Privacy Sandbox 2026: What to Build Now That Cookies Stay
Here’s the thing: the Privacy Sandbox 2026 conversation has changed. Chrome kept third‑party cookies as a user choice instead of killing them outright, but the ecosystem still moved. Advertisers are pushing for durable measurement, regulators are enforcing consent, and the Sandbox APIs continue to evolve. If your roadmap assumed a hard cutover, you need a cookie‑optional plan—not a cookie‑or‑bust plan.
I’ve spent the past year helping teams ship in this gray zone. Below is a pragmatic strategy for 2026 that balances today’s performance with tomorrow’s standards. We’ll use third‑party cookies where they’re available and appropriate, but we’ll stop depending on them. We’ll implement the parts of Privacy Sandbox that add value now, and we’ll design for easy swaps if APIs change.
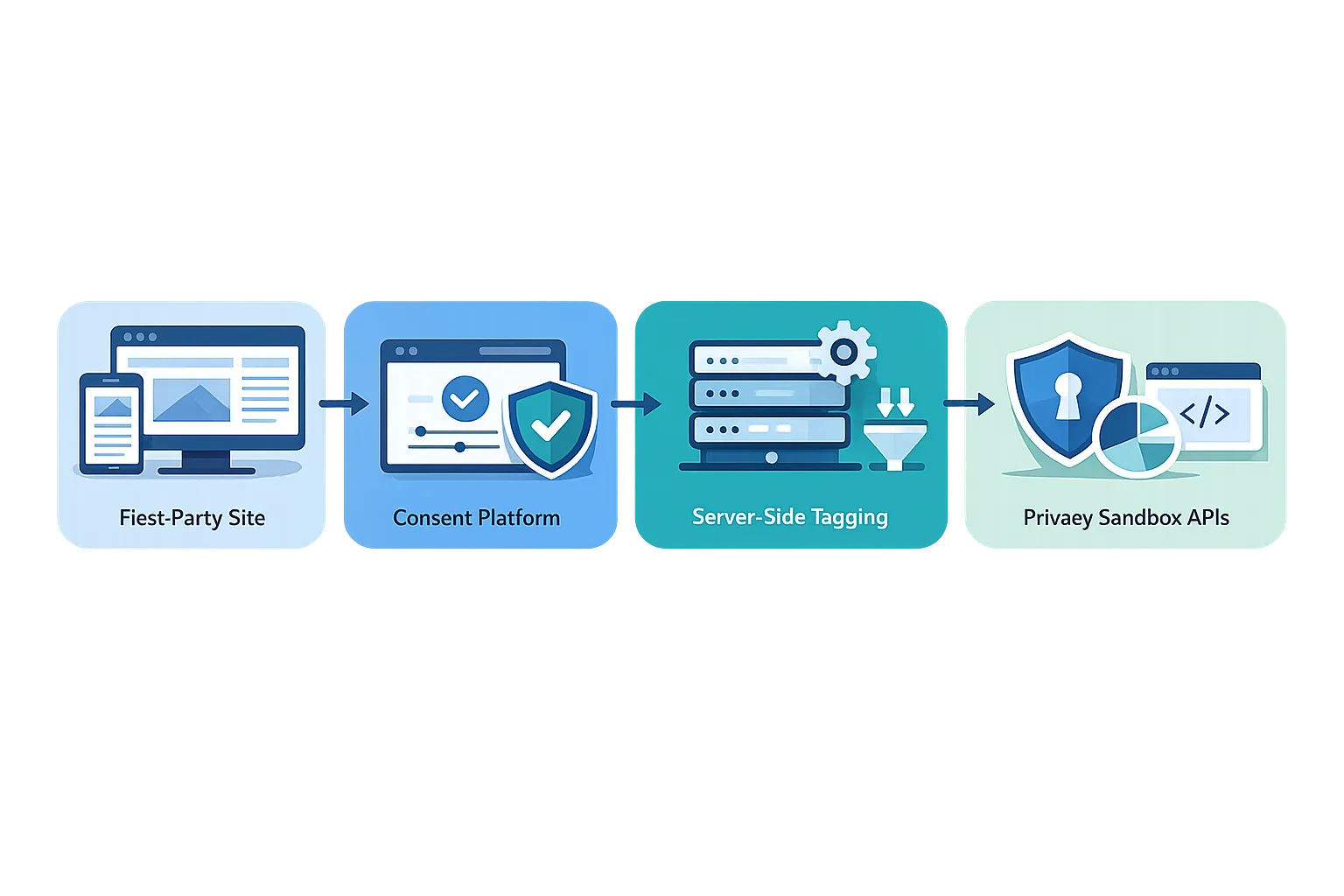
Privacy Sandbox 2026: the reality check
Let’s anchor on the current facts developers care about:
• Cookies aren’t gone in Chrome. Users can allow or block third‑party cookies, and organizations should expect mixed states across sessions and markets.
• Measurement APIs matter anyway. The Attribution Reporting API (ARA) exists and is widely testable in Chrome. WebKit backs a different approach (Private Click Measurement), which means cross‑browser parity still requires work.
• Protected Audience (PAAPI) is usable. Interest group remarketing and on‑device auctions are real, with event‑level win reporting supported at least through 2026 to ease migrations. Fenced Frames won’t be mandatory until 2026 at the earliest, so you can still render via iframes while you plan the shift.
• Topics is modest but useful. The taxonomy hovers around a few hundred human‑curated categories (roughly 469), meant for broad interest signals—not precision targeting.
• Consent is non‑negotiable. In the EEA, UK, and Switzerland, certified CMPs and stronger consent signaling are table stakes if you want full ad features. Even with cookies available, missing consent can switch off the very signals your ads and analytics rely on.
Net: the hybrid era is here. You need a stack that measures and targets effectively with or without third‑party cookies, and that respects regional consent requirements by design.
The cookie‑optional plan for 2026
Below is the plan I recommend to product leads, growth teams, and engineering managers who need results this quarter and a credible roadmap for the rest of the year.
1) Ship consent and data governance first
Consent isn’t just a banner—it’s a control plane. If you serve users in the EEA/UK/CH, use a Google‑certified CMP that integrates with the IAB TCF, and emit Consent Mode v2 signals (ad_user_data and ad_personalization) through your tags. That protects modeled conversions and remarketing eligibility when users consent, and it keeps you compliant when they don’t.
Best practices I see working:
• Treat consent as a dependency for all tags (analytics, ads, A/B testing).
• Route consent state into your data layer; don’t let each vendor interpret the page differently.
• A/B test your copy and layout for clarity, not dark patterns. Clear, honest language performs better over time.
Implementation tip: if you run server‑side tagging, propagate consent state to the server container and respect it there too. Nothing torpedoes trust faster than client consent ignored on the back end.
2) Fix attribution where you can actually win
Yes, split attribution is messy right now. You’ll often combine: first‑party analytics, platform conversions (Google, Meta, etc.), and a Sandbox API. The goal is consistency, not perfection.
Start with this sequence:
• Stabilize first‑party conversions: server‑to‑server events from your back end (orders, signups, subscriptions) with reconciliation to client events.
• Enable Attribution Reporting in Chrome contexts where you can: configure source and trigger registrations, permissions policy, and debug with chrome://attribution-internals plus header validation tools.
• Map to WebKit’s Private Click Measurement on Safari. Even if you don’t implement PCM immediately, design your event schema and redirect flows so adding it is a small patch, not a rewrite.
How to judge impact: track lift in attributed conversions where third‑party cookies are blocked (Safari, Firefox, cookie‑blocked Chrome). If your lift is marginal, you still bank resilience; if it’s material, double down.
3) Prepare remarketing with Protected Audience—carefully
PAAPI enables on‑device interest group membership and auctions. Two realities: it works today in Chrome, and pieces are still evolving. Event‑level win reporting remains available to keep billing and reporting sane; Fenced Frames aren’t mandatory for Chrome until at least 2026.
Practical path:
• Start small with one or two high‑ROI remarketing segments (for example, cart abandoners and high‑value visitors).
• Use an iframe rendering path first; plan a parallel proof‑of‑concept for Fenced Frames so you’re not surprised later.
• If you use key/value services for real‑time bidding signals, note that Trusted Execution Environment requirements harden over time. Run BYO services now; budget engineering time to migrate to TEE‑backed services when required.
Operational note: put strong guardrails on interest group lifetimes and membership size to keep memory and policy risks low. Treat every new signal as potentially sensitive.
4) Build first‑party data that actually earns its keep
“Collect emails” is not a strategy. You need a value exchange. Offer account benefits, content access, loyalty perks, or shipping convenience—and measure opt‑in rates by cohort. Hash and salt identifiers before activation; honor user deletion globally, not just in one system.
Technical moves I recommend:
• Server‑side tagging for durability and control (rate limits, retries, transformations).
• Event contracts between product and data teams so schema changes don’t break downstream systems.
• Periodic identity audits: enumerate where emails, phone numbers, and device IDs land; verify DSR paths and TTLs.
5) Observability and break‑glass drills
Sandbox integrations fail differently than cookie pipelines. Add dashboards for:
• Consent coverage by region and device class.
• ARA report volumes and error codes, with alerts on sudden drops.
• PAAPI participation rates and win reporting consistency.
• Cross‑browser gaps: Safari/Firefox vs Chrome performance deltas.
Run a monthly break‑glass drill: block third‑party cookies in your staging Chrome build and confirm that key journeys still attribute, segment, and bid as expected.
What about SEO vs. ads? Does Privacy Sandbox touch both?
Indirectly. Privacy Sandbox is about ads relevance and measurement—not rankings. But the same consent and data hygiene that keep ad signals flowing also preserve analytics quality and conversion data that feed SEO roadmaps. When your reports aren’t missing EEA conversions, your content ROI decisions improve. If you’re re‑platforming, see our practical approach in React 19 Migration: What to Ship—technical stability and performance pay dividends across acquisition channels.
People also ask
Do I still have to migrate if third‑party cookies are available?
Yes—because they’re not available everywhere. Safari and Firefox block them, and many Chrome users disable them. If you depend entirely on third‑party cookies, your cross‑browser performance will be uneven and your EEA reporting will collapse when consent isn’t granted. A cookie‑optional architecture gives you predictable results now and a cleaner path when standards change again.
Is the Attribution Reporting API future‑proof?
Treat ARA as a transitional tool that’s available and useful in Chrome today. Browser vendors are debating interoperability. Design your measurement layer so you can swap in an emerging shared standard or align with WebKit’s PCM without rewriting your product code.
Should I implement Topics?
It’s low lift and low risk if you already run contextual or broad interest campaigns. Don’t expect laser‑precise targeting—this is about broad signals. If you have limited engineering time, prioritize consent, attribution, and first‑party data first; add Topics once the foundations are solid.
A practical 90‑day rollout
Here’s a sequence you can run with a small cross‑functional squad:
Weeks 1–2: Baseline. Audit consent coverage, third‑party cookie reliance, and cross‑browser performance. Identify your top 3 conversion events and remarketing segments. Write an event contract and freeze schema changes for the quarter.
Weeks 3–5: Consent foundation. Deploy a certified CMP, wire Consent Mode v2, and pass consent state into your client and server tags. Instrument dashboards that show consent rates and conversion modeling eligibility by region.
Weeks 6–8: Measurement durability. Enable ARA in Chrome flows where you control both source and trigger. Validate with chrome://attribution-internals and header tools. Backfill server‑to‑server conversions from your order system with idempotent keys.
Weeks 9–10: Remarketing pilot. Create one PAAPI interest group and a simple seller script. Start with iframe rendering; capture win reports and compare to cookie‑based reporting where available.
Weeks 11–12: Decision checkpoint. If lift is visible in cookie‑blocked contexts, expand the pilot; if not, keep the codepaths behind flags and revisit when your audience or spend justifies it. Either way, you now operate in a cookie‑optional mode.
Risks, gotchas, and edge cases
• Incognito and user settings: ARA is disabled in Incognito and can be turned off by users; design fallbacks.
• Permissions Policy: if you embed third‑party iframes, they can’t use ARA without explicit allow permission.
• Cross‑browser divergence: Safari’s PCM differs conceptually; write an adapter layer so your app code doesn’t care which API produced a report.
• Fenced Frames timeline: don’t hardcode assumptions. Keep rendering options behind a feature flag so you can switch to Fenced Frames when needed.
• Consent regressions: a broken banner or mis‑routed consent state can silently zero out modeled conversions. Alert on consent rates and investigate sudden drops immediately.
The minimal architecture that works
If you need the shortest path to resilience, build this:
• Certified CMP emitting Consent Mode v2 signals to client and server.
• Server‑side tagging or a lightweight event gateway that deduplicates and retries.
• ARA enabled on key click‑through funnels (search/social → site → purchase), with a guardrail header that can disable it per route.
• PAAPI pilot for one remarketing segment, with controlled lifetimes and a clear exit plan.
• Observability: consent coverage, cross‑browser conversion rates, API error budgets.

What to do next
• Book a joint working session between growth, product, and engineering. Decide where third‑party cookies still deliver incremental value—and where they don’t.
• Stand up a staging environment with third‑party cookies disabled by default to test your fallback behavior.
• Implement Consent Mode v2 and certified CMP integration; prove that consent state controls every tag.
• Turn on ARA for one key funnel and verify with real conversions, not sandbox demos.
• Pilot PAAPI on a single remarketing segment with clear success metrics and shutdown criteria.
• Document your swap plan: how you’d replace ARA with a future interoperable API or align with PCM.
Want a sanity check on your architecture or a sprint partner to get this live? Explore what we do, see our work in the wild, and browse more practical guides on our blog. If you need an implementation plan next week, talk to us.




Comments
Be the first to comment.