Third‑Party Cookies in Chrome: 2026 Playbook
Let’s get straight to it: Google kept third-party cookies in Chrome. If you paused migrations waiting for clarity, you’ve got it now—and you still have work to do. Chrome won’t remove third‑party cookies, and the UK regulator has stepped back from day‑to‑day oversight after Google’s reversal. But privacy constraints aren’t going away: Incognito IP Protection, stricter consent expectations, and platform policy shifts are reshaping how we track and optimize growth in 2026. (developers.google.com)

What actually changed—and when
On April 2025, Google said it would not introduce a new user choice prompt nor deprecate cookies in Chrome. That ended years of Privacy Sandbox roadmapping around a hard cutoff. The CMA then released Google from the old Privacy Sandbox commitments on October 17, 2025, noting the competition concerns no longer applied given Google’s change of course. Translation: no forced cookie turndown from Chrome, no regulatory guardrails governing that plan. (arstechnica.com)
Google’s own developer guidance now states plainly that third‑party cookies are “no longer being deprecated.” If you only read one line today, make it that one. (developers.google.com)
However, Chrome is not static. Google has been preparing IP Protection for Incognito browsing—a two‑hop proxy that masks user IPs for third‑party requests in private sessions, with enterprise controls and regional rollouts. The project’s docs and Q&A clarify scope (Incognito only), sign‑in requirements, and the masked domain list approach. That’s real, and it affects attribution, fraud rules, and geo logic. (github.com)
Third‑party cookies in Chrome: what it means for measurement
Because cookies persist, many ad stacks will continue to “work.” But a 2026‑ready plan accepts three realities:
First, cookie reliability is inconsistent across browsers and modes (Safari’s ITP, Firefox ETP, enterprise policies, and Incognito). Second, privacy features now target other identifiers such as IP. Third, regulators and platforms still expect demonstrable user choice. You can’t bank your pipeline on Chrome alone.
The upshot: keep your cookie‑based workflows, but harden them with consent‑aware first‑party data, server‑side collection, and model‑friendly event quality. If you’re still pure client‑side and cookie‑centric, the gaps will show up in CAC volatility, remarketing reach, and multi‑touch models the moment your audience steps out of standard Chrome sessions.
The 2026 measurement stack I recommend shipping
Here’s the stack we deploy for clients who need CFO‑grade numbers and GC‑grade compliance without slowing release velocity.
1) A consent‑first data layer, not a tag salad
Unify events behind a typed data layer (think event, user, context, consent objects). Use a Consent Management Platform that can write normalized consent states your tags and server endpoints actually read. If you’re in React, formalize this during your app upgrade cycles—see our migration notes in React 19 shipping guidance to keep instrumentation from rotting during refactors.
2) Server‑side tagging as the default
Move network‑sensitive work off the browser. Whether you use GTM Server, Segment/Amp, RudderStack, or a bespoke Node/Edge worker, the goal is stable, auditable delivery and the ability to enrich with first‑party context. You’ll get fewer blocked calls, better latency profiles, and cleaner retry semantics. If you manage your own Node runtime, keep pace with security releases—our quick triage guide on what to patch today is a handy checklist.
3) First‑party identity that survives the basics
Implement durable user keys: account IDs, hashed emails on auth, or CRM IDs—stored lawfully and only sent when consented. For non‑auth traffic, use event‑scoped pseudonymous IDs with short TTLs, rotated frequently. Avoid “re‑identification” joins that your legal team can’t defend.
4) Event quality over event quantity
Define a standard taxonomy—view_item, add_to_cart, begin_checkout, purchase, plus the two or three funnel moments that are truly predictive in your domain. Log the minimum fields that make models work (value, currency, content IDs, campaign/creative, geo, device, consent). Resist the urge to “collect it all.”
5) Attribution that’s resilient, not omniscient
Expect less cross‑mode determinism. Use last‑non‑direct for ops reporting, but audit quarterly against a modeled view (data‑driven or Markov) and media‑mix experiments. Where your ad platforms support it, feed back server‑verified conversions with consent flags so algorithms don’t overlearn on noisy events.
6) GA4 plus a warehouse you actually query
GA4 remains a solid UI layer for marketers, but your truth should live in BigQuery, Snowflake, or Redshift with dbt‑managed transforms. Build daily freshness checks and null‑rate monitors to catch consent drift or broken client payloads.
7) A privacy posture you can demo
Store evidence of consent at the event level, show a log of suppression decisions, and document how IP, UA, and other identifiers are handled—especially for Incognito sessions where IP masking may apply. Your regulator, your partners, and increasingly your enterprise customers will ask. (github.com)
But didn’t Google end the Privacy Sandbox?
Google’s April 2025 move ended the plan to remove cookies and the proposed user choice prompt. Reporting at the time described Sandbox APIs as having a “different role” going forward. Practically, adoption remains limited across advertisers, and most growth teams don’t depend on Topics or Protected Audience today. If you’ve invested, keep it—just don’t make it your single point of failure. (arstechnica.com)
Here’s the thing: even without a cookie cutoff, Chrome will keep shipping privacy features (like Incognito IP masking). Your strategy should assume variability by browser, mode, and region—and abstract those differences away in your architecture. (github.com)
Incognito IP Protection: the hidden multiplier on tracking loss
Incognito already blocks third‑party cookies by default. With IP Protection, third‑party requests in Incognito route through a two‑hop proxy so embedded resources no longer see the user’s real IP. That undercuts geo targeting, coarse deduping, fraud‑prevention logic, and any model that leans on IP as a backstop. Enterprises can manage the feature; consumer rollout is region‑based. Plan for mixed reality. (privacysandbox.google.com)
What breaks in practice? Remarketing pools shrink for users who research privately. City‑level performance swings as more Incognito traffic appears to come from proxy locations. And basic bot rules that rely on IP repetition fail more often—expect to tighten device‑level and behavioral signals or plug in a proper risk engine. (privacysandbox.google.com)
A practical 9‑step checklist to ship this quarter
- Stand up a unified data layer with explicit consent states (
ad_storage,analytics_storage, and custom scopes). Tie it to your CMP and document fallbacks. - Move your highest‑value conversion events to a server endpoint you control. Keep client stubs minimal and resilient.
- Normalize user identifiers: authenticated IDs when present; short‑lived pseudonymous IDs otherwise. Don’t leak identifiers cross‑domain.
- Instrument GA4 and your ad platforms from the server; pass consent and country in payloads. Turn on channel‑specific conversion diagnostics.
- Set up a warehouse feed and dbt jobs for attribution, LTV, and cohorting; publish a weekly “measurement health” report that flags nulls, spikes, and consent mismatches.
- Harden fraud and abuse logic without IP: device signals, velocity checks, WebAuthn usage, and merchant‑defined risk rules.
- Run a 6‑week geo experiment: split markets or inventory classes to validate modeled attribution against MMM or uplift baselines.
- Draft an Incognito policy: what you infer, what you suppress, and how you respect user intent. Align with legal and update your privacy notice.
- Train your media team to read modeled paths and not over‑rotate on last‑click—especially where private browsing rates are high.
People also ask
Do I still need a CMP now that cookies remain?
Yes. Chrome’s stance doesn’t change your obligation to honor user choice and regional laws. A CMP gives you audit trails, granular scopes, and a consistent signal to pass downstream. It’s the difference between “we think we comply” and provable compliance.
Will GA4 “lose” more data in Incognito with IP Protection?
You’ll see more anonymized or proxy‑sourced traffic and less reliable geo/device joins for private sessions. That’s expected. The remedy is better server‑side collection with consent, plus modeled attribution that doesn’t assume IP determinism. (privacysandbox.google.com)
Is server‑side tagging really necessary now?
If you care about stability, yes. Client calls are easiest to block, throttle, or reshape by browser modes and extensions. Server‑side lets you control retries, enrich legally, and keep a clean separation between consented data and everything else.
What about Safari and Firefox?
They never promised cookie continuity. If your plan only works in standard Chrome, you don’t have a plan. Build for variability; measure like a skeptic.
Data points you can take to your next planning meeting
- April 2025: Google dropped the cookie deprecation plan and the new user choice prompt for Chrome. (arstechnica.com)
- October 17, 2025: The UK CMA released Google from Privacy Sandbox commitments after that reversal. (gov.uk)
- IP Protection: designed for Incognito sessions; sign‑in required; enterprise‑managed Chrome can control it; rollout tied to regions and a masked domain list. (github.com)
Let’s get practical: reference implementation sketch
Picture a Next.js storefront and a Go or Node edge API. You emit a minimal client signal (purchase with amount, currency, content_ids, consent). The browser sends this to your own endpoint. The endpoint validates consent, attaches first‑party context (logged‑in user ID if present), signs the payload, and forwards to your analytics and ad endpoints. For Incognito sessions, you’ll still get the event—but you won’t rely on IP for dedupe or geo. Instead, you use order IDs and device heuristics and resolve geo server‑side via payment data where lawful.
We’ve shipped variants of this stack across ecommerce and subscription apps. If you want a deeper walkthrough of how we instrument modern web apps without breakage during framework upgrades, start with our React 19 migration playbook, then explore how our services package server‑side tagging, consent, and analytics QA into a single sprint.
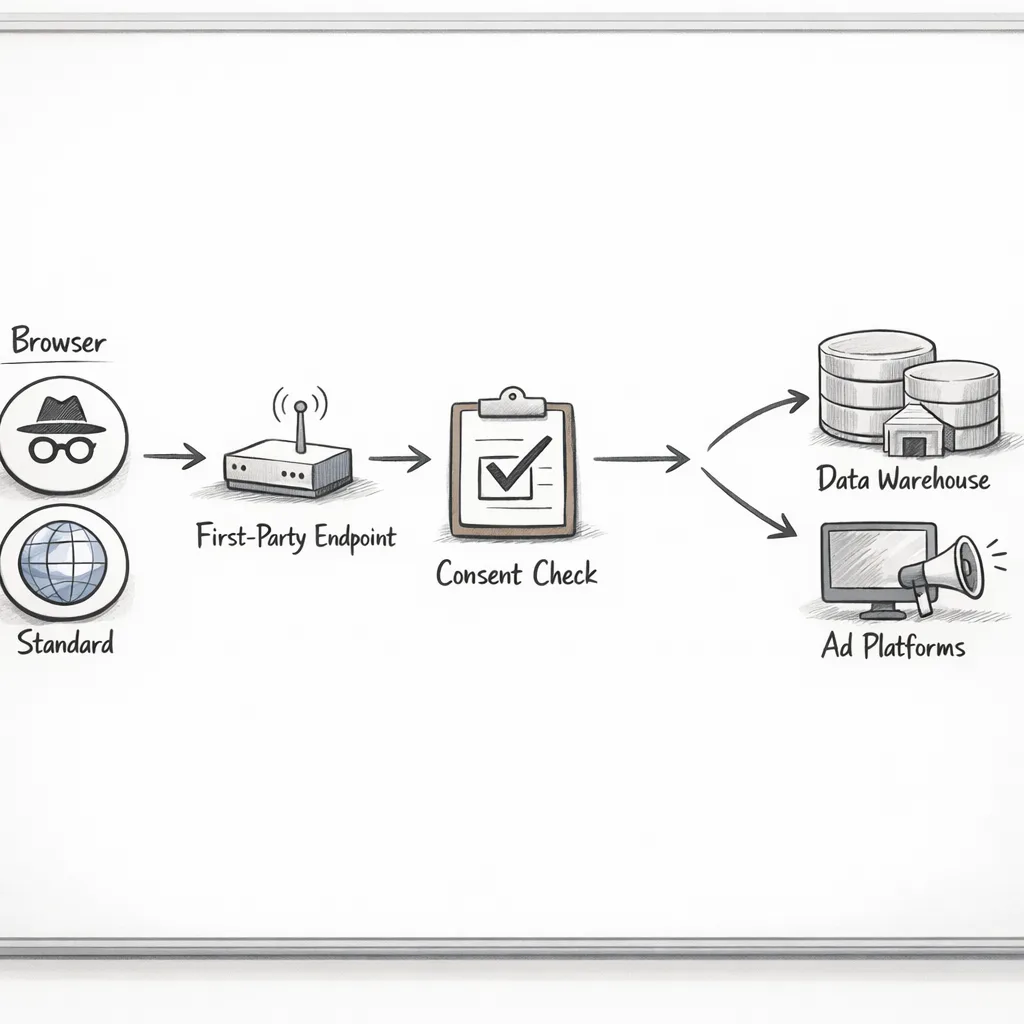
Risks, tradeoffs, edge cases
Two big ones. First, server‑side tagging can centralize risk. If your endpoint goes dark, you lose visibility across channels at once. Mitigate with multi‑region failover and backpressure limits. Second, consent drift: if your CMP config changes and your endpoint ignores it for a week, you’ll contaminate datasets and potentially breach policy. Automate parity checks between the CMP and your event schemas.
Edge cases worth testing: VAT‑inclusive pricing and currency rounding at the edge; guest checkout IDs colliding across subdomains; and referral spam filtering without IP. Build fixtures and replay logs so you can reproduce issues without guessing.
Zooming out: strategy, not whiplash
The last few years pushed teams into reactive roadmaps. 2026 is the year you stop swapping trackers and start building a measured system that survives browser shifts. Keep the cookies; earn first‑party trust; move the network to your side of the glass; and plan for private sessions to behave differently. If that sounds like the boring answer, good—boring is what actually scales. For help scoping or auditing your stack, see what we do on What We Do or start a conversation via Contacts.
What to do next (this week)
- Inventory your events, consent flags, and destinations; cut noisy fields.
- Stand up a minimal server‑side endpoint for your top conversion.
- Add a nightly report that compares client vs. server counts by channel.
- Draft and publish your Incognito/IP Protection handling policy.
- Plan a 60‑day media test to validate modeled attribution.
If you want more industry context as you plan, our blog tracks the platform changes that actually move budgets—without the fluff.




Comments
Be the first to comment.