Third‑Party Cookies Aren’t Dead: Your 2026 Plan
Let’s say it plainly: third‑party cookies didn’t go away. Chrome flirted with deprecation for years, restricted them for a small test cohort in January 2024, and then pivoted in mid‑2024 and 2025 to keep cookies while leaning on user choice. If you paused migrations waiting for a final verdict, 2026 is your chance to reset—without betting the farm on features that may sunset or never reach critical mass.
Where we are now: the third‑party cookies timeline
Here’s the short, verifiable timeline so we’re all on the same page:
• January 4, 2024: Chrome begins restricting third‑party cookies by default for roughly 1% of users to test breakage and mitigation paths. That test stayed in place to observe real‑world impact.
• July 22, 2024: Google announces it no longer plans to fully remove third‑party cookies and instead pursues a Chrome “user choice” model. Translation: cookies stay, but people can toggle them in Privacy & Security settings rather than seeing a brand‑new prompt.
• April 22, 2025: Google says it won’t roll out the standalone cookie prompt at all, and will maintain existing settings while improving Incognito protections and related privacy controls.
• June 13, 2025: The UK’s competition regulator (CMA) signals the legally binding commitments it secured for the Privacy Sandbox process are no longer needed, given Google’s pivot away from removing cookies.
• Late 2025: Multiple Privacy Sandbox pages flag several features as scheduled for phaseout or no longer mandated (for example, fenced frames “no sooner than 2026” and event‑level reporting in Protected Audience supported until at least 2026). In practice, Sandbox becomes optional plumbing—not a forced migration path.
As of today—January 13, 2026—Chrome continues to support third‑party cookies by default, with users able to manage them, and with Incognito blocking them. The Sandbox work isn’t entirely gone, but it’s no longer the main highway you must take.
What changes in 2026 (and what doesn’t)
What doesn’t change: you still need reliable attribution, consent, and audience building. Privacy and competition regulators remain active, and browser makers still tweak protections. What does change: you’re no longer racing a fixed death date for third‑party cookies in Chrome. That means you can focus on durable, incremental upgrades instead of fire drills.
Here’s the thing: keeping cookies isn’t a free pass. Safari and Firefox have long restricted cross‑site tracking. Corporate networks and privacy tools block a lot of pixel calls. And the ad stack is more fragmented than ever. Teams that ship now are doubling down on first‑party data, clean consent UX, and server‑side integrations to reduce client breakage and improve performance.
The 3P→1P Reality Check: a framework you can use
Use this four‑part framework to move from fragile third‑party dependencies to resilient first‑party signals while keeping revenue intact.
1) Audit: Map every cookie and data flow
Start with inventory. Crawl your site and apps to list every tracker, tag, script, and cookie. For each, capture: domain, purpose (analytics, ads, fraud, login), data categories, retention, and downstream vendors. Diff across key templates: homepage, product detail, cart, checkout, account, and post‑purchase.
Then find hard dependencies on third‑party cookies. Typical red flags: legacy retargeting tags that read cross‑site IDs; stitched user journeys that rely on third‑party cookies across your branded subdomains; and auth or embedded tools that break when third‑party cookies are off (SSO pop‑ups, sandboxed iframes, helpdesk widgets).
Tip: include your mobile web views. Hybrid apps often hide silent failures when cookies or storage are restricted in the embedded browser.
2) Consent: Fix UX and governance
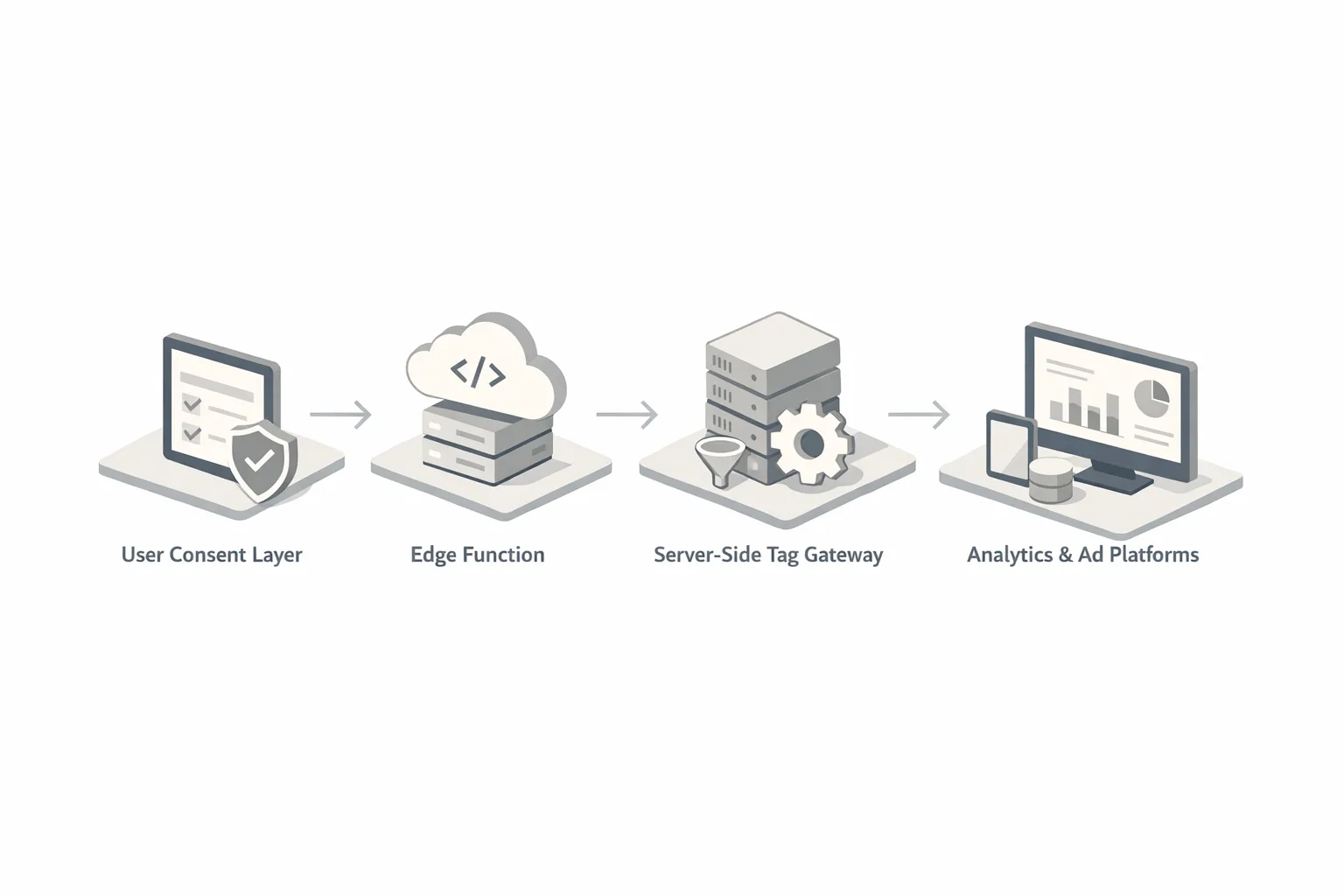
Consent isn’t a banner; it’s a system. Make sure the first interaction is clear, fast, and localized. Keep categories granular enough to be meaningful but not so granular that users smash “reject all.” Bind choices to a server‑side consent record keyed to a first‑party identifier so you’re not at the mercy of a cleared cache.
Governance matters. Wire your tag manager and CDP so they refuse to fire vendors without a valid consent state. If you operate in multiple jurisdictions, define a single policy table (per region, per purpose) and test it with synthetic users. You want provable enforcement, not just a pretty modal.
3) Attribution: Move to durable signals
Rebuild your measurement on first‑party IDs and modeled conversions rather than raw third‑party cookie joins. Prioritize:
• First‑party ID: a server‑generated, privacy‑safe user key (logged‑in user, CRM ID, or hashed email with proper consent).
• Event quality: fewer, richer events > floods of noisy ones. Normalize purchase, subscription, lead, and trial events across web and app with the same schema.
• Server‑side conversion APIs: send signed, deduped conversion events from your backend to ad platforms and analytics. It reduces client breakage and improves match rates when done right.
• MMM and incrementality tests: reserve budget to run geo‑splits or audience holdouts. Modeled lift is your safety net when cookie joins are unreliable.
4) Tech: Upgrade your web stack
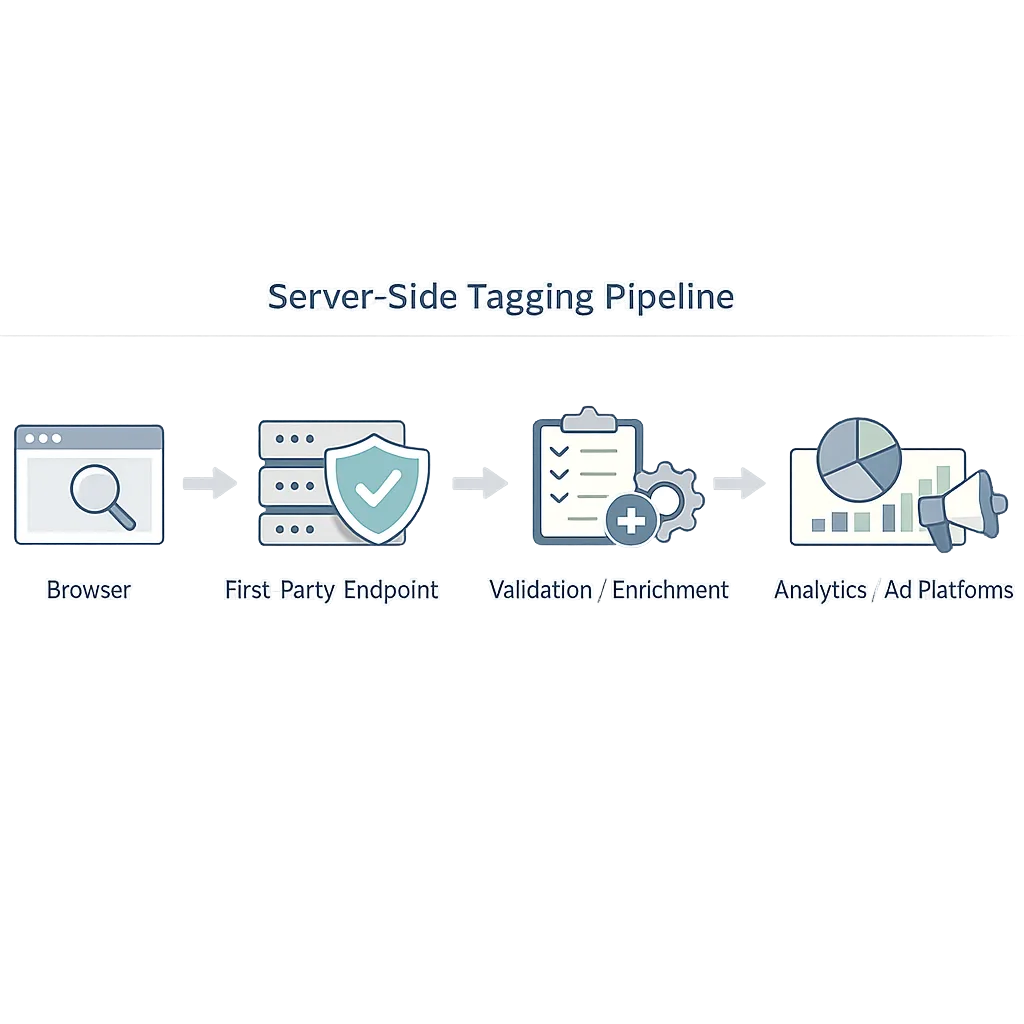
Two upgrades pay off fast. First, server‑side tagging: proxy third‑party tags through your domain, validate payloads, strip PII, and enforce rate limits. Second, identity resolution at the edge: use edge functions to set/refresh first‑party cookies tied to your consent record, with short TTLs and rotation to reduce risk.
While you’re there, clean house. Remove zombie tags. Migrate to HTTP‑only, Secure cookies for session state. SameSite must be explicit (Lax for most, Strict for sensitive flows). And test in browsers with strict defaults—if it works in Safari, you’ll sleep better.
People also ask
Are third‑party cookies going away in Chrome?
No firm deprecation is scheduled. Chrome tested restrictions in early 2024, then kept cookies under a user‑choice model through 2025. As of January 2026, cookies remain available by default (with Incognito blocking them). Plan for resilience rather than a flip‑of‑the‑switch removal.
Should we still implement Privacy Sandbox APIs?
Implement them if they help you hit goals, but don’t assume they’ll be mandated. Some features are marked for phaseout or have “no sooner than” timelines. Run limited pilots where they make sense and measure lift versus the operational cost. Don’t anchor your roadmap to any single adtech experiment.
Will Safari and Firefox do anything different?
They’ve already enforced stricter tracking limits for years. If you rely heavily on third‑party cookies, your pain is concentrated in those browsers. Fixing attribution and consent on WebKit/Gecko typically raises overall performance, even if Chrome keeps cookies.
Implementation playbook: a 60‑day, step‑by‑step path
Let’s get practical. Here’s a proven sequence we’ve used with product and growth teams to reduce risk fast.
Days 1–10: Instrumentation and audit
• Deploy a crawler and tag debugger across top 100 URLs plus high‑value flows.
• Export existing tags from your TMS and reconcile against the crawl.
• Map cookie usage by domain, lifespan, and purpose; flag third‑party dependencies.
• Stand up a consent decision log (even if minimal) so you can verify enforcement.
Days 11–20: Consent UX and policy
• Redesign the banner for speed and clarity; prefetch assets so it never blocks.
• Define a policy matrix by region/purpose; wire it into your TMS and server‑side endpoints.
• Build an admin view to audit per‑request consent decisions and vendor fires.
Days 21–35: First‑party identity
• Choose your durable ID (hashed email, customer ID) with explicit user permission.
• Implement signed, server‑generated cookies for the ID and tie them to consent state.
• Add a kill switch to invalidate IDs if consent is withdrawn or stale.
Days 36–50: Server‑side events
• Mirror your purchase/lead/subscription events to a server‑side endpoint.
• Deduplicate client/server fires; use a consistent event_id.
• Pipe to ad platforms’ conversion APIs with hashing and minimum fields.
Days 51–60: Testing and rollout
• Run A/B or geo tests to quantify impact on match rates and CPA/ROAS.
• Validate in Safari, Firefox, and Chrome Incognito; fix any SameSite or storage edge cases.
• Remove deprecated tags and document your new data flow.
Data and dates you can plan around in 2026
• Chrome’s 1% restriction test began January 4, 2024 and persisted for learning—not as a fixed ramp to 100%.
• Public statements in July 2024 and April 2025 confirmed a shift to user choice and no standalone prompt rollout.
• Regulator posture softened in mid‑2025 as mandates tied to cookie removal were reconsidered.
• Protected Audience’s event‑level reporting is supported at least through 2026, with fenced frames not mandated before 2026. Treat those as optional pilots, not bedrock.
None of this stops you from using cookies. It just means the industry’s “forced migration” pressure is gone. Your competitive edge now comes from disciplined engineering and better data stewardship, not from chasing a mandatory deadline.
Risks and edge cases you should plan for
• Embedded SSO flows: third‑party cookies disabled in pop‑ups or iframes can still break logins. Modernize your OAuth flow (PKCE, SameSite fixes, post‑message redirects).
• App webviews: many mobile webviews behave more like Safari than Chrome. Verify storage, navigation, and deep link handoffs across iOS and Android.
• Multi‑region policy drift: one CMS change can silently re‑enable vendors in restricted regions. Use allowlists, not manual tag toggles.
• Data leakage: server‑side tagging can become a blind “proxy everything” pipe. Enforce schemas, strip PII, and log payloads for audits.
What to do next
1) Book a two‑week audit sprint. Inventory tags, cookies, and consent wiring across web and app. If you want help, our team’s analytics and data engineering services include a fast forensic crawl and consent enforcement check.
2) Stabilize attribution with server‑side events. Pick one funnel (checkout, subscription, or lead) and ship a clean, deduped server‑side conversion feed to your top ad platform.
3) Stand up a first‑party ID. Tie it to consent and governance. Document rotation, TTLs, and revocation.
4) Test in strict browsers first. Make Safari/Firefox green, then polish Chrome. That discipline pays back quickly.
5) Keep an eye on policy changes. Platform rules shift. Our blog tracks the practical implications for shipping teams, including app store policy changes that often ripple into web data practices.
Related reads from our team
If you manage cross‑platform products, you know policy pivots aren’t limited to the web. Our breakdown of Google Play external links in 2026 shows how payments policy can impact attribution and UX. And if you’re modernizing runtime and infra hygiene while you refactor tracking, our Node.js 20 EOL 2026 migration playbook has a solid checklist mindset you can re‑use.
FAQ for execs who have to sign the budget
“Can we just keep everything as‑is since cookies survived?” You can—but you’ll bleed signal quality in non‑Chrome traffic and under stricter privacy settings. The better question is what minimal upgrades protect revenue across all browsers. Start with server‑side conversions and consent governance; they pay back in months.
“What’s a realistic timeline?” Sixty days for a baseline upgrade at mid‑market scale, six months for multi‑region consent and full server‑side tagging with identity resolution.
“Where do the savings show up?” Lower wasted spend from deduped conversions, better match rates, fewer broken flows in Safari/webviews, and reduced compliance risk. Engineering time shifts from break‑fix to roadmap work.
Zooming out
The industry spent five years preparing for a cliff that never came. That’s fine. You didn’t waste time—you built muscles. Now put them to work where they matter: first‑party data, consent you can prove, and measurement that survives the next shift—because there will be a next shift.
If you want a pragmatic partner who’s shipped this before, see what we build on our portfolio and reach out via contacts. We’ll help you modernize without breaking the business.




Comments
Be the first to comment.