Node.js Security Release, Jan 2026: Patch React/Next Now
The January 13, 2026 Node.js security release shipped fixes for eight vulnerabilities across all active release lines and, critically, mitigates a denial‑of‑service condition that can crash processes when async_hooks is enabled. If you run React Server Components, Next.js, or any APM tracer in production, this affects you. Let’s cut through the noise: what changed, who’s at risk, which versions to deploy, and how to roll out safely this week.

Node.js security release: what shipped on January 13, 2026
Updates landed for 20.x, 22.x, 24.x, and 25.x, addressing 3 High, 4 Medium, and 1 Low severity issues. Dependency bumps include c‑ares 1.34.6 and undici 6.23.0/7.18.0. The headline for app teams is the mitigation for uncatchable stack overflows when async_hooks is active—something that quietly touches a huge slice of the ecosystem via AsyncLocalStorage and APM instrumentation.
Shipping versions you should see in your environment today: 20.20.0, 22.22.0, 24.13.0, and 25.3.0. If your fleet isn’t on one of those (or a distribution rebuild of the same), you’ve still got work to do.
Why React, Next.js, and APM users are squarely in scope
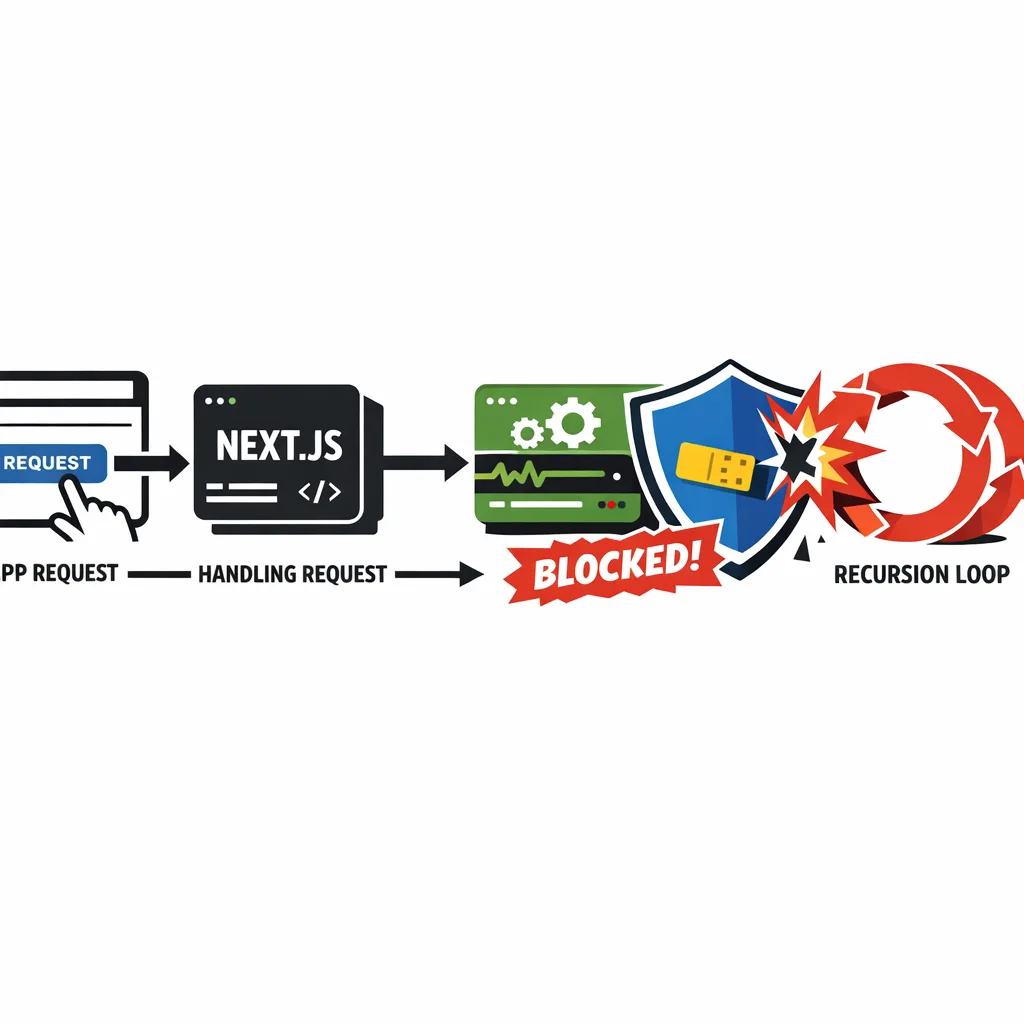
Here’s the thing: when async_hooks is enabled, a deep recursion in user code could previously bypass normal error handling and kill the process with exit code 7 (no try/catch, no uncaughtException). That’s not a hypothetical lab trick. React Server Components use AsyncLocalStorage to carry request context; Next.js relies on it for cookies/headers; and every major APM (Datadog, New Relic, Dynatrace, Elastic, OpenTelemetry) traces across async boundaries by turning on hooks. In practice, all it takes is a maliciously nested payload or an accidental recursion bug to trigger a restart loop.
A plausible incident you can actually picture
Imagine a Next.js route that accepts JSON and normalizes it recursively. An attacker sends a 50k‑level nested array. With async_hooks active, the stack overflows and the process exits—no graceful 500, no circuit breaker. If you’re auto‑restarting, your orchestrator brings the app back up, the attacker hits it again, and your error budget evaporates. If you’re on serverless, a burst of cold starts and throttles can cascade across dependencies.
Does Node 24+ make this disappear?
Not entirely. Node 24 reimplemented AsyncLocalStorage using V8’s AsyncContextFrame, which means React/Next.js don’t need async_hooks for their own context on that line. That reduces the blast radius. But if you run a tracer that still enables async_hooks, you can reproduce the crash on 24.x too. The January patches make recovery far more consistent across lines, but availability still depends on your code and inputs. Treat the update as necessary, not sufficient.
What versions should I deploy today?
Target one of these per line: 20.20.0, 22.22.0, 24.13.0, or 25.3.0. On managed platforms, confirm the underlying runtime—not just your package.json engines field.
- Containers: update your base image, rebuild, and verify the Node binary inside the image. Don’t assume your registry’s “latest” tag moved.
- Serverless: pin the runtime to the patched minor (or a platform alias that maps to it) and force a full redeploy to refresh warm pools.
- PaaS: check the buildpack or stack stack release notes; promote an app image that bundles the new Node bits.
If you need a deeper operational cadence, we published a short checklist in Node.js Security Release: What to Patch Today—use it to structure approvals, rollouts, and audit artifacts.
Quick triage: the 60‑minute checklist
You can make meaningful progress in an hour. Run this now:
- Inventory the runtime: for each service, run
node -vin prod shells ordocker runshells. Snapshot the results. Flag anything not at 20.20.0, 22.22.0, 24.13.0, or 25.3.0. - Search for hard signals: scan logs and orchestrator events for
exit code 7, repeated restarts, or spikes aligning with unknown nested payloads. - Trace surface check: list APM agents and versions. If any agent enables
async_hooks(most do), prioritize those services for canary deploys. - Gate big inputs: add temporary limits to JSON depth and array nesting at the edge. If you’re behind a gateway, add a schema or body size/depth limit now.
- Schedule the rollout: pick the first window for services facing untrusted input, then internal APIs. Don’t wait on an “all clear” from every team; ship under a feature freeze if you must.
How to test without breaking prod
Let’s get practical. In staging or a direct replica:
- Repro harness: craft a nested payload generator and hit the hot path that was most likely to recurse. Verify that the patched runtime returns a 4xx/5xx or a safe error path, not a process exit.
- With and without APM: run the same test with your tracer on and off. You’re validating both runtime behavior and agent compatibility.
- Memory and CPU ceiling: record process RSS and CPU during the test; compare to pre‑patch baselines. Resource spikes can hint at regressions, especially when the tracer is active.
- Serverless traps: cold start time with tracing on can tick up if the platform refreshed layers. Measure it.
Write down the exact Node version observed at runtime and attach the test payload and logs to your change ticket. That’s the audit trail you’ll want a month from now.
People also ask: does this affect React apps that don’t use RSC?
If you’re rendering only on the client and your Node backend doesn’t enable AsyncLocalStorage or an APM tracer, your risk is lower. But most real apps eventually enable tracing, job queues, or server‑side rendering. In other words: you might be fine today, but future you will install a tracer. Patch now while it’s easy.
People also ask: how do I know if async_hooks is enabled?
In practice, if you import a tracer like dd-trace, newrelic, or initialize OpenTelemetry, you’re enabling it. You can also add a guard in a non‑critical code path to see if AsyncLocalStorage context flows through: if it does, tracing or framework internals are active. The safest assumption in 2026 web stacks: hooks are on more often than you think.
A pragmatic guardrail you can deploy this week
While the patched runtime makes the crash less likely, validate inputs anyway. Two low‑friction defenses:
- Depth‑bounded JSON parse: wrap your parser with a depth counter and reject when you exceed a sane threshold for your domain (e.g., 64 or 128).
- Iterative over recursive transforms: if you routinely traverse trees, switch hot paths from recursion to an explicit stack/queue. You’ll gain predictability and avoid stack blowouts entirely.
Neither replaces patching. They do buy you headroom against similar classes of denial‑of‑service bugs.
What about the other CVEs?
The drop also included fixes for a race in zero‑filled buffer allocation (confidentiality/integrity impacts), HTTP/2 malformed header handling that could crash servers, permission model bypasses via symlinks and Unix domain sockets, a TLS callback error‑handling gap, and a targeted fix for a certificate‑parsing memory leak on 24.x. If those sound low‑probability, remember: modern exploit chains glue together “weird” bugs. Patch, don’t pick and choose.
Platform gotchas: serverless, containers, and PaaS
Every January, teams ship app code and forget the foundation. Don’t. Three places we see rollouts stall:
- Serverless runtimes: many platforms map “Node 20” to a minor behind the security release for days. Force a redeploy and check the live runtime. If your platform lags, bundle a custom layer.
- Container images: your digest from last week is unpatched. Use a dated base tag (e.g., node:24.13.0-alpine), rebuild, and confirm with
node -vinside the final image. - PaaS buildpacks: even when a platform updates quickly, your app can be pinned to an older stack. Read the stack release notes and republish.
If your team needs a battle‑tested rollout pattern, borrow from our January 2026 Patch Tuesday playbook—the same dependency triage muscle applies here.
How this interacts with React/Next.js upgrades
React 19 and recent Next.js releases lean harder on server components and actions, which means more async context. Keep your framework upgrades and Node patching decoupled but coordinated: patch Node now, then schedule framework bumps with focused QA. Our guide to shipping React 19 safely in early 2026 covers the rollout patterns we use with client teams.
Operational smoke tests you can automate
- Exit‑7 sentinel: alert on any process exit with code 7. That’s your canary for recursion‑adjacent dangers.
- Payload fuzzer: run a nightly job that hits a non‑prod environment with nested JSON up to your limit. Fail the job if the service restarts.
- Tracer toggles: keep a runtime flag to disable APM in emergencies. You shouldn’t need it often, but when you do, you’ll need it fast.
What to do next
Here’s the short action list for today and this week:
- Upgrade Node to 20.20.0, 22.22.0, 24.13.0, or 25.3.0 across all services. Verify in runtime, not just CI.
- Roll out depth limits and iterative transforms on routes that parse user‑supplied JSON.
- Test with tracing on and off; compare behavior and resource curves.
- Put an alert on exit code 7 and on restart loops. Capture payload samples where legal.
- Schedule follow‑up time to trim recursion in hot paths and to review APM versions.
If you’d like help triaging environments or planning a safe rollout, our team does this work every week. See what we do for engineering teams, or get in touch for a rapid assessment. For mobile and platform policy changes that might collide with your sprint, our recent pieces on Google Play policy shifts and Android release cadence are on the blog.
Bottom line
The January 13 drop is not business as usual. The async_hooks mitigation reduces a real availability risk for React/Next.js backends and for any service running tracing. Patch the runtime now, put simple depth limits in front of untrusted inputs, and keep an eye on exit code 7. Then, once you’re steady, continue your framework upgrades on your own schedule. Ship fast, ship safe—and prove it with logs, versions, and tests.





Comments
Be the first to comment.