don’t have to boil the ocean. Use this 7‑step framework to ship incremental wins while de‑risking your stack.
1) Map where third‑party cookies matter in your product
Create a short inventory: analytics, conversion tags, remarketing, SSO/IdP flows, embedded tools, and any iframe content. Note which flows break without third‑party cookies, which degrade, and which are unaffected. Run this audit across Chrome, Safari, Firefox, and Chrome Incognito/private windows.
2) Get consent right—and verifiable
Consent isn’t a banner; it’s a data pipeline. Your CMP should initialize before any tags and pass consent state to your tag manager and downstream platforms. If you market in the EU/EEA, verify Consent Mode v2 parameters are present for analytics and ads. Use real‑user monitoring to confirm consent state is respected on every template and route.
3) Stabilize measurement with server‑side tagging
Move fragile browser‑only collection to a first‑party endpoint you control. Whether you use a managed server‑side container or a custom endpoint, the goal is consistent, consented signals—not fingerprinting. Keep a strict privacy posture: honor consent server‑side, avoid leaking identifiers, and document retention windows. If you run Node.js for your edge or API layer, align this work with your regular patching cadence; our Node.js security release checklist explains how we keep these endpoints tight.
4) Modernize identity flows with FedCM (and friends)
If you provide “Sign in with …” experiences, test the FedCM button and One‑Tap paths. You’ll likely adjust permissions‑policy headers and CSP in iframes, and you should plan UX for browsers that don’t support FedCM yet. For enterprise SSO or custom IdPs, evaluate Storage Access API prompts and design them like you would a permission dialog—clear, minimal, and at the right moment in the journey.
5) Use partitioned cookies (CHIPS) for embedded state
When you legitimately need cross‑site state in embeds—chat, maps, or CMS media—set cookies with Partitioned, SameSite=None, and Secure. That preserves per‑site state without enabling tracking across publishers. Start by running dual cookies during rollout to avoid breaking existing clients, then retire the unpartitioned version.
Set-Cookie: __Host-session=abc123; Path=/; Secure; SameSite=None; PartitionedTest this behavior in Chrome DevTools’ Application tab and verify the partition key matches the top‑level site. Avoid naming collisions between partitioned and unpartitioned cookies during migration.
6) Engineer for cross‑browser parity
Implement Storage Access API fallbacks in embedded contexts that require access to first‑party state when the browser blocks it by default. Gate requests behind real user actions and cache grants responsibly. For analytics and conversions, assume Safari/Firefox are your limiting constraints; when Chrome provides extra signals, consider that a bonus, not a baseline.
7) Make it observable
Ship dashboards that segment performance by browser, device, and consent state. Track conversion rate deltas between Chrome vs. Safari/Firefox. Add synthetic checks for sign‑in flows that exercise FedCM and Storage Access paths. Alert on consent drift: when tags fire before consent or when server‑side endpoints accept events without required flags.
People also ask
Do I still need a CMP if third‑party cookies work in Chrome?
Yes. Consent is regulatory and contractual, not just technical. Platforms increasingly require consent signals to unlock measurement and personalization features in regulated markets. A CMP that integrates deeply with your tags and server‑side pipeline is table stakes.
What about remarketing lists that used third‑party cookies?
Rebuild audiences with first‑party signals: authenticated sessions, on‑site behaviors tied to your own identifiers, and compliant hashed emails. Expect better cross‑browser stability and more durable performance than cookie‑only lists.
Will FedCM break my current Google sign‑in?
Migration typically works with minimal changes, but you should test. You may need to adjust permissions‑policy headers and CSP, and plan alternative UX on browsers without FedCM support. Don’t wait—identity is core infrastructure.
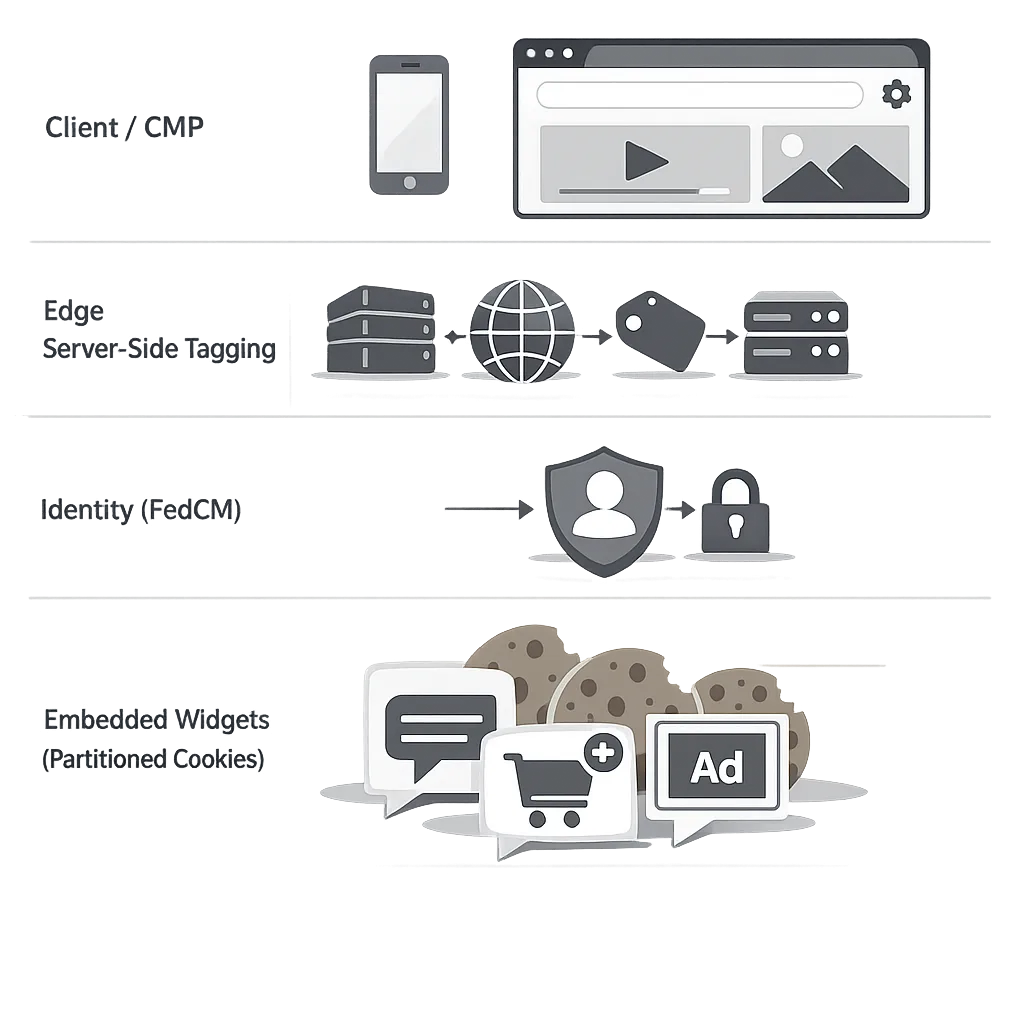
A 2026 reference architecture you can actually ship
Below is a lean pattern we’ve implemented for clients who need reliable analytics and identity flows across browsers while respecting consent.
Client tier: CMP initializes first, sets consent, and passes it to a thin tag loader. Only essential first‑party analytics fire before consent (for example, anonymous page timing with no identifiers). Ads/remarketing tags wait for explicit consent in regulated regions.
Edge/API tier: A server‑side collection endpoint validates consent parameters and appends server‑known context (e.g., geo, UA, coarse IP if allowed). It drops any disallowed identifiers, applies retention rules, and forwards events to measurement partners with appropriate flags. We deploy this on hardened runtimes and align its patch cadence with security releases.
Identity tier: FedCM where available, falling back to standards‑compliant OAuth 2.0/OIDC in non‑supporting browsers. For embedded IdP experiences, use Storage Access API with clear prompts triggered by user interaction.
Embed tier: For third‑party tools that need state, adopt partitioned cookies (CHIPS). Avoid unpartitioned third‑party cookies unless you’ve verified parity across Safari/Firefox (you won’t have it).
Data points and dates to anchor your roadmap
• April 2025: Chrome confirms it will maintain third‑party cookie choice and not roll out a standalone prompt. • October 17, 2025: UK regulators release Privacy Sandbox commitments after Google’s change in direction. • As of January 2026: Safari blocks cross‑site cookies by default (ITP), Firefox ships Total Cookie Protection and blocks cross‑site tracking by default. • Chrome’s Incognito continues to block third‑party cookies and shows stronger disclosures. • CHIPS (partitioned cookies) are supported by default in modern Chrome; use for legitimate embedded state. • FedCM is production‑ready in Chrome; major identity providers and libraries support it, with migrations in flight.
Common implementation gotchas we keep seeing
• CMP loads after tags: fixes consent theater but not the law—or platform policy. Boot the CMP and consent state first. • Server‑side tagging that ignores consent: regulators and vendors treat this as a violation. Enforce consent at the edge. • Identity flows hidden in iframes without proper permissions‑policy: FedCM and Storage Access API calls fail silently. • Partitioned cookies shipped without SameSite=None and Secure: they won’t set. • Browser mix‑ups: QA only on Chrome. You need parity runs for Safari/Firefox and private modes.
What to do next
Here’s a tight action list you can execute this sprint.
- Run a cookie dependency inventory and test critical flows across Chrome, Safari, Firefox, and Incognito/private modes.
- Move to a consent‑first tag loading sequence. Validate Consent Mode parameters where required and log them server‑side for audits.
- Stand up a server‑side collection endpoint with strict consent checks and retention rules.
- Pilot FedCM in a canary environment; adjust permissions‑policy/CSP and design fallbacks.
- Migrate embedded widgets that need state to partitioned cookies (CHIPS) and remove unpartitioned third‑party cookies.
- Instrument browser‑segmented dashboards and alert on consent drift and identity failures.
Need a partner to get this over the line?
If you want a battle‑tested implementation and fast time‑to‑value, see what we do for data, analytics, and privacy, browse the outcomes in our portfolio, and check our implementation services. If you’re modernizing your front end at the same time, our React 19 migration guide pairs well with server‑side tagging and identity updates. Ready to move? Talk to us.

Bottom line
Chrome keeping third‑party cookies doesn’t restore the “old normal.” Safari and Firefox haven’t budged, private modes are stricter, and platforms increasingly demand verifiable consent. Your competitive edge is a consent‑first, identity‑modern, cross‑browser architecture that treats Chrome’s extra signals as a bonus—not a crutch. Ship the framework above and you’ll be future‑ready regardless of what the next announcement changes—or doesn’t.





Comments
Be the first to comment.