Third-Party Cookies Survive. Your 2026 Plan Shouldn’t.
Yes, third-party cookies are still alive in Chrome. But treating that as a green light to keep your measurement and login flows unchanged is how you wake up to broken funnels on Safari, skewed attribution on Firefox, and rising account takeovers via stolen session tokens. The headline changed; the job didn’t. Let’s use 2026 to ship a durable, browser‑proof growth and security plan.
The headline changed: Google kept third‑party cookies—now what?
In April 2025, Google walked back its multi‑year plan to deprecate third‑party cookies in Chrome, and the UK Competition and Markets Authority later released Google from its Privacy Sandbox commitments in October 2025. Even Google’s own developer docs now warn that add‑on guidance tied to deprecation is no longer necessary. Translation: Chrome users will continue to have cookie choice, not forced removal. That’s the “good” news. (theverge.com)
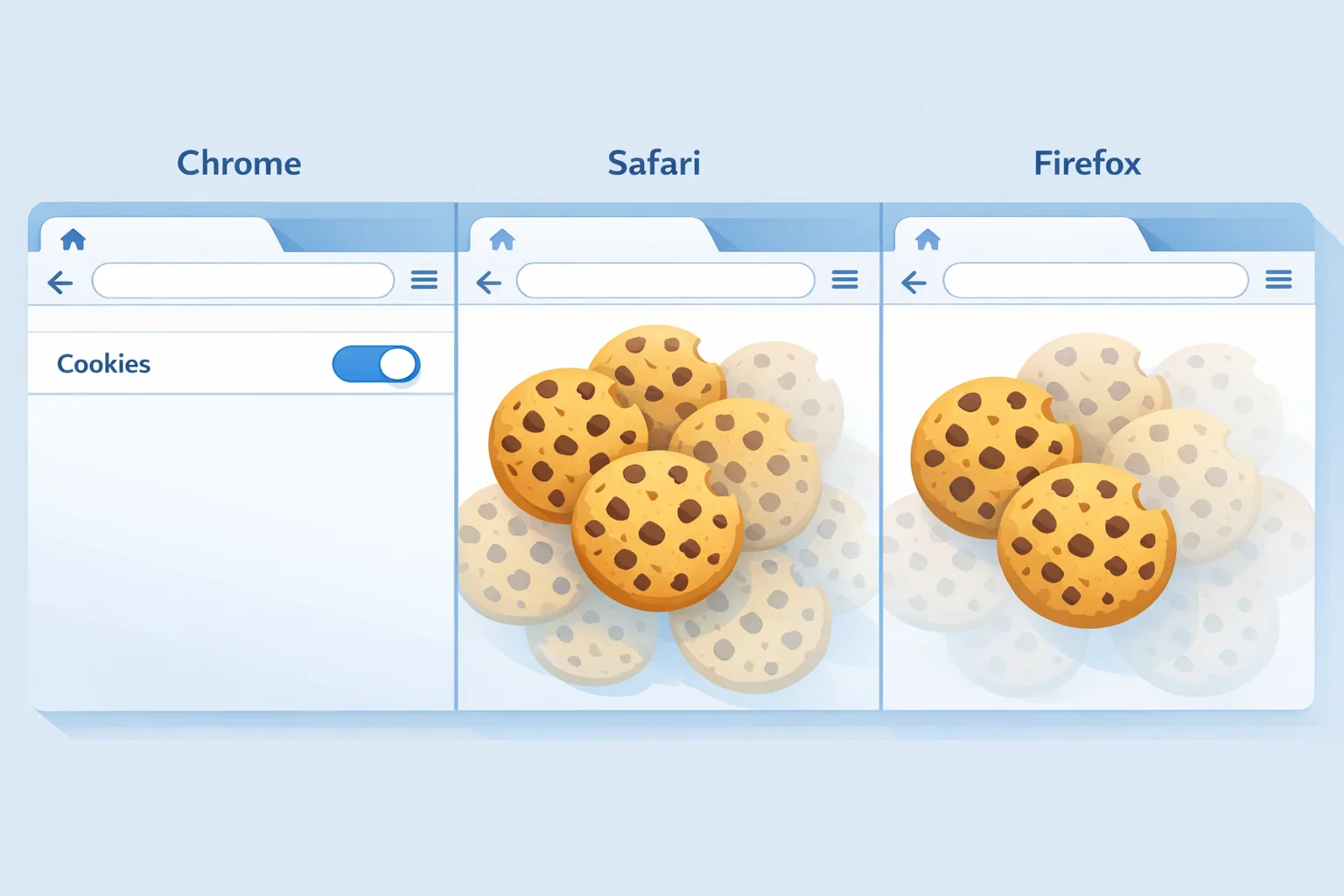
Here’s the catch: outside Chrome, the world never stood still. Safari blocks cross‑site cookies by default through Intelligent Tracking Prevention (ITP), and has for years. Firefox ships Total Cookie Protection (TCP), isolating cookies per site by default. If your funnels depend on cross‑site state, they’re already under stress on a large share of mobile and privacy‑conscious desktop traffic. (webkit.org)
What this means for growth, analytics, and security in 2026
Practically, you’re running three web realities at once: chrome‑style permissive defaults (with opt‑out), Safari’s strict model, and Firefox’s partitioned world. Plan for the strictest, then gracefully degrade for everyone else. Meanwhile, account hijacking via cookie theft surged enough that Chrome proposed Device Bound Session Credentials (DBSC) to tie sessions to the device, making stolen cookies far less useful. DBSC won’t fix your analytics, but it will reduce painful security incidents that erode user trust and revenue. (blog.chromium.org)
Is Privacy Sandbox “over”? What still matters?
Google’s deprecation plan is off; the CMA formally released its oversight; industry coverage described Sandbox’s end. Some APIs and docs linger, but the strategic shift is clear: Chrome isn’t enforcing a universal kill switch on third‑party cookies. Don’t mistake that for “do nothing.” The direction of travel for other browsers—and security risk from stolen tokens—still demands change. (gov.uk)
Two technical threads remain relevant regardless of policy headlines: partitioned cookies (CHIPS) and better session protection (DBSC). CHIPS gives you per‑site cookies for legitimate embedded use cases without enabling cross‑site tracking. DBSC mitigates the malware business model around token theft. Those are worth your time in 2026. (developer.mozilla.org)
Let’s get practical: a 2026 playbook that actually ships
1) Inventory your cookie dependencies (by browser, by flow)
Start with a 90‑minute triage. Map every cookie‑dependent step: SSO in iframes, embedded payment flows, marketing tags, live‑chat widgets, A/B testing, and any cross‑subdomain state. Test each step in: Safari on iOS, Firefox desktop, Chrome with third‑party cookies disabled (simulate strict mode). Document: which cookies are cross‑site, which require third‑party access, and which can be first‑party.
Tip: build a small script to crawl critical paths and log document.cookie visibility, SameSite/Secure attributes, and whether storage access prompts appear. Bake this into CI so regressions are caught before a release train leaves the station.
2) Use CHIPS (partitioned cookies) where you embed third‑party content
For iframes and embedded widgets that legitimately need continuity—think support chat, media players, or payment instruments—use partitioned cookies. In HTTP headers: Set-Cookie: widget_session=abc; SameSite=None; Secure; Partitioned. In JS: document.cookie = "widget_session=abc; SameSite=None; Secure; Partitioned";. Partitioned cookies isolate state per top‑level site, restoring functionality without re‑enabling cross‑site tracking. Safari added CHIPS support (with site‑level partition keys), aligning behavior with Chromium. (developer.mozilla.org)
Reality check: partitioned cookies still require HTTPS and SameSite=None. They don’t give you a free pass for cross‑site identity, and known trackers may be blocked from using them in Safari. They’re a targeted fix for embeds, not a universal measurement replacement. (webkit.org)
3) Harden sessions with DBSC (Device Bound Session Credentials)
Session cookie theft bypasses MFA and devastates teams when a single compromised laptop turns into a week of incident response. DBSC binds the session to a device, so exfiltrated tokens won’t replay elsewhere. Chrome’s proposal targets roughly half of desktop users at first (hardware capabilities drive that number), with a path to software keys to avoid hardware fingerprinting. If you operate consumer logins or admin consoles, DBSC belongs on your 2026 security roadmap. (blog.chromium.org)
How to plan it: treat DBSC like an additional factor at the session layer. Keep your existing secure cookie flags (Secure, HttpOnly, SameSite=Lax/Strict for non‑embed sessions), rotate secrets aggressively, and maintain a fallback for devices that can’t present DBSC proof. Roll out to employees and high‑risk user cohorts first (admins, creators, merchants), then expand.
4) Stop keying logic off the User‑Agent string
Chrome’s User‑Agent reduction means fewer reliable UA details; move to UA Client Hints for any remaining browser‑specific logic. Better: design features that don’t depend on user‑agent at all. If you’re still running regex jungles for device detection, it’s time to refactor. (chromium.org)
5) First‑party data pipelines, not workarounds
Resist the urge to resurrect legacy cross‑site IDs. Invest in durable, consented first‑party data: clean product event streams, server‑side tagging behind your own domain, and clear user‑facing controls. Your experimentation and media mix models improve when your product telemetry is trustworthy. If you’re building on Node, keep dependencies current; recent security releases made patch‑now urgency a norm for backend tag relays. See our quick guide on shipping critical runtime patches without downtime. Ship Node.js security updates today.
6) Consent and transparency that users actually see
Consent UIs should be boring and honest: one sentence of plain English, clear choices, and a link to details. Don’t bury toggles. Wire consent state into your analytics configuration and experiments; don’t record events you said you wouldn’t. This isn’t just risk management—it keeps your datasets clean and makes modeling easier.
7) Build a browser‑matrix test harness
Create a nightly job that: loads top LPs and key onboarding flows; asserts cookie presence, partitioning, and visibility; screens for storage access prompts; and compares event volumes by browser. Alert on meaningful deltas. This is the operational discipline that keeps “it broke in Safari” from hijacking your sprints.
People also ask
Do I still need to prepare for third‑party cookies changes in 2026?
Yes—because the real world is already mixed. Chrome’s reversal reduced immediate breakage risk on one browser family, but Safari fully blocks third‑party cookies, and Firefox isolates them by site. Planning for strict defaults is the only way to avoid whiplash the next time policies or defaults shift. (webkit.org)
Will DBSC replace cookies entirely?
No. DBSC strengthens session integrity by binding tokens to devices. You’ll still use cookies (first‑party and partitioned) for state. Think of DBSC as closing the door on the easiest replay attacks, not a replacement for your session design or auth flows. (blog.chromium.org)
Does Safari support CHIPS?
Yes. Safari shipped partitioned cookies (CHIPS) in version 18.4 and documents site‑level partitioning and requirements. It provides a clean way for embedded third‑party components to persist state without enabling cross‑site tracking. (webkit.org)
A concrete framework: the COOKIE scorecard
Use this scorecard to grade each user journey (0–2 points per item, max 12). Anything under 8 needs a redesign.
- C — Clarity: cookies labeled, scoped, and minimal? (
HttpOnly,Secure,SameSite, expiries) - O — Ownership: first‑party where possible; third‑party only with contracts and DPAs
- O — Orchestration: consent state wired into analytics and experiments
- K — Keying: partitioned (CHIPS) for embeds; no cross‑site identity hacks
- I — Integrity: DBSC plan for high‑value sessions; token rotation, anomaly detection
- E — Experimentation: browser‑matrix tests; alerting on cookie/volume deltas
Data points and timelines that matter
Key milestones to anchor your roadmap: Google’s April 2025 reversal on cookie deprecation; CMA’s October 17, 2025 decision to release Sandbox commitments; Mozilla’s TCP on by default; Apple’s long‑standing third‑party blocking and 2020 announcement of full cross‑site blocking; Safari 18.4 adding CHIPS; Chrome’s UA reduction phases continuing. These are stable enough to build against in 2026. (theverge.com)
Risks, limitations, and gotchas
Partitioned cookies aren’t universal tracking. If your use case truly requires a user to be recognized across unrelated sites, CHIPS won’t do that—and that’s the point. Also, some browsers treat trackers harshly even with partitioning. Don’t plan your business model around a loophole that could be closed tomorrow. (webkit.org)
DBSC requires client capabilities. Chrome’s own write‑up projects initial availability for roughly half of desktop users and emphasizes avoiding hardware‑based segmentation in standards. Plan for fallbacks (short‑lived session rotation, stepped‑up challenges on new devices, and device enrollment for admins). (blog.chromium.org)
Legacy UA sniffing will increasingly fail as UA reduction marches on. If your ad, analytics, or A/B code flips logic on exact OS versions, expect odd bugs and mis‑attribs. Move to feature detection and Client Hints. (chromium.org)
What to do next (this week, this quarter)
This week (5–8 hours)
- Run your cookie inventory against Safari iOS, Firefox desktop, and Chrome with third‑party cookies disabled.
- Identify at least two embeds that can move to CHIPS.
- Draft a DBSC adoption note for security stakeholders (who, where, fallback).
This quarter
- Refactor any UA‑string logic; switch to Client Hints or feature detection.
- Stand up a server‑side tagging endpoint on your own domain; give analytics a stable, first‑party path.
- Automate a browser‑matrix test harness and alerting for cookie/volume deltas.
When you need help
If your team wants a pragmatic partner to ship this without derailing product, we’ve done this before. See what we do for growth and platform teams, browse a few relevant builds in our portfolio, or reach out via contact to scope a fast assessment.
A note for SEO and analytics leads
Expect your organic channel mix to change slightly as privacy‑default browsers grow share on mobile. That’s not a crisis; it’s a measurement reality. Focus your time where you can win: first‑party events flowing reliably from product to data warehouse, attribution models that use aggregated signals over long‑lived cross‑site IDs, and conversion lift experiments to validate spend. If you need a refresher on shipping without policy delays, our recent analyses on platform policy updates and security patch cadences are a good companion read on operational discipline. Check the blog for those deep dives.
Zooming out
The web keeps zigzagging between privacy, competition policy, and practical interoperability. Betting your growth on any one policy prediction is risky. Shipping a resilient stack—partitioned where it should be, first‑party where it can be, and hardened against token theft—is just good engineering. If Chrome’s stance shifts again, you’ll be ready. If it doesn’t, you’ll still have faster page loads, fewer help‑desk tickets, and cleaner data.
That’s the quietly compounding advantage of making the right changes now.




Comments
Be the first to comment.