React2Shell Fixed: Your 2026 Production Survival Guide
React2Shell (CVE-2025-55182) landed like a punch in early December and reminded everyone that React Server Components are, in practice, server code with an internet-facing surface. The core RCE issue in the RSC Flight protocol was patched quickly in React 19.0.1/19.1.2/19.2.1, then follow-up vulnerabilities were disclosed a week later with additional patches. If your org runs Next.js 15/16 with App Router or any RSC implementation, you need both waves of fixes and a few operational guardrails to stay safe.
What changed after the December disclosures?
Two things at once: first, we learned how a crafted RSC payload could reach unsafe deserialization and execute arbitrary code server-side—no auth, no trickery beyond hitting the right endpoint. Second, we saw how quickly real actors moved. Within days, exploitation was observable in the wild against internet-facing Next.js apps and custom RSC deployments. That combination—simple pre-auth triggering plus broad framework adoption—drove the urgency and the rapid patch cadence.
Here’s the thing: RSC blurs front-end and back-end lines. When you enable Server Components or Server Actions, you’re effectively exposing a structured RPC surface (the Flight protocol) through your app. Treat it as part of your server API, with the same threat model you’d apply to JSON or GraphQL endpoints. That mindset shift is the long-term lesson from React2Shell.
React2Shell: who’s at risk and how attackers pivot
Any app serving RSC endpoints from vulnerable versions was at risk of pre-auth remote code execution. Common targets included internet-facing Next.js 15/16 apps using the App Router and Server Actions. Once on a host, attackers didn’t stop at dropping a web shell—they pivoted: enumerating cloud credentials, scraping environment variables, tampering with CI deploy keys, and planting persistence through systemd timers or Node process managers. On containerized fleets, they probed lateral movement via metadata services and build artifact stores.
Don’t assume you’re safe because you “don’t use Server Actions.” Many projects pulled in RSC packages implicitly through framework defaults. If your build included react-server-dom-* packages in the affected ranges, you needed a patch even if you believed the feature was dormant.
Which versions are safe today?
There were two meaningful waves of updates:
Wave 1 (RCE fix): React shipped patches for the RCE disclosed on December 3. Safe minimums for that issue were React 19.0.1, 19.1.2, and 19.2.1 across the RSC packages (react-server-dom-webpack/parcel/turbopack). Next.js shipped corresponding patches across supported release lines.
Wave 2 (DoS + source exposure): On December 11, additional vulnerabilities were disclosed, and fixes were backported again. As of early January 2026, you should target these minimums or newer:
- React RSC packages: 19.0.3+, 19.1.4+, or 19.2.3+ (depending on your minor line).
- Next.js: for App Router projects, run at least 15.5.7 on the 15.x line or 16.0.7 on the 16.x line (or newer patch releases). If you’re pinned to earlier minors, confirm your exact patched micro—several point releases shipped rapidly.
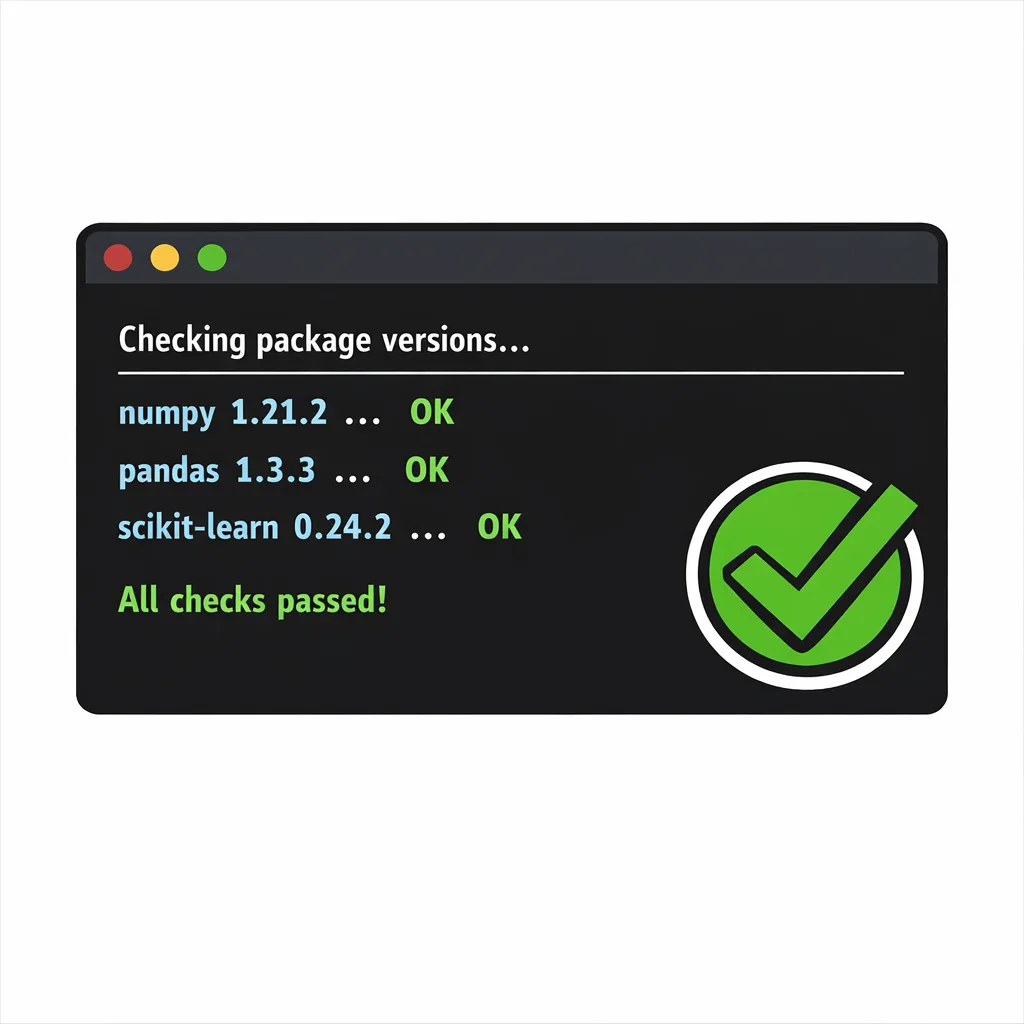
Validate, don’t guess. Run npm ls react react-dom next (or your pnpm/yarn equivalents) in production build images, not just your local dev machine. If you manage a monorepo with multiple apps, verify each deployment artifact.
The 72‑hour patch playbook (works for any size team)
Here’s a pragmatic sequence we’ve used with client teams to move from exposure to a defensible baseline within three days—without blowing up release safety.
1) Inventory what’s actually exposed
Start with the internet-facing list. Pull targets from your CDN/edge config and DNS. For each app or service:
- Label whether it uses Next.js App Router or custom RSC.
- Extract dependency versions from the built artifact (Docker image, serverless bundle, or output of
npm lsinside CI’s build container). - Check for RSC packages:
react-server-dom-webpack,react-server-dom-turbopack,react-server-dom-parcel.
Automate this once. If you’re not producing an SBOM in CI, introduce one now. It pays off the next time a critical CVE drops.
2) Patch to the right micro, rebuild, redeploy
Bump React/Next.js to the patched lines appropriate for your minor. In many repos, the safest path is to advance all the way to the latest micro in your minor (for example, 19.2.3 and 16.0.7), rebuild, and redeploy behind a feature flag or progressive delivery. Avoid partial upgrades that mix patched RSC with unpatched adapters.
After redeploy, verify at runtime: log the exact versions on process start, and expose a health endpoint that returns dependency hashes. It’s mundane, but it turns audits and incident response from guesswork into grep.
3) Add a thin protective layer (it’s not your only defense)
While patches are the fix, a light edge policy helps with resilience:
- Rate-limit RSC endpoints by method and route signature.
- Block obviously malformed Flight payloads and requests with suspicious content-types.
- Alert on responses that match known fingerprint strings and stack traces generated by RSC parsing failures.
Don’t overfit the WAF. The goal is to shave blast radius during the scramble, not to build a perfect signature that breaks on the next patch.
4) Hunt for signs of compromise
Assume some probing happened before your patch. In the last 14–30 days of logs, look for:
- Surges of 5xx on RSC routes or
/_nextserver action endpoints. - Unexpected Node child processes, shell invocations, or outbound connections to uncommon ASNs.
- New cron/systemd timers on hosts that run your Next.js server.
- Modifications to environment variables,
.npmrc, or CI deploy keys.
If anything is fishy, snapshot and preserve evidence before you patch further. Rotate credentials, invalidate tokens, and rebuild fresh images from patched bases.
Should you roll back React Server Components?
It depends on the surface area you’ve exposed and your tolerance for risk while your team stabilizes. If your app uses RSC heavily and you can’t patch immediately (compliance freeze, brittle tests, etc.), consider a temporary bias toward safety:
- Disable Server Actions on the most sensitive routes and refactor to a conventional API controller for a sprint.
- Move a few hot paths back to client components or SSR until your monitoring story around RSC improves.
- Gate RSC features behind a kill switch you can flip without a redeploy.
I’m not advocating abandoning RSC. I’m advocating control. Feature flags plus a rollback plan give you options the next time an exploit starts trending before you finish your patch rollout.
Operational guardrails that pay off in 2026
Use this incident to lock in a better baseline. Here’s a simple framework we recommend across product teams.
1) Prove what’s deployed
Every service should emit its dependency bill of materials and key versions on startup. Store the SBOM artifact from CI alongside the build and attach the hash to your release. When the next advisory drops, you can answer “where are we exposed?” in minutes.
2) Shorten the patch loop
Subscribe CI to security advisories for your primary frameworks. Add dependency bots (Renovate/Dependabot) with auto-merge only for patch-level updates after tests pass. Make “patch Wednesday” a real thing for your org so you’re not negotiating emergency change windows every time.
3) Bound the blast radius
Run apps under least privilege. For Node workloads, deny execution of shells and compilers at runtime unless absolutely necessary. Use read-only file systems and drop capabilities in containers. Keep secrets out of env where possible and rotate them automatically on redeploy.
4) Make your edge smarter
Whether you’re on a CDN, service mesh, or an API gateway, define a thin schema for RSC traffic: expected methods, content types, and payload sizes. Rate-limit by route and client fingerprint. Even a 5–10% reduction in successful probes during a zero-day buys your team time.
5) Drill the IR play
Run a half-day tabletop on a React2Shell-like scenario. Practice artifact capture, rapid patching, secrets rotation, and customer comms. If your last incident retro ended with “we should automate that,” automate it now.
People also ask: quick answers for stressed teams
Is Next.js safe if I never used Server Actions?
Maybe—but don’t rely on memory or intent. If your build includes the affected RSC packages in the vulnerable ranges, you needed the patches. Check your lockfile and the actual production build artifacts. Many teams discovered transitive exposure they didn’t realize they had.
Can a WAF alone stop React2Shell?
No. WAF rules can blunt obvious exploit traffic and reduce noise, but they won’t replace the patched RSC packages. Think of the edge as a seatbelt, not a roll cage.
Do I need to rotate secrets after patching?
If your servers were internet-facing during the exposure window, assume credentials could have been read and rotate them. Prioritize cloud provider keys, database creds, OAuth client secrets, and CI tokens. It’s cheap insurance and it closes a door attackers love to keep open.
A realistic staging plan that won’t break your sprint
Shipping safety fixes during a roadmap push is hard. Here’s a staging plan that balances speed with stability:
- Day 1 morning: patch and rebuild in a branch, run smoke and e2e in CI.
- Day 1 afternoon: deploy to staging plus a small canary environment in prod behind feature flags. Start telemetry diffing between patched and unpatched pods.
- Day 2: widen the canary, rotate secrets for the canary slice only, and review error budgets.
- Day 3: full rollout, delete old images, rotate remaining secrets, and harden edge rules now that you’ve observed real traffic.
Keep the branch alive for a week so you can cherry-pick additional micro updates without repaving your test matrix.
Zooming out: what React2Shell says about modern web stacks
RSC is powerful. It unlocks server-side data fetching and co-location without the hand-rolled API boilerplate. But power surfaces complexity. Expect more scrutiny of the Flight protocol, the ergonomics that make Server Actions feel easy, and the standards conversation around how much runtime behavior a front-end framework should own on the server.
That’s healthy. Our job is to ship products without leaving easy wins to attackers. The teams that win are the ones who pair strong defaults with operational muscle: fast inventory, fast patching, and enough telemetry to know when something’s off.
What to do next (this week)
- Confirm you’re on patched lines: React RSC 19.0.3/19.1.4/19.2.3+, Next.js 15.5.7+ or 16.0.7+.
- Search logs for RSC-triggered 5xx spikes and suspicious child processes during December 3–31.
- Rotate sensitive credentials for any internet-facing app that was exposed.
- Add a health endpoint exposing dependency versions and ship an SBOM from CI.
- Write minimal edge limits for RSC routes and alert on anomalies.
Need a deeper hardening plan?
If you want a structured sprint template, use our 30‑day React2Shell hardening plan as a starting point. For broader guardrails across pipelines and deps, see our software supply chain security playbook. If you’d like help implementing this in your own stack, review what we do for engineering teams and reach out via our contact page. We’ll meet you where your code is—monorepo or multi-repo, serverless or bare metal—and get you to a safer, faster patch posture.

Final take
React2Shell wasn’t a reason to abandon React Server Components. It was a wake-up call to treat RSC as a first-class server surface, patch ruthlessly, and build the muscle to prove and improve what you’ve deployed. Lock in the practices above and the next advisory will feel like a routine patch, not a fire drill.




Comments
Be the first to comment.