Third‑Party Cookies Aren’t Dead: Your 2026 Playbook
Let’s say it plainly: third-party cookies are still here. After years of drafts, trials, and pushback, Google said in April 2025 that Chrome wouldn’t force a deprecation or roll out a standalone prompt, and by October 17, 2025 the UK regulator closed its oversight. That reset matters. Teams that paused migrations or over-rotated to unproven APIs now need a 2026 plan grounded in what actually ships. This guide is that plan—focused on engineering choices, usable data, and consent that doesn’t torpedo conversion.
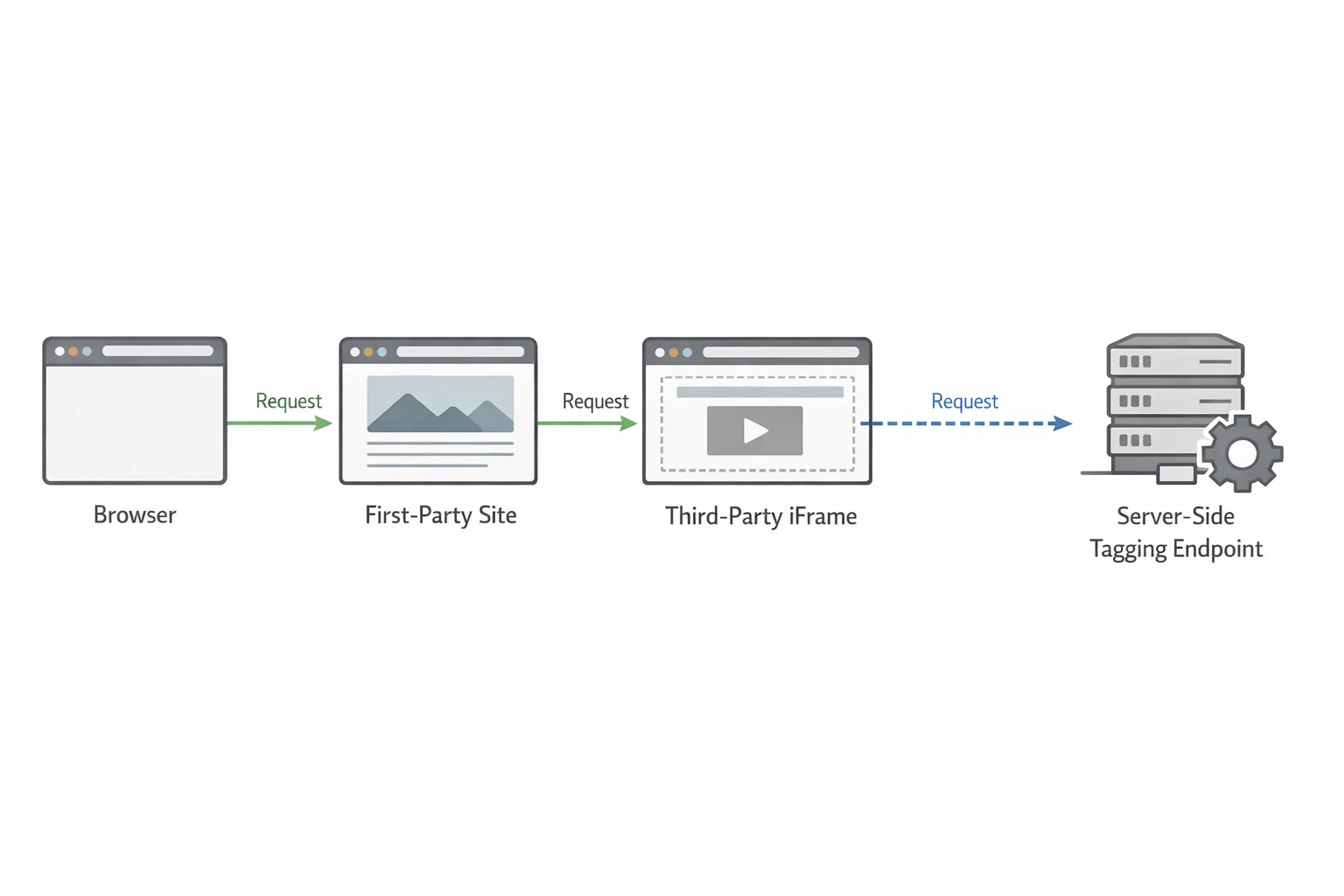
What actually changed—and what didn’t
Two dates anchor your strategy. First, April 2025: Chrome confirmed it would maintain user choice and not deprecate third-party cookies. Second, October 17, 2025: the UK Competition and Markets Authority released the commitments it had imposed around the Privacy Sandbox proposals, citing Google’s change of course. Translation: in 2026 you can still rely on third-party cookies in Chrome, but the writing on the wall from other browsers hasn’t changed.
Safari’s Intelligent Tracking Prevention (ITP) and Firefox’s Enhanced Tracking Protection (ETP) continue to clamp down on third-party cookies by default. Many enterprise firewalls and privacy extensions do the same. Meanwhile, Chrome has long shipped CHIPS—partitioned cookies via the Partitioned attribute—plus better DevTools for inspecting cookie partitions. So the web is fragmented. Instead of waiting for a grand switch-off, you need a stack that performs under mixed policies.
Primary keyword check: third‑party cookies in 2026
Here’s the thing: building for 2026 means embracing two truths at once. Third‑party cookies are still widely usable in Chrome, and they’re still unreliable across audiences and contexts. If you treat them as a bonus when present—and design graceful fallbacks when they aren’t—you’ll keep shipping without whiplash.
What this means for your stack right now
Don’t rip out stable code that works in Chrome, but stop pretending one browser’s policy covers your funnel. For most teams, the pragmatic target state is a hybrid:
- Keep critical integrations that still depend on third‑party cookies in Chrome, but instrument fallbacks for Safari/Firefox.
- Adopt CHIPS where cross-site iframes or embedded widgets need session continuity without exposing a global cross-site cookie jar.
- Move fragile client-to-vendor beacons to server‑side tagging behind your domain to reduce client failure rates and ad blocker collisions.
- Strengthen first‑party identity with signed-in experiences or soft identifiers (e.g., durable, consented user IDs) and clean data contracts.
- Tune consent UX for clarity and performance, not dark patterns—conversion and compliance both suffer when you play games.
If you’re resource‑constrained, stage this over two quarters. Use an architecture review to pick the highest‑impact surfaces: auth flows in embedded contexts, payments and post‑purchase pings, and conversion measurement for paid growth.
90‑day “Cookie Reality Check” framework
Use this lightweight framework to audit and ship improvements without boiling the ocean.
Days 0–15: Inventory and breakage map
Pull a list of all SDKs, tags, and iframes that read or write cookies. In DevTools, check the Application tab for partitioned vs. unpartitioned cookies and note which requests fail in Safari/Firefox. For auth, verify whether your embedded experiences or SSO popups assume unpartitioned third‑party cookies. Document which conversions rely on client-only beacons.
Days 16–45: Stabilize the client
Enable partitioned cookies where appropriate: set Set-Cookie: <name>=<value>; Secure; SameSite=None; Path=/; Partitioned on cookies needed inside third‑party iframes you control. Validate that cookie names don’t collide with unpartitioned variants and that your code checks for the partitioned version first. Fix SameSite regressions that break sign-in or checkout redirects, especially after vendor SDK updates.
Parallel to that, implement consent hooks that fire early but don’t block render. If you use a CMP, expose a stable, typed event contract (e.g., consent.updated) that your analytics and ad tags subscribe to. Ship skeleton UIs so the page becomes interactive while the CMP loads.
Days 46–75: Move high‑value events server‑side
Stand up a server‑side tagging endpoint on your domain (Cloud Run, Lambda@Edge, Fly.io—pick your flavor). Proxy only the events you truly need: purchases, sign‑ups, and key post‑install actions. Normalize payloads, enrich with first‑party context (user ID if consented, campaign data), and forward to vendors’ conversion APIs. Keep PII policies strict: hash emails with a stable salt where permitted and log minimal metadata.
Days 76–90: Measurement hardening
Close the loop. Compare attribution deltas in Chrome vs. Safari/Firefox. Expect higher match rates where third‑party cookies survive and smaller—but steadier—signals elsewhere via server‑side and modelled conversions. Align finance on new reporting ranges so spikes and dips don’t cause whiplash during budget reviews.
CHIPS in practice: when to use partitioned cookies
Partitioned cookies (CHIPS) give each top‑level site its own cookie jar for a third‑party context you control. That’s perfect for embedded customer portals, support widgets, or cross‑domain micro‑frontends. It’s not a stealth way to resurrect cross‑site tracking; partitioned cookies can’t be read across different top‑level sites. Treat them as scoped session state, not a targeting primitive.
Gotchas you’ll hit in the real world:
- Don’t set both
authandauth-partitionedand forget to expire the old one; you’ll confuse downstream readers. Use a temporary dual‑cookie pattern with a clear retirement date. - Audit CDN and proxy layers. Some edge middleware strips unknown cookie attributes; ensure
Partitionedpasses through untouched. - Test WebViews. Older app WebViews may lag on CHIPS; feature‑detect and gracefully fall back.
Server‑side tagging without vendor lock‑in
Server‑side tagging stabilizes measurement by moving brittle browser‑to‑vendor calls behind your domain. It also reduces the surface area of third‑party scripts on the page. The trap is recreating another black box. Keep ownership of the code path and observability:
- Keep your endpoint simple: an authenticated POST that validates schema, rate limits, and forwards to a small set of vendor APIs.
- Log to your data warehouse with a clear schema and retention. If a partner changes contracts, you still have your raw events.
- Use feature flags to switch destinations without code deploys. Triage outages fast when a vendor returns 4xx on new fields.
If this sounds like heavy lifting, we help teams ship this quickly. See what we deliver on our engagements, and explore implementation services if you need a jump start.
People also ask
Are third‑party cookies still going away?
Not in Chrome, as of January 2026. Google stepped back in 2025 and regulators closed their oversight later that year. That said, Safari and Firefox continue to block third‑party cookies by default. Reality check: your audience is mixed. Plan for both states to coexist indefinitely.
Should we still consider Privacy Sandbox APIs?
Some APIs and experiments are being reevaluated or sunset by Google, and adoption has been uneven. If an API demonstrably improves performance or privacy for your use case, test it—but don’t anchor core measurement on tools with uncertain long‑term support. Prefer standards backed by multiple engines or patterns you control, like server‑side tagging and first‑party analytics.
Do we still need a CMP and consent signals in 2026?
Yes. Laws didn’t reverse alongside Chrome’s decision. You still need valid consent (or another lawful basis) to set or read non‑essential cookies and to process personal data in many jurisdictions. Treat consent as a product surface: fast loads, clear language, and predictable event contracts for downstream tags. If you’ve been burned by slow CMPs, you can decouple render from consent logic with placeholders and late mount.
Data points you can take to your execs
Use objective milestones to reset expectations: April 2025—Chrome stated it would maintain user choice and not deprecate third‑party cookies. October 17, 2025—the CMA officially released Google from commitments tied to Privacy Sandbox changes. Chrome has supported partitioned cookies for years, making scoped cross‑site embeds viable without re‑introducing global tracking jars. That’s the world we’re in—we should optimize for it.
Risk ledger: the fine print teams overlook
Cross‑browser drift will keep widening. A fix validated in Chrome may degrade in Safari if it couples to unpartitioned cookies or relies on third‑party script state. Ad blockers will continue to target known vendor endpoints; server‑side tagging helps, but keep an eye on DNS‑based filters. And remember: partitioned cookies don’t absolve you from privacy compliance; they change scope, not obligations.
Vendor churn is another risk. SDKs auto‑update, cookie attributes change, and some partners deprecate client libraries in favor of conversion APIs with strict schemas. Insist on versioned contracts, and add synthetic tests to catch breaking schema changes before they hit production.
SEO, CRO, and analytics: make them play nicely
It’s tempting to treat this as an ads‑only problem. Don’t. SEO experiments, personalization, and CRO often rely on the same client signals. If you move measurement server‑side, ensure your experimentation framework still resolves variants quickly and exposes assignment to analytics. Avoid long‑running client mutations that delay Largest Contentful Paint; defer them or render on the server when feasible. For front‑end teams planning upgrades, our take on modernization—like what to ship with React 19—pairs well with this data cleanup.
A pragmatic checklist you can start tomorrow
- Catalog every cookie your site sets. Tag each one as first‑party, third‑party, or partitioned. Remove stale cookies and rename ambiguous ones.
- Fix
SameSiteon every auth and payment redirect. Tests should cover Chrome, Safari, Firefox, and at least one privacy‑focused mobile browser. - For embedded experiences you control, enable CHIPS and verify no CDN or proxy strips the
Partitionedattribute. - Stand up a minimal server‑side tagging endpoint. Start by forwarding only purchase and sign‑up events to one ads platform via its conversion API.
- Ship a consent event contract (
consent.updated) and instrument subscribers rather than hard‑coding vendor callbacks all over your codebase. - Align finance and marketing on new attribution baselines by browser family. Publish a one‑pager explaining expected deltas and why.

What to do next (teams and owners)
If you lead engineering, green‑light a two‑sprint effort to enable partitioned cookies for embeds you own and to proxy one conversion end‑to‑end server‑side. If you own growth, rewrite your measurement memo using the April/October 2025 milestones so stakeholders stop expecting a cookie cliff. If you’re a founder or product owner, fund the consent and data‑contract work first; it unlocks everything else. And if you want a partner who’s done this before, review our selected projects and get in touch via ByBowu Contacts.
Edge cases and debugging tips
Seeing odd login loops in an embedded app? In DevTools, verify whether you’re reading the unpartitioned cookie name from inside an iframe—switch to the partitioned variant and confirm SameSite=None; Secure are present. Payments failing after redirects? Inspect Set-Cookie headers for missing or overwritten attributes on the way back from the provider. Conversion API rejects? Diff your payload against the vendor’s latest schema and add a replay queue with backoff.
One last performance note: CMPs and analytics can crush Core Web Vitals if they render-block. Use async/defer, split critical CSS, and lazy‑mount heavy widgets. If you’ve deferred a modernization, your window is now: a stable cookie landscape plus a performance upgrade is a measurable win. Our delivery playbooks cover this balance of speed and sanity.
The bottom line for 2026
Third‑party cookies didn’t vanish; they normalized. That gives you freedom—and responsibility. Keep what works in Chrome, ship partitioned cookies where you embed experiences, migrate fragile measurement to your server, and treat consent like a first‑class feature. Do that, and you’ll collect cleaner signals, respect privacy, and keep growth predictable in a fragmented web. That’s the boring, durable kind of progress teams get rewarded for.





Comments
Be the first to comment.