Your 48‑Hour Node.js Security Release Playbook
If you run production on Node, the latest Node.js security release isn’t optional reading—it’s a shipping decision. On January 13, 2026, the project shipped updates for 20.x, 22.x, 24.x, and 25.x addressing 3 high, 4 medium, and 1 low severity issues, alongside dependency bumps to c‑ares 1.34.6 and undici 6.23.0/7.18.0. Downloads listed 20.20.0, 22.22.0, 24.13.0, and 25.3.0. (nodejs.org)
Here’s the thing: patches reduce risk only after you roll them out—safely. This field guide walks you through what changed technically, where teams are likely exposed, and a pragmatic 48‑hour plan to patch, test, and push without drama.
What changed in this Node.js security release?
Start with scope. The project’s advisory documents the CVEs, affected lines, and the bundled dependency updates. The big items you’ll care about in production include:
• Timeout‑based race condition where Buffer.alloc() or typed arrays can appear non‑zero‑filled under certain timing conditions, risking exposure of uninitialized memory (CVE‑2025‑55131; high). Affects all active lines (20/22/24/25). (nodejs.org)
• Permission Model symlink traversal that can break filesystem isolation and allow file read/write outside approved paths (CVE‑2025‑55130; high). Affects users of --permission on 20/22/24/25. (nodejs.org)
• HTTP/2 HEADERS handling can crash servers with malformed frames (CVE‑2025‑59465; high). If your TLS stack lacks robust error handlers, a remote DoS is on the table. (nodejs.org)
• TLS client‑certificate parsing memory leak that can be triggered when iterating X.509 fields via socket.getPeerCertificate(true) (CVE‑2025‑59464; medium). Noted as already fixed in 24.12.0 but documented for awareness in the advisory. (nodejs.org)
• Permission Model network bypass via Unix Domain Sockets on 25.x (CVE‑2026‑21636; medium). The advisory calls out that --allow-net is still experimental, but the bypass matters if you rely on permission boundaries. (nodejs.org)
On dependencies, c‑ares 1.34.6 is a security release that fixes CVE‑2025‑62408, a bug in query termination that could enable DoS. If your stack performs lots of DNS lookups under load, this matters for availability. (c-ares.org)
Undici updates shipped as 6.23.0 and 7.18.0 within Node. Snyk notes a resource‑exhaustion issue mitigated in 6.23.0 and 7.18.2; stay current if you pin Undici directly in userland. (nodejs.org)
Why these issues matter in production
Zero‑fill assumptions are everywhere—buffer reuse in parsers, crypto payloads, uploaded file chunks. If uninitialized memory bleeds into serialization or logs, you’ll leak secrets you didn’t even store. The permission model bugs land where teams reach for stricter sandboxing in CI or multi‑tenant worker hosts—precisely the places you expect isolation to hold. And if you terminate TLS with Node and request client certs, the memory leak is a slow DoS waiting for a loop.
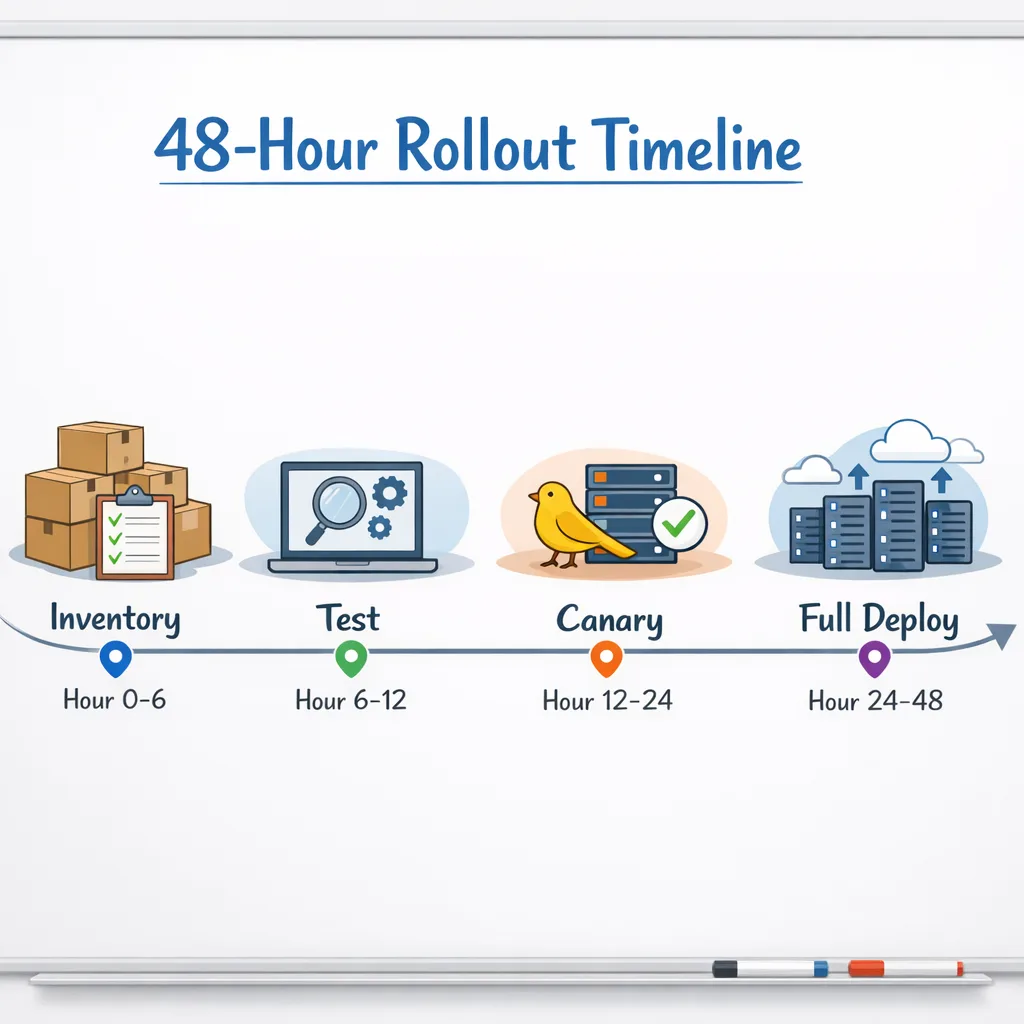
The 48‑hour response plan
This is the playbook I run with clients when a drop like this hits. It assumes you own at least one customer‑facing service and you deploy multiple times per week.
Hour 0–2: Inventory and blast radius
• Enumerate all Node runtimes in prod and pre‑prod: container images, serverless functions, workers, cron boxes, and CI runners. Capture major/minor versions and whether --permission is enabled anywhere.
• Identify services with: HTTP/2 enabled, mTLS or client cert inspection, heavy DNS usage (service discovery, outbound APIs), and any code paths that return raw buffers or typed arrays.
• Note direct Undici pins in package.json. If you’re on Undici 7.x outside of Node’s built‑in, check whether you’re on ≥7.18.2; if not, plan a bump. (security.snyk.io)
Hour 2–8: Decide versions and freeze
• For each release line in use, target the patched tags: 20.20.0, 22.22.0, 24.13.0, or 25.3.0 according to the advisory. Lock them in your base image or runtime profile before you touch application code. (nodejs.org)
• Soft‑freeze non‑essential merges. Keep the diff small so test signals are about the upgrade, not features.
Hour 8–20: Focused test passes
Don’t spray generic regression tests at this. Aim at the known failure modes and the real attack surface.
• Memory safety: Add a unit test that allocates a zero‑filled buffer and validates contents under load. For example, run Buffer.alloc(1_000_000), slice/serialize, and confirm zeros only. Loop it with a time budget to mimic timing quirks. (nodejs.org)
• HTTP/2 crash: Spin a canary with HTTP/2 enabled and hammer it with malformed header frames using a test client. Validate that error handlers catch and close sockets—not crash the process. (nodejs.org)
• Permission model: With --permission active, attempt to read/write via a relative symlink that points outside your allowed path. The operation should now be blocked. Also verify that UDS connections can’t bypass --allow-net on 25.x. (nodejs.org)
• TLS client certs: If you call socket.getPeerCertificate(true), soak‑test with repeated connections and watch memory. Expect flat usage post‑patch on 24.x and newer. (nodejs.org)
• DNS stress: If you run service discovery or lots of outbound calls, run a load test that amplifies DNS churn to ensure no regressions with c‑ares 1.34.6. (c-ares.org)
Hour 20–32: Staged rollouts
• Roll to 5–10% of traffic first. Enable elevated logging around TLS, HTTP/2, DNS, and file I/O errors.
• Watch for outliers: latency spikes on upstream calls (Undici bump), increased 5xx rates on H2 endpoints, memory drift on TLS‑heavy services, or unexpected permission denials in sandboxed jobs.
• If you run a monorepo, promote the base image change and version matrix updates across packages in a single PR to avoid inconsistent runtime drift.
Hour 32–48: Full rollout and retro
• Promote to 100% and confirm golden dashboards return to baseline.
• Document where you rely on the permission model. Today’s network check gaps were labeled experimental—the signal is to avoid assuming strong isolation guarantees until flags graduate from experimental. (nodejs.org)
People also ask
Which versions are affected and which should I install?
The advisory lists patches for all active lines: 20.20.0, 22.22.0, 24.13.0, and 25.3.0. If you’re on any earlier 20/22/24/25 build, you’re affected by at least the high‑severity CVEs. Upgrade to the matching patched line—don’t jump majors during a security fix unless you’ve planned for it. (nodejs.org)
Do I need to rebuild native modules?
These are patch/minor releases within each major; ABI compatibility usually holds. Still, if you ship native extensions or older N‑API bindings, run a clean rebuild in CI and verify prebuild availability for alpine/musl if you use it in containers. Focus on runtime tests rather than only type checks.
What about undici and c‑ares—do those changes break anything?
Node bundled updated undici and c‑ares to address public vulnerabilities. If your app directly pins undici, check whether you’re on ≥6.23.0 or ≥7.18.2 to incorporate the decompression chain hardening. For DNS‑heavy systems, the c‑ares 1.34.6 security release reduces DoS risk during query termination. Validate with load. (nodejs.org)
Is there anything else on the crypto side I should watch?
Yes—keep an eye on OpenSSL advisories and how they flow into your distributions and Node images. For example, OpenSSL posted updates on January 27, 2026 with fixes across supported branches; you’ll want those once they land in your base images even if Node doesn’t bump immediately. (openwall.com)
Test focus: practical checks you can run today
Here are lean tests I’ve used in real patch windows to catch the unexpected:
• Buffer hygiene: run an integration test that allocates and returns a zero‑filled payload from a private endpoint. Add chaos timing by mixing CPU‑heavy and I/O‑heavy tasks in the same process to tease out race windows. The response must contain only zeros. (nodejs.org)
• H2 hardening: inject malformed headers via a controlled client (or fuzz harness) and confirm your server handles the error path and stays up. Log handler paths explicitly so you don’t mistake socket resets for process crashes. (nodejs.org)
• Permission model staging: mount a read‑only directory and attempt fs.futimes() to validate that timestamp updates are blocked under permissions (CVE‑2025‑55132). Also test symlinks and UDS behavior as described above. (nodejs.org)
• TLS soak: if you read peer cert fields, push 10–30k short‑lived TLS connections against a staging service and capture heap usage over time to confirm no leak signal post‑patch on 24.x+. (nodejs.org)
Rollout patterns for monoliths and microservices
Monoliths: bake a single base image with the patched Node version, run targeted tests, deploy behind feature flags for any behavior‑touching changes (e.g., stricter permission checks). The upside is speed; the risk is a wide blast radius if you miss a test.
Microservices: upgrade the shared base image first, then promote per‑service builds. Prioritize edge‑facing services (API gateway, auth, payments) and internal gateways that terminate TLS or front HTTP/2. Accept a day or two of mixed Node versions during rollout; consistency is less important than eliminating the biggest risks first.
Operational guardrails to keep
• A small, boring Node version matrix. Two LTS lines max in prod. Anything older moves to a retirement track.
• Alerting that understands the difference between process crashes and graceful connection resets.
• A documented position on the Permission Model: it’s a helpful guardrail when used deliberately, not a full sandbox. Treat “experimental” flags like “best‑effort,” not guarantees. (nodejs.org)
Zooming out: why this pace of security patches is normal
Node ships on top of a stack (V8, OpenSSL, c‑ares, Undici). The advisory itself names c‑ares and Undici versions updated in response to public vulnerabilities, and the community CVE feeds corroborate the specific Node issues. This cadence is what a mature ecosystem looks like: fast disclosure, specific fixes, and patched artifacts for all supported lines. The job for your team is to make upgrades safe and routine. (nodejs.org)
What to do next
• Upgrade runtime: move services to 20.20.0, 22.22.0, 24.13.0, or 25.3.0 today. Lock the base image. (nodejs.org)
• Run targeted tests: buffers, HTTP/2 error paths, TLS client cert parsing, permission model checks, and DNS load. (nodejs.org)
• Evaluate Undici: if you pin it directly, bump to a version with the decompression chain fix (≥6.23.0 or ≥7.18.2). (security.snyk.io)
• Track OpenSSL: subscribe to your distro’s security notices and rebuild base images when 3.x updates drop. (openwall.com)
• Write the retro: list what made this upgrade slow and remove one friction point before the next release.
Want help pressure‑testing your rollout?
If you need a second set of eyes, our team ships Node upgrades for regulated and high‑traffic stacks. Start with the quick reads—our breakdowns on what to patch first and a ship‑fast playbook—then reach out via Bybowu Contacts. If you’re building a longer‑term program, our test‑smarter guide shows how to make these windows dull, fast, and safe.
FAQ for execs and PMs
• Are we exposed? If you’re on the affected lines and handle HTTP/2, TLS client certs, or rely on Node’s Permission Model, yes—until you patch. (nodejs.org)
• Will there be downtime? Not if you stage correctly. Canary, monitor, then promote.
• Why do we patch when nothing looks broken? Because today’s issues include crash and data‑exposure classes. The point of patching is to remove unknowns before attackers or traffic spikes find them. (nodejs.org)

Security releases aren’t emergencies when you’re ready for them. Treat this one as a rehearsal: tighten your inventory, write the minimum viable tests for the vulnerabilities at hand, and keep your base images boring and current. Ship it.





Comments
Be the first to comment.