Node.js January 2026 Security Release Playbook
The Node.js security release on January 13, 2026 is not one to punt. This Node.js security release touches all active lines—20.x, 22.x, 24.x, and 25.x—with three high‑severity issues and several medium/low items that affect HTTP/2 servers, TLS paths, Buffer allocation, and the experimental Permission Model. If you run Node in production—and who doesn’t?—you’ve got work to do.

What shipped on January 13, 2026—and why it matters
Node.js published patched releases for every supported line:
• 20.20.0
• 22.22.0
• 24.13.0 (LTS)
• 25.3.0
Package bumps in the release train include undici (6.23.0/7.18.0 depending on line) and c‑ares 1.34.6. The headline vulnerabilities:
• CVE‑2025‑55131 (High): A timeout/race can expose uninitialized memory in Buffer.alloc/TypedArrays under specific timing conditions (notably with the vm module’s timeout). In the wrong workload, that’s secrets in memory leaking through your API or logs.
• CVE‑2025‑55130 (High): Permission Model symlink traversal could bypass --allow-fs-read/--allow-fs-write. If you sandbox scripts with the Permission Model, this closes an escape hatch.
• CVE‑2025‑59465 (High): Malformed HTTP/2 HEADERS could crash a process via an unhandled TLSSocket error—classic remote DoS for servers that didn’t wire low-level TLS error handling.
• CVE‑2026‑21636 (Medium): Unix Domain Sockets could slip past network permissions when --permission is enabled.
• CVE‑2026‑21637 (Medium): Exceptions thrown in TLS PSK/ALPN callbacks could bypass normal handlers and leak FDs or crash the process.
• CVE‑2025‑55132 (Low): fs.futimes() could alter timestamps despite read-only permissions when the Permission Model is on.
• CVE‑2025‑59464 (Medium, already fixed on 24.12.0): TLS client cert parsing memory leak when iterating X.509 fields.
Here’s the thing: none of these are theoretical curiosities. If you operate HTTP/2 in production, process client TLS certificates, or rely on the Permission Model for isolation, you’re in scope. And the Buffer/TypedArray race is the kind of bug that turns an internal secret into an API response when load and timing align.
Am I affected? A quick triage map
Use this to decide urgency before you read the rest:
• Runs HTTP/2 servers (especially with default TLS error handling)? Treat CVE‑2025‑59465 as a remote DoS; patch now.
• Uses the Permission Model in any environment (multi‑tenant tasks, CI runners, sandboxes)? Patch immediately for symlink traversal (CVE‑2025‑55130) and UDS policy gaps (CVE‑2026‑21636).
• Uses vm with timeouts or handles untrusted input under tight time constraints? Patch for CVE‑2025‑55131 to avoid memory disclosure.
• Terminates client TLS with certificate inspection (getPeerCertificate(true)) on 24.x? Ensure you’re on ≥24.12.0; the rollup includes 24.13.0.
• TLS with PSK/ALPN callbacks? Patch to eliminate crash/FD leak paths (CVE‑2026‑21637).
Node.js security release checklist (fast path)
Ship the minimum safe change, verify, and move on. Here’s the practical order:
1) Identify your active Node lines and versions. On each service host/container: node -v
2) Map each service to the patched target: 20→20.20.0, 22→22.22.0, 24→24.13.0, 25→25.3.0.
3) Update base images and lockfiles. For containers, bump your FROM to node:20.20.0 (or the line you run). Rebuild images with clean layers to purge stale OpenSSL/undici/c‑ares copies from prior builds.
4) Roll through pre‑prod with error visibility. Turn on TLS socket error logging and aggressive HTTP/2 tests to exercise the new error pathways.
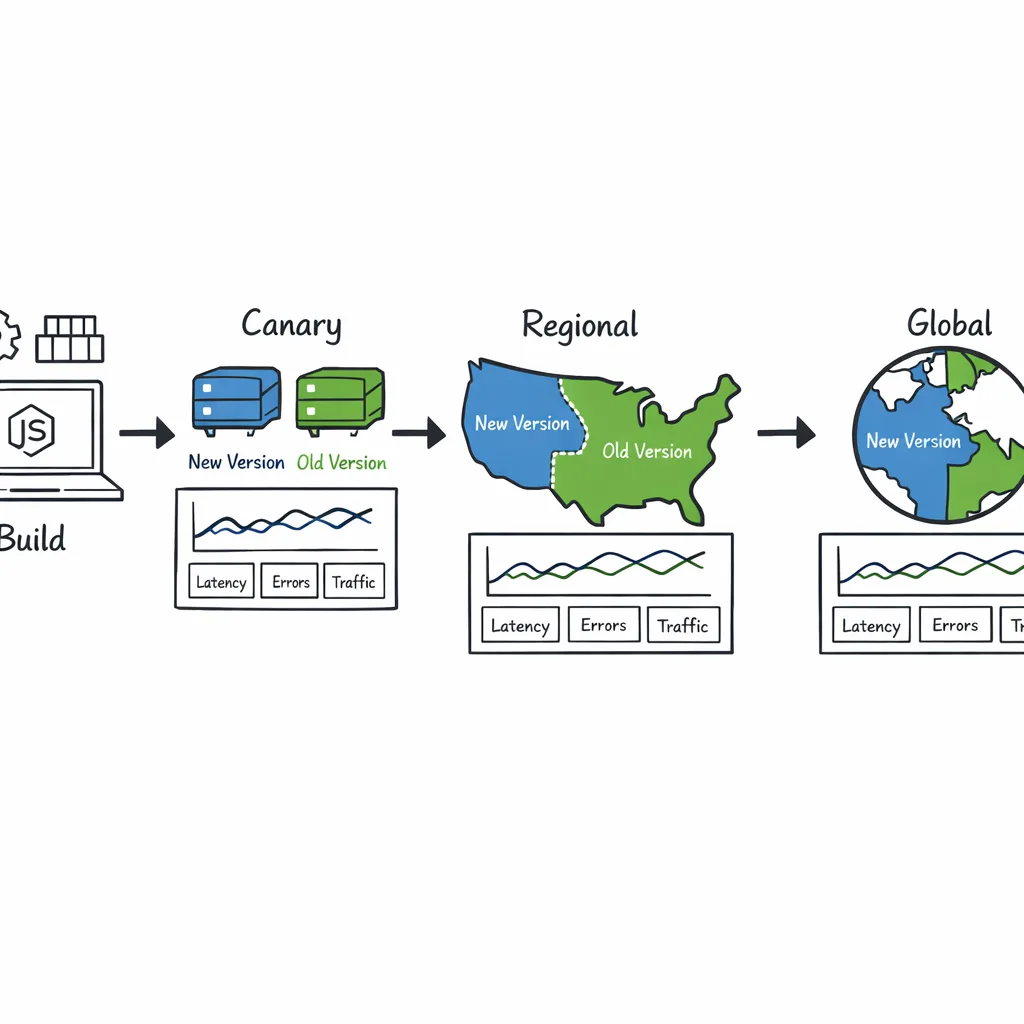
5) Deploy safely: start with low‑blast‑radius services (edge, canary regions), watch CPU/memory/socket handles, then advance to core APIs.
6) Confirm no stray undici pinning. npm ls undici and your lockfile should reflect the line’s intended version; watch for transitive pin conflicts.
7) Rebaseline detection. Update your SCA/SBOM and vuln scan baselines so the new CVEs are marked remediated. Adjust WAF rules and monitors that reference known crash signatures.
Want a one‑pager you can hand to your on‑call? We built it here: Node.js Security Release: What to Patch Today.
What changed technically—and how it can break you
HTTP/2 HEADERS handling (CVE‑2025‑59465)
Before the fix, malformed HPACK data could trigger a low‑level TLSSocket error that bypassed graceful handling and toppled the process. After upgrading, Node installs safer default error handling to prevent a process‑wide crash. If you previously relied on default behavior, great—you’re safer. But if you had bespoke error wiring, re‑run your integration tests; the lifecycle of TLS socket errors may present differently and silence a warning you expected to see.
Buffer.alloc/TypedArrays zero‑fill under timeouts (CVE‑2025‑55131)
The patch ensures allocations aren’t exposed to userland until they’re safely initialized. Practically, that reduces timing sensitivity in codepaths under load. If you have tests asserting on buffer initialization timing, expect behavior to be more deterministic now.
Permission Model hardening (CVE‑2025‑55130, CVE‑2026‑21636, CVE‑2025‑55132)
Expect tighter checks around symlink resolution, UDS connections, and timestamp updates. If your build tools or scripts rely on clever symlink tricks—or if local IPC used UDS without --allow-net—those will now be blocked when --permission is enabled. That’s the security boundary you asked for, but it may break dev tooling that ran inside the same guardrails as production jobs.
TLS callback error propagation (CVE‑2026‑21637)
Thrown exceptions in PSK/ALPN callbacks now route through consistent handlers. If you previously masked these with process.on('uncaughtException'), that crutch is less relevant. Do the right thing: validate inputs earlier and fail fast inside the callback with explicit error paths.
Test plan you can run in an afternoon
Bring your CI and a coffee. This is the sequence we use on client migrations:
• Unit pass on upgraded Node runtime.
• HTTP/2 fuzz: send intentionally malformed headers to ensure the server closes the connection without crashing. Verify error log visibility at both TLS socket and app levels.
• TLS client cert path: if applicable, run 1,000 connection cycles against getPeerCertificate(true) and watch memory—steady state only; no leak trend.
• Permission Model sanity: run job containers with --permission, ensure symlinked scripts still work only inside allowed dirs, and that UDS attempts are blocked without --allow-net.
• Timing stress: execute routes that allocate large buffers under load while toggling vm timeouts to make sure nothing odd slips into responses or logs.
Zero‑drama deploy patterns
Patching Node shouldn’t become a hero story. Use these patterns to keep incidents boring:
• Blue/green (infra‑level): build and soak the patched image in green, warm caches, then flip traffic via gateway routes. Roll back by re‑pointing to blue.
• Rolling with guardrails: start at 1% traffic in a non‑critical region; hold for 30 minutes; advance to 10%; then 50%; then global. Automate auto‑halt on error‑rate or latency deltas beyond your SLOs.
• Immutable base images: never apt‑get inside running containers. Rebuild with the patched base and promote images via digests.
• Observability ready: pre‑create dashboards for socket counts, TLS handshake failures, heap usage, and event loop lag per deploy group. You can’t troubleshoot what you can’t see.
People also ask
Which version should I upgrade to?
Stay on your major line and take the patched minor: 20→20.20.0, 22→22.22.0, 24→24.13.0, 25→25.3.0. Don’t jump majors in a security sprint unless you’d planned that work.
Do I need to restart all my pods?
Yes. The runtime fix lives in the Node binary and linked libraries. New containers or processes must be spawned from the patched build to be protected.
We don’t use the Permission Model—can we wait?
No. CVEs also cover HTTP/2 and Buffer allocation timing. The Permission Model fixes are only part of the story.
Will the undici update break my HTTP clients?
It shouldn’t in most apps, but teams that pinned undici or rely on undocumented behavior should test long‑lived connections, proxy settings, and retry logic. Validate connection pooling and backoff under load.
A 30‑minute audit you can automate
Drop this as a runbook in your repo to stop future scramble:
• Runtime inventory: emit node -v at service start and export as a metric label.
• SBOM on build: generate CycloneDX on every build; fail the pipeline on known‑exploited CVEs.
• Base image watch: alert when your pinned Node base falls behind the latest patch for that line.
• HTTP/2 regression test: keep a negative‑test suite that sends malformed headers and verifies graceful close.
• Permission Model canary: for services that set --permission, run a daily job trying to use a UDS and a symlink outside the allow‑list. Alert on unexpected success.
Data points worth pinning to your ticket
• Release date: January 13, 2026.
• Affected lines: 20.x, 22.x, 24.x, 25.x.
• Severity mix: 3 High, 4 Medium, 1 Low.
• Patch targets: 20.20.0, 22.22.0, 24.13.0, 25.3.0.
• Dependency bumps: undici to 6.23.0/7.18.0; c‑ares 1.34.6.
Keep that in your change record. Six months from now when an auditor asks, you’ll have crisp context.
Related shifts you shouldn’t ignore
Your Node patch window is a perfect time to sweep adjacent risk:
• npm and transitive crypto libs: check for recent patches in cryptography packages you embed; crypto bugs have outsized blast radius.
• Platform WAF rules and HTTP/2: if your WAF vendors adjusted rules for protocol‑level issues, re‑evaluate false positives after you patch the runtime.
• OS patching: align with your OS baselines. If you’re already planning a Windows/Linux maintenance window, stack your Node upgrade in the same slot. Our January 2026 Patch Tuesday breakdown can help you prioritize.
What to watch out for during rollout
• Memory plateaus that creep: watch heap usage on services that inspect client certs; the fix should stop growth. Any new trend suggests your code, not Node, is leaking.
• Silent permission denials: developer tooling that used to work inside a locked‑down job may now fail when UDS or symlink tricks are blocked. Document explicit allow‑lists.
• Stuck connections: if you pinned undici and inadvertently mixed versions across services, you can see asymmetry in retry/keep‑alive settings. Align them.
Operational guardrails we recommend
• Freeze window with an escape hatch: a 48‑hour post‑deploy change freeze on the platform prevents noise. Exempt only emergency security changes.
• Canary user cohort: mirror real traffic. Synthetic is helpful, but nothing catches edge cases like production patterns at 1%.
• One CVE, one PR, one tag: keep the change surface tiny. Upgrade the runtime, rebase, ship. Don’t sneak in refactors.
Where this leaves the Permission Model
The Permission Model is getting sharper. The symlink and UDS fixes show a team iterating towards a real, enforceable boundary. Is it ready for every multi‑tenant use case? Not yet. But for scoped tasks and job runners, it’s viable—especially when paired with container isolation and readonly filesystems. Treat it as a layered defense, not a silver bullet.

What to do next
• Patch to 20.20.0, 22.22.0, 24.13.0, or 25.3.0 on every service.
• Run the HTTP/2 negative tests and TLS memory check if applicable.
• Validate Permission Model jobs with symlink and UDS attempts.
• Remove undici pinning unless required, and align versions across services.
• Log your runtime versions at startup and export as metrics for ongoing visibility.
If your team wants a guided, low‑risk rollout, we can help you plan, test, and ship. See our security and delivery services, browse relevant work in the portfolio, and reach out via contacts. For mobile teams juggling parallel store updates, our Play and App Store policy primers—like App Store Age Ratings 2026: Ship Without Blockers—pair nicely with a platform patch window.
Zooming out: this January release is a reminder that platform hygiene pays off. Small, consistent upgrades keep you from wagering a quarter’s roadmap on a weekend patch party. Do the boring things well, and your uptime will thank you.





Comments
Be the first to comment.