Third-Party Cookies in 2026: Your Realistic Plan
If you planned your year around third-party cookies disappearing, take a breath. Third-party cookies remain in Chrome, and they’re not scheduled for blanket deprecation. But that doesn’t mean you can keep operating like it’s 2019. Safari has blocked them by default for years, Firefox blocks known third‑party trackers by default, and Chrome continues to roll out privacy protections that limit cross‑site tracking in practical ways. The question isn’t “Are third‑party cookies dead?” It’s “How do we build a durable 2026 plan that works across browsers and still hits target CPA?”
What changed—and what didn’t
Let’s get the timeline straight, because strategy depends on the details. In July 2024, Google said it would not deprecate third‑party cookies in general Chrome browsing and instead pursue a user‑choice approach. In April 2025, it also opted against introducing a separate third‑party cookie prompt. By October 17, 2025, the UK’s Competition and Markets Authority formally released Google from the Privacy Sandbox commitments it had been overseeing. That sequence matters: the immediate threat of a “hard cutoff” in Chrome receded, but the broader shift toward privacy‑preserving measurement did not reverse.
Meanwhile, the rest of the ecosystem kept moving. Safari fully blocks third‑party cookies by default and relies on the Storage Access API for specific, user‑mediated exceptions. Firefox’s Enhanced Tracking Protection blocks known third‑party tracking cookies for everyone by default. Chrome continues to improve privacy controls and is investing in features that reduce passive tracking vectors, especially in private browsing modes. If your acquisition and retention plans quietly assume Chrome third‑party cookies will always save the day, you’re one feature flag away from a measurement blackout on a big chunk of traffic.
Third-party cookies: what this actually means for measurement
Here’s the thing: “Cookies are still in Chrome” is not the same as “Your measurement is fine.” Cross‑site cookies are already unreliable on a significant share of sessions, and they’re the first thing users, extensions, and IT policies disable. On the open web, you should assume:
- Safari and Firefox sessions won’t support third‑party cookie flows for attribution or personalization.
- Chrome users can increasingly restrict cross‑site tracking, and private browsing will limit additional signals (including IP‑based techniques) when enabled.
- Regulatory pressure (EEA, UK, and many U.S. states) keeps pushing toward explicit consent, data minimization, and clearer purpose limitations.
If your bid strategies, frequency capping, and LTV models rely on third‑party IDs across sites, your numbers are already skewed. That’s why the winning 2026 plan is “Chrome‑compatible but browser‑independent.”
People also ask: Are third‑party cookies going away in 2026?
No official date exists for Chrome to remove them in general browsing, and the last two years made a universal cutoff unlikely. Still, you should operate as if cross‑site cookies are a minority capability: design for first‑party identity, consent‑aware data collection, and server‑validated events that work the same in Safari and Firefox.
Do I still need a cookieless plan if Chrome keeps cookies?
Yes. Your traffic mix isn’t 100% Chrome, audiences increasingly browse in stricter modes, and platform algorithms (ads and anti‑fraud) reward clear, high‑fidelity first‑party signals. A cookieless plan is now just a modern plan.
What breaks without third‑party cookies today?
Common breakpoints include cross‑site SSO iframes, embedded checkout widgets that set session cookies from a different domain, legacy remarketing tags, and frequency capping that relies on a third‑party ID. You’ll also see skewed last‑click attribution because some browsers simply won’t hand the data over.
The 2026 blueprint (even if Chrome keeps cookies)
Over the past year, we’ve guided teams through a six‑layer migration that de‑risks performance without boiling the ocean. Use this as your starting point and adapt to your stack:
- Policy & consent first. Map purposes (measurement, personalization, ads) to consent categories. Block non‑essential tags until consent. Honor revocation and regional rules. If you run EEA traffic, support consent signals publishers and ad platforms actually read.
- First‑party identity. Stabilize user recognition with your own domain and storage. Use secure, short‑lived first‑party cookies tied to server sessions. Where appropriate and permitted, implement login incentives and preference centers that create value for the user, not just the marketer.
- Server‑side tagging. Move critical event collection to a server endpoint you control. Validate and enrich events (e.g., campaign params, geo) and forward to destinations. This mitigates ad‑blockers, reduces client bloat, and gives you governance levers you’ve never had in the browser.
- Durable attribution. Combine consented first‑party events with modeled conversions, post‑purchase surveys, and media mix modeling. Don’t chase perfect person‑level tracking; aim for directional confidence that updates quickly enough for bidding systems.
- Creative and audience systems. Shift spend toward contexts and high‑intent supply where cookie‑level IDs matter less. Build remarketing lists primarily from your first‑party graph, not third‑party pixels.
- Resilience testing. Regularly emulate Safari/Firefox conditions, private browsing, and stricter Chrome settings. Ship only what works under those constraints.
If you want a partner who’s done this before, our team can scope, implement, and validate the whole stack—from consent orchestration to server‑side pipelines. See what we do and how we connect strategy to engineering sprints.
Let’s get practical: the migration checklist
Use this as an implementation worksheet with your analytics, martech, and engineering leads. Expect two or three sprints for a well‑maintained stack; more if you’re untangling duplicated tags across properties.
- Consent and governance: Define purposes, map tags to purposes, block until consent. Log consent decisions server‑side for audits. Provide region‑specific flows.
- Data collection: Deploy a first‑party endpoint for browser events. Support signed, time‑boxed identifiers and rotate keys. Normalize event names and parameters across web/app.
- Attribution inputs: Ensure UTM hygiene. Preserve landing‑page parameters through redirects. Capture server‑validated purchase events with campaign context and consent flags.
- Destinations: Route server‑side to analytics, ad platforms, and warehouses. Strip prohibited fields. Respect each destination’s consent requirements.
- QA and monitoring: Build synthetic journeys for Chrome default, Chrome private, Safari, and Firefox. Monitor event loss, latency, and destination acceptance rates.
On the engineering side, pair this with a modern frontend plan—fewer client scripts, deferred tag loading, and a component‑driven UI on the latest stable framework. If you’re overdue, our Next.js 16 + React 19 upgrade playbook shows how to tighten performance and security while you refactor analytics.
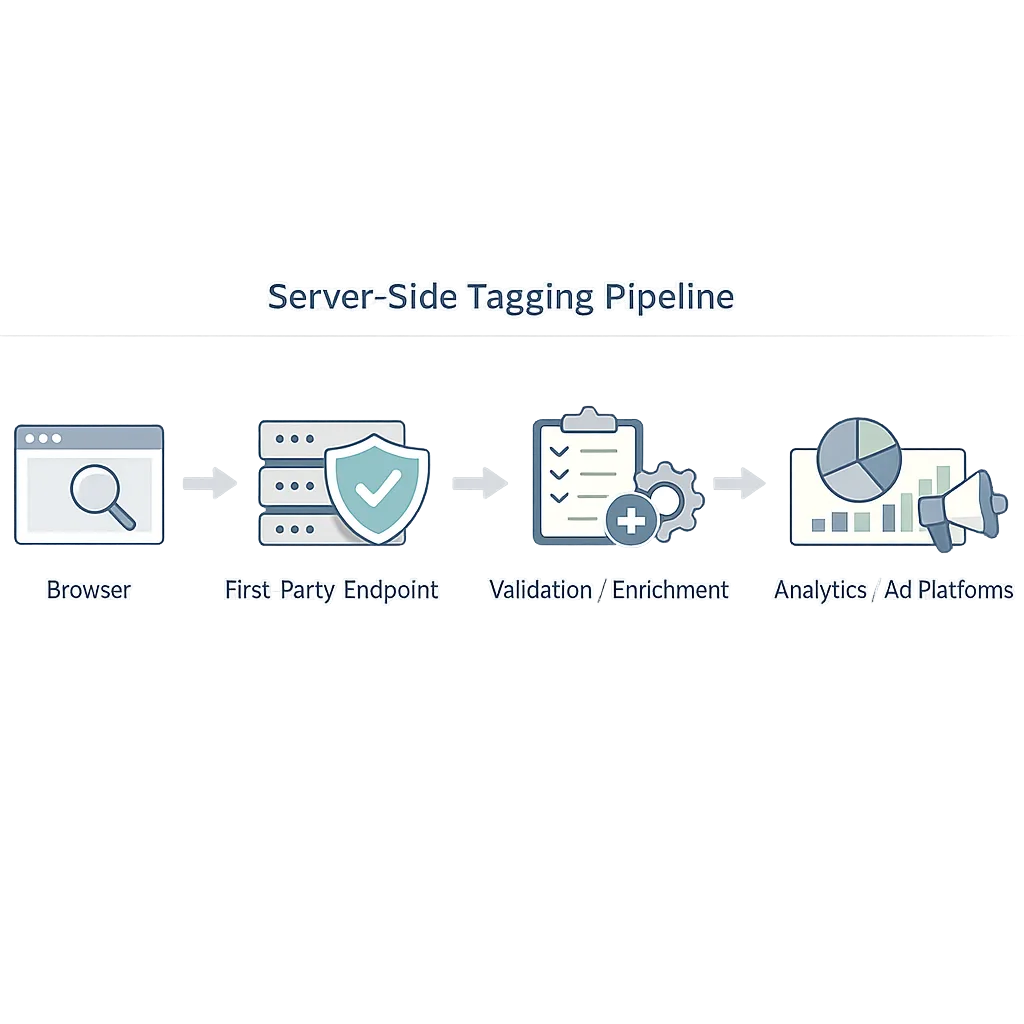
Server-side tagging without breaking UX
Bad server‑side rollouts fail for the same reasons: events don’t match client timing, product teams lose visibility, and ad platforms reject payloads. Avoid those traps by mirroring the client schema, echoing a subset of events to the client for debugging, and implementing idempotency so retries don’t inflate conversion counts.
Two technical gotchas to plan for: cross‑domain flows and storage scoping. If you rely on third‑party iframes for auth or payments, prioritize their first‑party or SDK‑based alternatives—or use the vendor’s documented, user‑mediated storage access. For storage, keep cookies scoped narrowly (path, domain) with secure and httpOnly flags where applicable, and treat the client ID as an input to server logic, not a source of truth.
Measurement that survives stricter modes
A durable measurement plan combines three layers:
- Deterministic, consented events from your sites and apps, captured server‑side and mapped to business outcomes.
- Modeled conversions trained on your deterministic base to fill gaps where browser constraints limit tracking.
- Periodic calibration using holdouts, brand lift, post‑purchase surveys, and MMM to keep models honest.
Frequency capping and sequential messaging still work—just scope them to your first‑party graph and owned channels. For paid media, bias toward platforms that accept server‑side signals with robust privacy controls. You’re not giving up personalization; you’re relocating it to the right layer.
Compliance isn’t a banner—it’s a system
More than ten U.S. states now enforce comprehensive privacy laws, and enforcement stings when your tags fire before consent or your data flows don’t match your disclosures. Treat consent as configuration, not code spread across templates. Centralize purpose definitions, control tag firing from a single policy engine, and emit consent state with every server‑side event. Keep records of what fired, why it fired, and which consent string applied.
If you’ve been postponing this because you feared a rebuild, start smaller: ship a single, verifiable improvement each sprint. For instance, block remarketing until consent is true, then verify decreased unauthorized fires—and document it. That auditable trail is gold during vendor reviews and regulator inquiries.
Data-backed outlook for 2026
There’s no universal cookie cutoff date on Chrome as of January 2026. Safari and Firefox continue to limit cross‑site cookies by default. Chrome private browsing is getting stricter against covert signals, and enterprise controls remain conservative. That adds up to a steady squeeze on legacy cross‑site identifiers and a steady reward for teams that invest in first‑party data and server‑side pipelines.
The smartest companies I’ve worked with stopped asking, “Will Chrome kill cookies?” and started asking, “What’s the smallest change that gives us consistent, permissioned signals across every browser?” They’re the ones watching their blended CAC fall while competitors argue about prompts.
30/60/90-day execution plan
Days 1–30: Prove readiness
- Ship a consent‑gated server‑side purchase event with campaign parameters and a privacy log.
- Flip on synthetic monitoring for Safari, Firefox, Chrome default, and Chrome private paths.
- Kill at least two redundant pixels and move their logic server‑side.
Days 31–60: Stabilize attribution
- Backfill modeled conversions for browsers without third‑party cookies; compare against your deterministic baseline weekly.
- Introduce a basic MMM readout in your BI tool to triangulate channel contribution.
- Coordinate with paid media to ingest server‑side events and adjust bidding.
Days 61–90: Scale and govern
- Add consent state to every server‑side event and expand coverage to micro‑conversions.
- Implement audience sync fed by your first‑party profile graph.
- Publish an internal privacy/measurement runbook and train owners across growth, product, and data teams.
Need help sequencing these sprints? Our services team delivers a hands‑on implementation with weekly checkpoints, and you can see how we approach end‑to‑end delivery on what we do. If you want examples of how we harden stacks under deadline pressure, browse our portfolio and then get in touch.
Risk radar: issues teams overlook
Shadow tags. Old tag managers, hard‑coded pixels, and vendor snippets that no one owns. Audit and delete. Every rogue request is a liability and a performance tax.
Cross‑domain auth. Social login and identity brokers inside iframes can fail silently when third‑party cookies are blocked. Prefer top‑level redirects or provider SDKs that support user‑mediated storage access.
Event timing. Client and server events must reconcile. Without idempotency keys and sequencing, retries inflate revenue and break ROAS calculations.
Disclosure mismatch. If your privacy policy says one thing and your server routes say another, you’re out of compliance even if the user clicked “accept.” Keep your disclosures and routing in lockstep.
What to do next
- Stop debating the headline and start testing under Safari/Firefox and private browsing conditions. If it breaks there, it’s fragile everywhere.
- Stand up a first‑party events endpoint and move your conversion events server‑side with consent signals.
- Refactor one remarketing audience to use your first‑party graph only; monitor CPA and frequency control.
- Document your consent purposes and tag map. If a pixel doesn’t have a purpose, remove it.
- Set a 90‑day goal: “100% of revenue‑critical events captured server‑side with consent state.” Make it visible and track progress weekly.
Third‑party cookies sticking around in Chrome is not a free pass—it’s breathing room. Use 2026 to finish the shift you postponed: consent‑centric data, first‑party identity, server‑validated events, and attribution that survives stricter modes. Teams that do this will bid smarter, ship faster, and sleep better.




Comments
Be the first to comment.