Third-Party Cookies in 2026: What to Ship Now
After years of whiplash, here’s the current state: Google kept third-party cookies. No new one-click kill switch; users manage cookies in settings, and Incognito continues to block 3P cookies by default. That reversal—announced on April 22, 2025—ends the immediate cookie deprecation drama and replaces it with something more practical: ship privacy-resilient experiences that work with or without 3P cookies. (privacysandbox.google.com)

What actually changed—and what didn’t
Let’s anchor the timeline so your roadmap is based on facts, not vibes:
• January 4, 2024: Chrome turned on Tracking Protection for 1% of users to test third‑party cookie restrictions. That test happened, but the mass phase‑out never arrived. (blog.google)
• July 2024: Google floated a “user choice” approach instead of hard deprecation. (gov.uk)
• April 22, 2025: Google made it official—no standalone cookie prompt, and it will “maintain the current approach” to 3P cookie choice. Incognito keeps blocking 3P cookies; IP Protection is on the roadmap. (privacysandbox.google.com)
• October 17, 2025: The UK CMA released Google from its Privacy Sandbox commitments because the competition concerns tied to cookie removal no longer applied. Translation: the regulator closed that chapter. (gov.uk)
• Late 2025 into 2026: Google’s own developer docs note the deprecation is off. If you paused work waiting for “cookiepocalypse,” it’s time to resume—but with a smarter design. (developers.google.com)
Does this mean third‑party cookies are ‘safe’ again?
Not really. Safari and Firefox have blocked them for years. Many enterprise policies do the same. Chrome Incognito blocks them, and Chrome is adding additional protections for private sessions (IP masking via proxies in eligible regions, with sign‑in requirements). Plan for reliability when 3P cookies are missing, limited, or partitioned, because plenty of users already browse that way. (github.com)
Primary keyword: third‑party cookies—and your 2026 plan
Here’s the thing: the business problem was never just “cookies go away.” It’s that identity, analytics, and personalization have become conditional. Your job is to make revenue‑critical flows resilient under three modes:
1) Cookies work normally (Chrome default). 2) Cookies are blocked (Safari, Firefox, enterprise policies, Chrome Incognito). 3) Cookies are partitioned (CHIPS) or limited by IP Protection and other mitigations.
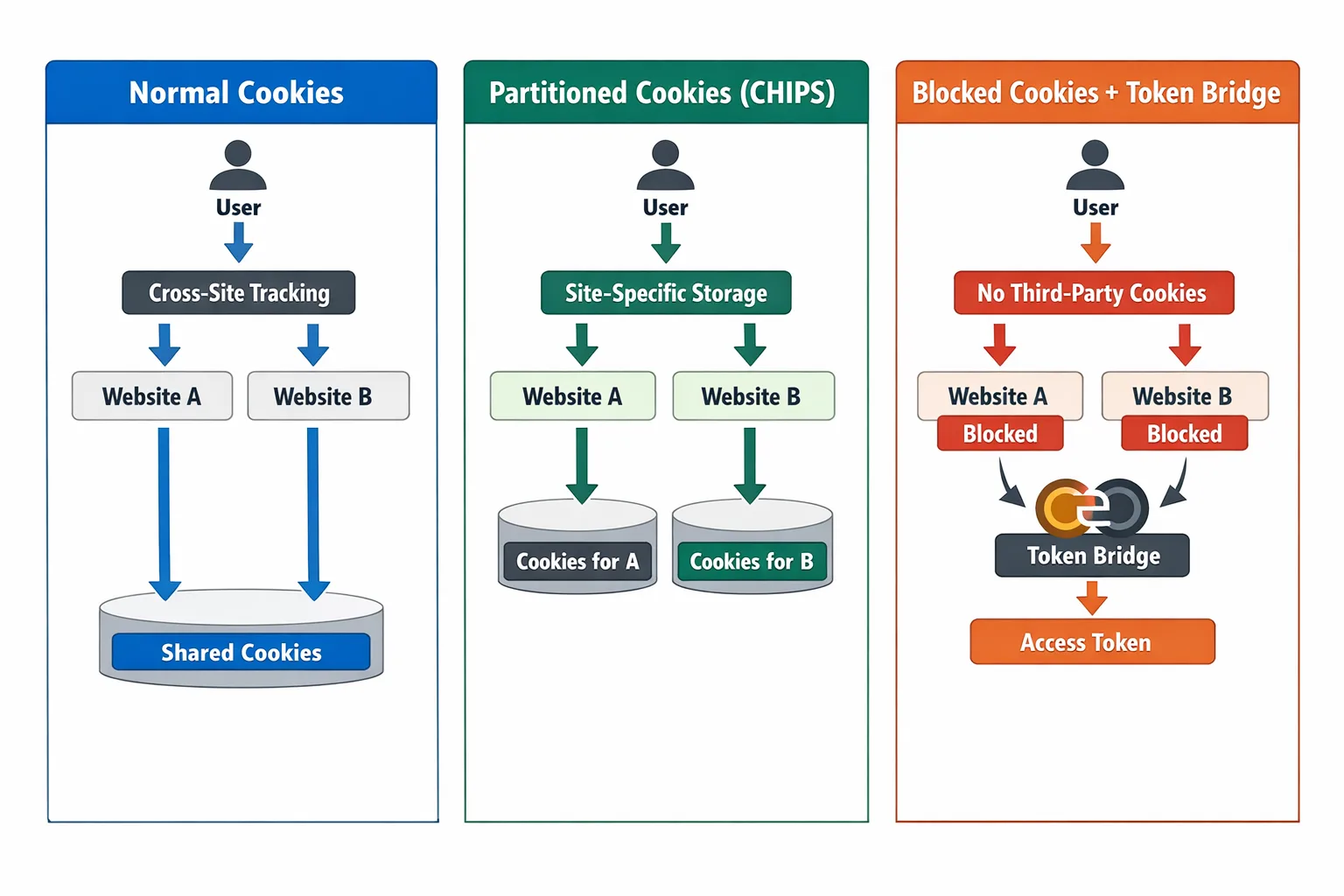
CHIPS is your friend (when used intentionally)
CHIPS—Cookies Having Independent Partitioned State—lets third‑party embeds set cookies that are double‑keyed per top‑level site. That preserves functionality (think chat widgets, embedded billing, CDN media, or preference storage) without spraying the same cookie across the entire web. In Chrome, CHIPS is supported by default (Chrome 114+). Use it to reduce cross‑site risk while keeping legitimate integration state. (privacysandbox.google.com)
How to ship CHIPS without breaking things
• Mark third‑party stateful cookies with Partitioned, Secure, and SameSite=None where appropriate.
• Treat partitioned and unpartitioned cookies as separate storage—you can’t rely on one to overwrite the other.
• Watch Chrome’s per‑partition limits (size and count) and name cookies explicitly rather than overloading a single token. (privacysandbox.google.com)
• DevTools: look for the Partition Key column to confirm what’s actually set and sent. MDN’s examples are spot‑on if you need a quick refresher. (developer.mozilla.org)
But what about Chrome’s IP Protection?
IP addresses are used for routing and anti‑fraud—and also abused for tracking. Chrome’s IP Protection masks the user’s IP for third‑party requests in Incognito via a proxy chain and a Google sign‑in gate (to rate‑limit abuse). It’s not a VPN, and it doesn’t apply to normal browsing, but it will reduce passive tracking in private sessions. Design assuming some share of your traffic—especially sensitive verticals—will have masked IPs. (github.com)
People also ask: Is Google still killing third‑party cookies?
No. Google decided in April 2025 to keep the current model: users choose cookie behavior in settings; Chrome Incognito continues to block 3P cookies by default. No forced deprecation. (privacysandbox.google.com)
People also ask: Do I still need a consent banner?
Yes. Consent is about lawful basis and transparency (GDPR/CPRA, etc.), not just cookies. If you use cross‑site identifiers, ads personalization, or advanced analytics, your Consent Management Platform remains non‑negotiable. Nothing in the Chrome update removes that obligation.
People also ask: Should we stop our server‑side tagging/first‑party data projects?
Absolutely not. The ROI on cleaner measurement and durable IDs remains strong, and those projects future‑proof you if policies change again—or if more of your audience lives in cookie‑restricted contexts.
A practical framework: Build for Conditional Identity
Use this three‑phase framework with explicit exit criteria. It’s designed to fit a two‑sprint window for most teams.
Phase 1 — Audit (1–2 weeks)
• Inventory cookies by domain, scope, purpose, and attribute set. Flag anything missing Secure, or using SameSite=None without TLS.
• Map critical user journeys that touch cross‑site storage: SSO, payments, embedded chat, help center, CDN media, A/B testing, and advertising pixels.
• Record browser distribution (Chrome/Safari/Firefox/Edge, Incognito/private share) and platforms (iOS WebKit vs. Android Chrome). Expect higher third‑party cookie block rates on iOS.
• Baseline analytics: session stitching rate, attribution coverage, cart conversion by browser, and sign‑in success for embedded flows.
Phase 2 — Adapt (2–4 weeks)
• Adopt CHIPS for third‑party embeds that truly need per‑site state; keep those cookies small and explicit.
• Add first‑party fallbacks: tokens in top‑level storage (first‑party cookies or localStorage) plus postMessage/URL‑param handoffs to iframes when cross‑site cookies are missing.
• Implement Storage Access API paths where Safari/WebKit demands it (for embedded login/profile panes). Keep your UX fast: only request access when you need it.
• Move unstable client‑side tags server‑side. If you run Google Tag Manager server‑side or a similar collector, migrate the top three revenue‑critical endpoints first.
• Strengthen consent flows: event‑level gates for ads personalization and remarketing; don’t block functional features that don’t require consent.
• Update SSO flows: where possible, avoid deep third‑party iframe logins; prefer top‑level redirects or popups with postMessage back to the embed.
Phase 3 — Measure (ongoing)
• Track delta in conversion and drop‑off by browser mode (normal vs. private where you can infer it ethically) and by partitioned vs. first‑party storage paths.
• Monitor cookie error budgets: count, size, expiration, and attribute drift across releases. Fail CI on insecure or non‑compliant cookies.
• Validate ad/analytics coverage by campaign. Focus on modeled conversions quality instead of raw last‑click volume.
Engineering checklist you can copy into Jira today
- Add
Partitioned; Secure; SameSite=Noneto third‑party stateful cookies that must persist across refresh. - Ensure every cookie with
SameSite=Nonealso hasSecure; reject in CI otherwise. - Cap cookie size (≤2 KB is a good target; Chrome enforces per‑partition budgets). (privacysandbox.google.com)
- Implement a first‑party token bridge: generate a short‑lived token server‑side; pass via URL param to the embed; store first‑party on the top domain; rotate aggressively.
- Instrument postMessage contracts between top‑level and embeds. Validate origin strictly.
- Add Storage Access API paths for Safari if your embed needs first‑party access.
- Move three highest‑volume tags to a server‑side endpoint. Preserve consent flags on the server.
- Add e2e tests that run with third‑party cookies blocked, with partitioned cookies only, and with IP masking simulated.
Designing analytics that survive cookie volatility
Measure on three layers:
• First‑party server events: log-ins, purchases, key lifecycle events—authoritative and consent‑aware.
• Client signals: pageviews, UI interactions, non‑PII diagnostics—resilient to cookie loss.
• Modeled conversions: accept some modeled attribution to account for cookie gaps; guard against over‑crediting by validating lift in geo/holdout tests.
When third‑party cookies exist, use them to improve stitching—but never to make or break core attribution.
Ad tech reality check for 2026
• Retargeting works better in Chrome normal mode than anywhere else, but your frequency capping must not depend on global third‑party cookies. Partitioned cookies and private modes will skew caps if you’re careless.
• Contextual + first‑party audiences still compound nicely. The big wins we’ve shipped lately pair on‑site signals with lightweight interest topics, then use server‑side events to reduce pixel fragility.
• Expect more private browsing. With IP masking in Incognito sessions and stronger defaults in other browsers, store only what you need, and be explicit about consent. (github.com)
Compliance: consent, contracts, and CMP hygiene
Cookies aside, regulators and platforms want enforceable transparency. Make sure your CMP exposes granular toggles (analytics vs. ads vs. personalization), stores auditable records, and propagates consent to both client and server tags. Keep DPA and processor lists current; update your privacy notice when you introduce partitioned cookies or server‑side collection paths.
Architectural patterns that aged well
• Top‑level auth + embed: run sign‑in at the top domain; pass a scoped token to the embed via URL param + postMessage; renew via silent refresh.
• Edge compute for consent gating: evaluate consent flags and geolocation at the edge and strip disallowed tags upstream.
• Progressive enhancement for personalization: render a fast generic view, then apply consented personalization in a single pass; don’t block the main thread waiting on third‑party origins.
What could change next?
Two wildcards to watch: platform‑level anti‑tracking (e.g., more private browsing adoption on mobile) and enterprise policies that default to stricter third‑party blocking. Neither requires a Chrome deprecation to impact your KPIs. Building for conditional identity keeps you safe—even if Google changes course again.
What to do next (this week)
- Run a cookie/consent health check in staging and production across Chrome, Safari, Firefox, and Chrome Incognito. Fix insecure attributes.
- Identify two embeds that break with 3P cookies blocked; pilot CHIPS there.
- Migrate one high‑value pixel to server‑side and validate parity.
- Ship event‑level consent enforcement (block ads until consent) without breaking functional UX.
- Brief your stakeholders with a one‑pager: current state, risks, CHIPS adoption plan, and the next two sprints.
Need a partner to ship this cleanly?
If your backlog is full, bring in a team that has done this before. Our engineers pair with your product and marketing leads to harden identity, analytics, and consent with measurable lift. See how we deliver complex web projects, explore our technical SEO and web performance services, browse our hands‑on shipping playbooks, or start a conversation.
FAQ for developers and product leads
Will Chrome’s decision be reversed again?
No one can promise the future, but the CMA’s October 2025 decision to release commitments is a strong signal that the regulator considers the matter closed. Plan around user‑choice, not forced deprecation. (gov.uk)
Do I need to change my CMP because of CHIPS?
Probably not, but you should clearly document where partitioned cookies are used and for what purpose. If they support personalization or advertising, ensure consent flags apply equally to partitioned storage.
Can I detect Incognito to tailor experiences?
No, not reliably or ethically—Chrome deliberately prevents this. Instead, design fallbacks that work when cross‑site cookies and IP‑based heuristics are unavailable. (privacysandbox.google.com)
Are Privacy Sandbox APIs dead?
Google’s April 2025 post reframed their role and doubled down on Incognito protections. Some APIs remain available, but your roadmap shouldn’t depend on any single experimental ad API. Build first‑party strength and server‑side collection; treat the rest as incremental. (privacysandbox.google.com)
Zooming out: we’re settling into a durable, pragmatic era. You can rely on third‑party cookies being available for a large share of Chrome users, but you can’t depend on them. Ship for conditional identity, adopt CHIPS where it makes sense, and keep your consent, analytics, and security posture tight. That’s how you grow without breaking when the next privacy wave hits.





Comments
Be the first to comment.