React2Shell: A 30‑Day Hardening Plan for 2026
React2Shell is the name given to CVE‑2025‑55182, a critical remote code execution bug in React Server Components (RSC) disclosed on December 3, 2025. It scored a CVSS 10.0, affected default configurations, and was exploited in the wild within days. If you run Next.js with the App Router or any RSC‑capable framework, this is your wake‑up call. Here’s a pragmatic, 30‑day plan that we’ve used with teams to patch fast, prove safety, and harden for 2026.

What actually changed — and what versions fix React2Shell?
The root issue lives in React’s RSC Flight deserialization. The React team shipped fixes on December 3 across the active 19.x lines, then followed up on December 11 with additional patches for two non‑RCE issues found during post‑mortem review. Here’s the short version you can act on today:
- React RSC packages: upgrade to fixed versions in your line — 19.0.1 (and later), 19.1.2 (and later), 19.2.1 (and later). Subsequent follow‑ups for related DoS/source‑exposure issues landed with safe builds 19.0.3 / 19.1.4 / 19.2.3.
- Next.js: upgrade to the latest patched release in your train. If you’re on 15.x or 16.x, move to the latest 15.x/16.x patch. Teams still on 13.x/14.x should follow the vendor guidance to land on the latest 14.2.x or stable 15.x/16.x line before rolling forward.
- If your app was online and unpatched on or before December 4, 2025 at 1:00 PM PT, rotate application secrets. Assume exposure and act accordingly.
Also note two follow‑on CVEs disclosed on December 11, 2025 (a DoS and a source‑exposure bug), plus an addendum patch for an incomplete DoS fix. None of those were RCE, but you should still roll to the latest safe builds listed above.
The React2Shell 30‑Day Hardening Plan
Most teams don’t fail at patching; they fail at sequencing. Use this four‑phase cadence to get from firefight to forward defense without tripping production.
Phase 1 (Days 0–3): Patch and protect
Move fast, but leave an audit trail. Your goals: eliminate RCE risk, buy time with compensating controls, and keep production steady.
- Patch now: bump React RSC packages and your framework (Next.js or equivalent) to their latest patched versions in your current line. Confirm with a lockfile diff and an SBOM scan so you know what actually shipped.
- Rotate secrets if you were exposed: start with cloud credentials, service tokens, webhook signing keys, and database passwords. Treat bearer tokens as burned.
- Add WAF rules and rate limits: deploy managed rules that target the known exploit patterns while you patch lagging services. This won’t save you alone, but it shrinks the window.
- Consider temporarily disabling Server Actions / RSC endpoints on internet‑facing routes if your patch rollout will take more than a day.
If you need a blow‑by‑blow for the first 72 hours, we published a triage‑first walkthrough in React2Shell: Your 72‑Hour Patch‑and‑Prove Plan.
Phase 2 (Days 3–10): Prove you’re clean
Patching ends the vulnerability; it doesn’t erase an intrusion. Use this window to look for footprints, especially if you were publicly reachable before December 4.
- Threat hunting starter list: unexpected Node subprocesses, one‑off reverse shells, miners chewing CPU, new local users, modified
authorized_keys, suspicious outbound DNS, or sudden outbound traffic to tunnel services. Check ephemeral containers and build agents too. - Logs to review: API routes that map to Server Actions, spikes in POSTs with large opaque payloads, and short bursts of 500s around your RSC handlers. Don’t ignore a brief DoS‑style CPU plateau—it may have been a crude probe.
- SBOM and dependency attestation: regenerate an SBOM for each service post‑patch. Validate that your container images include the fixed RSC packages and not just an updated top‑level
react. - CI hygiene: verify that any GitHub Actions or scanners you pulled down to "check for React2Shell" are legitimate. A few fake scanners popped up that were themselves malware. Only run vetted tools.
Phase 3 (Days 10–21): Fortify the boundary
React Server Components blur the line between UI and server execution. Treat that boundary like an API, not a convenience feature.
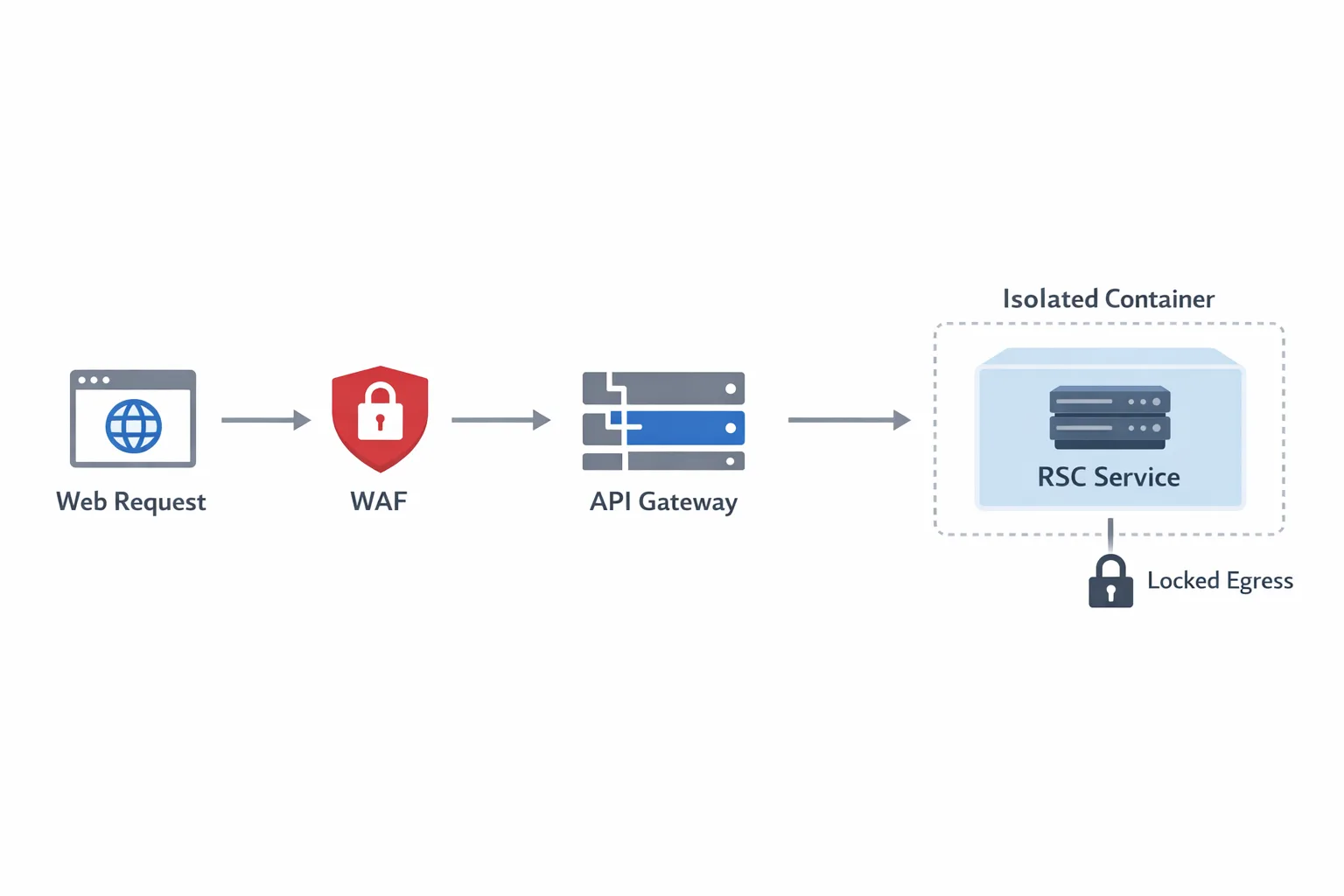
- Constrain ingress: route RSC traffic through a reverse proxy with request size limits, sane timeouts, and anomaly detection. Put your API gateway’s schema validation in front of RSC endpoints where possible.
- Reduce blast radius: run RSC handling in its own process or container with a tight AppArmor/SELinux profile, read‑only root FS, no shell, and least‑privileged IAM. Egress‑deny by default; open only what you need.
- Separate secrets: put signing keys and critical credentials behind short‑lived, workload‑bound identities. Prefer workload identity federation over long‑lived keys.
- Observability you’ll actually read: add explicit counters and spans for RSC deserialization, payload size, and error types. Alert on abnormal POST size to RSC routes.
Phase 4 (Days 21–30): Make it routine
You’re past the crisis. Now make sure the next one is boring.
- Automated patch trains: enable Dependabot/Renovate for app and Docker base images. Ship weekly, not quarterly.
- Lifecycle policy: codify “patch within 24 hours for RCE, 7 days for high, 30 for medium.” Measure it.
- Pre‑prod kill switch: feature‑flag RSC endpoints so you can turn them off globally while a patch bakes.
- Security review for RSC usage: add a design checklist to any PR that introduces Server Actions or new server functions.
The 10‑minute vulnerability check
Need to know if you’re still exposed? Here’s a quick, no‑frills approach that works across most CI environments.
- List your RSC packages: run
npm ls react-server-dom-webpack react-server-dom-parcel react-server-dom-turbopack next(or your framework equivalents). Confirm versions are at or beyond the patched releases in your line. - Check your lockfile: search
package-lock.jsonorpnpm-lock.yamlfor the vulnerable versions (19.0.0, 19.1.0–19.1.1, 19.2.0). - Build an SBOM: use
cyclonedx-npmor your preferred tool and stash it in artifacts with the release. - Smoke test: send a small POST to a known Server Action route and confirm you’re not seeing unbounded CPU spikes or serialization errors. Keep this in pre‑prod only.
Architecture guardrails for RSC in 2026
RSC is powerful, but power needs boundaries. Treat it like you would a private RPC system exposed at the edge.
- Define the trust boundary: anything deserialized by your server is untrusted until validated. Wrap RSC calls behind explicit server‑side
zod/valibotvalidation where practical, even if the transport is “internal.” - Constrain the surface: avoid catch‑all handlers that share process space with sensitive work. Split critical jobs (payments, user management) into isolated services with narrow APIs.
- Watch the blast radius of dynamic code: avoid patterns that reflect user‑controlled structure into server evaluation, even indirectly. Prefer declarative data over executable shapes.
- Instrument for the next time: keep per‑route payload size histograms and outlier detection. Make it easy to turn up sampling on RSC routes without redeploying.
People also ask
Am I vulnerable if I don’t use Server Actions?
Possibly. If your app supports React Server Components, you could still have reachable server function endpoints via framework defaults or plugins. Don’t assume “we don’t use actions” equals “we’re safe.” Verify your installed packages and framework behavior, and patch regardless.
Which versions fix React2Shell?
React’s RSC packages were fixed with 19.0.1 / 19.1.2 / 19.2.1 and later, then followed by additional non‑RCE fixes that leave 19.0.3 / 19.1.4 / 19.2.3 as safe roll‑ups as of mid‑December 2025. Next.js shipped patched builds across maintained trains; update to the latest in your line (15.x/16.x users: take the newest patch; 13/14 users: move to a supported patched release).
Do I need to rotate secrets?
If your app was publicly reachable and unpatched before December 4, 2025 at 1:00 PM PT, yes—assume exposure and rotate. Start with cloud provider credentials, JWT signing keys, webhook secrets, and database credentials. Track rotations with change tickets; don’t rely on memory.
How do I know if we were exploited?
Look for unusual outbound connections from your web tier, unexpected node child processes, new local users, modified SSH keys, or sudden CPU spikes around RSC routes. If you find anything suspicious, trigger incident response and preserve evidence before you clean.
A practical checklist you can copy
Here’s a compact list we drop into client runbooks.
- Inventory: enumerate all services using React/Next.js or any RSC plugin; tag internet‑facing first.
- Patch: update to fixed versions; confirm via lockfile diff and SBOM.
- Protect: enable WAF rules and tighten reverse proxy limits.
- Prove: hunt for IOCs, rotate secrets, and snapshot logs/artifacts.
- Partition: isolate RSC handling to a low‑privilege process/container.
- Policy: codify RCE SLA (24h), high (7d), medium (30d) and enforce.
- Pipeline: automate dependency updates and add pre‑prod kill switches.
For Next.js teams: a few gotchas
Next.js App Router apps inherit RSC behavior. When you upgrade, watch for three common tripping points:
- Partial upgrades: updating
reactwithout bumpingreact-server-dom-*ornextcan leave you vulnerable. Always check transitive versions pulled in by your framework. - Canary mismatches: if you’re on a canary build from late 14.x/early 15.x, follow the vendor path back to a patched stable release before rolling forward.
- Runtime drift: container layers and build runners cache aggressively. Rebuild from a clean base image and purge the package manager cache to ensure patched artifacts make it into production images.
If you’re planning a broader upgrade to stabilize your stack, our guide to Next.js 16 + React 19 in 30 days covers parallel upgrade lanes and rollback design.
When mitigation beats patch speed
Some estates can’t patch everything in 24 hours. If you’re juggling legacy modules or audit windows, treat this like any other edge‑exposed RCE: segment, filter, and watch.
- Network shape: put an API gateway in front of any RSC‑capable app. Enforce mTLS for east‑west traffic where possible.
- Egress policy: deny by default from web tier containers; allow only the specific domains you need. It turns RCE into a dead end.
- Runtime controls: run with a read‑only filesystem, disable shell, and set
NODE_OPTIONS=--no-addonsif you don’t rely on native addons. - Quarantine lane: if you suspect compromise, fork traffic to a clean deployment and keep the suspect node online for forensics instead of instantly redeploying over evidence.
What about “we don’t use React Server Components”?
I’ve heard this a dozen times this month, and half the time it wasn’t true. Framework defaults enable features you didn’t explicitly ask for. Validate the installed package graph and what your framework exposes by default. If RSC packages are present, patch them even if you think you’re not using them.
What to do next
- Ship the patches today, confirm with SBOMs, and rotate secrets if you were exposed before December 4, 2025 1:00 PM PT.
- Run the 10‑minute check across all services and set alerts on RSC payload anomalies.
- Plan a one‑sprint hardening pass: isolate RSC handling, add gateway validation, and lock down egress.
- Formalize your RCE response SLA and automate weekly dependency updates.
- If you need help, our team has shipped multiple React2Shell remediations across regulated environments—see our portfolio highlights and reach out via Bybowu contacts.
Zooming out
React Server Components aren’t going away, and for good reason—they unlock serious UX wins. But they also introduce a new class of edge‑adjacent risk that deserves first‑class architecture. Patch today, prove you’re clean, and then constrain the boundary so the next CVE is just another Tuesday. For more on the moving policy and platform backdrop shaping your 2026 roadmap, keep an eye on our engineering blog and our breakdowns like What Broke, What’s Fixed, What to Do Now.






Comments
Be the first to comment.