Chrome Third‑Party Cookies Are Staying. Now What?
After years of delays, Google kept third‑party cookies in Chrome and dropped plans for a new, standalone cookie prompt. For teams that built roadmaps around the phase‑out, this sounds like a reprieve. It isn’t. The practical reality is that Chrome still allows cross‑site cookies, but Safari and Firefox continue blocking cross‑site tracking by default, and Chrome is pushing privacy protections like Incognito‑only IP Protection and stronger anti‑fingerprinting. The takeaway: treat the Chrome third-party cookies status as a stay of execution, not a pardon, and ship a privacy‑first architecture that works across all major browsers.

What actually changed—and when
On April 22, 2025, Google said it would keep the current approach in Chrome: users can still allow or block third‑party cookies in Settings, and Google would not roll out a new standalone prompt. Chrome’s early‑2024 1% test group that restricted cross‑site cookies for evaluation purposes remained, with temporary exceptions extended to prevent breakage in non‑ads use cases. Then, on October 17, 2025, the UK Competition and Markets Authority released Google from prior Privacy Sandbox commitments because the original deprecation plan was no longer in scope. Meanwhile, Chrome continues to enhance Incognito protections (including IP masking via proxy in eligible regions) and to promote privacy APIs developers can opt into.
Do those dates mean “business as usual”? Not quite. Safari has blocked third‑party cookies by default since 2020, and Firefox has blocked tracking cookies by default since 2019, now with Total Cookie Protection. Cross‑browser behavior is fragmented; Chrome’s decision only stabilizes one slice of the landscape.
What this means for your 2026 roadmap
Here’s the thing: if your analytics, ads, or embedded SaaS flows rely on classic third‑party cookies, they already fail for a meaningful share of traffic outside Chrome. They also degrade in Chrome’s Incognito and in stricter enterprise policies. The winning pattern in 2026 is a first‑party‑centric design with scoped cross‑site access only where there’s a user‑benefit and explicit consent.
From a product perspective, assume three user states at all times: (1) full first‑party state available, (2) partitioned third‑party state available (via CHIPS), and (3) no third‑party state unless granted (via Storage Access API or user settings). Your job is to build happy paths for each and degrade gracefully without support costs exploding.
Build a cookie‑resilient stack (even if cookies stay)
The goal is simple: predictable measurement and login/embedded experiences across Chrome, Safari, and Firefox—without fragile browser‑specific hacks. Use this blueprint.
1) Rebase identity on first‑party
Move identity and consent checks to the top‑level site you control. That means first‑party IDs (via secure, HTTP‑only cookies or tokens) tied to your domain, with short lifetimes and rotation. For cross‑domain estates, standardize your auth broker (OIDC) and use one canonical login domain to minimize hops that create storage partition mismatches.
For client analytics, prefer server‑side collection with a layer that enforces consent decisions and decorrelates identifiers. This curbs vendor pixels proliferating in fragile third‑party contexts and reduces breakage when cross‑site cookies disappear for a subset of users.
2) Use CHIPS for legitimate embeds
Cookies Having Independent Partitioned State (CHIPS) lets you opt specific cookies into partitioned storage with the Partitioned, SameSite=None, and Secure attributes. Partitioned cookies prevent cross‑site tracking while preserving legitimate third‑party functionality—think chat widgets, payments, or embedded dashboards that need stable state only within the top‑level site the user is on. Ship CHIPS where you can because it works across Chromium and is now supported in modern Safari builds, reducing variance between browsers.
Practical guardrails: document which cookies should be partitioned and why; avoid name collisions between partitioned and unpartitioned cookies; and expire or rename legacy cookies to prevent ambiguous reads. Verify setup in DevTools where the partition key appears, and regress with automated checks.
3) Storage Access API for user‑driven exceptions
When an embedded third‑party truly needs unpartitioned cookie access—SSO flows for a federated IdP are the classic case—use the Storage Access API (SAA). Embed with the correct iframe sandbox tokens, then call document.hasStorageAccess() and document.requestStorageAccess() on user interaction. Expect policy differences by browser (grant duration, prompts, or first‑party visit requirements), and instrument the outcomes. This is your narrow, auditable escape hatch—not a blanket replacement for third‑party cookies.
4) Respect consent, centrally
Consolidate consent capture and enforcement into one place. Whether you use IAB GPP, regional opt‑ins, or custom toggles, store the decision in first‑party state and pass it through your server‑side pipeline. If you run many properties, version your consent schema so front‑end and ETL agree on signal meaning during rollout. A clean consent backbone reduces incidental leakage from legacy tags still trying to set third‑party cookies.
5) Measurement that survives partitioning
Modelled conversions and event stitching should survive even with partitioned or blocked cross‑site cookies. That means: use event‑level deduplication keys in first‑party context, ensure click IDs don’t rely on third‑party reads, and prefer outbound link decoration that complies with your privacy policy over client‑side piggybacking. Validate your outcomes across Chrome normal/Incognito, Safari, and Firefox with automated scenarios in CI.
If you need help implementing a privacy‑first analytics pipeline or adjudicating which tags to keep, our team’s privacy‑first analytics implementation service can get you there without guesswork.
People also ask
Do I still need a CMP if Chrome keeps cookies?
Yes. Consent isn’t just about Chrome or cookies; it’s about legal and platform obligations across markets. Your CMP governs data use and vendor activation regardless of how a browser stores state. Keep it. Tighten it. And connect it to your server‑side tagging so decisions actually change behavior.
Will Chrome’s IP Protection break my analytics?
It can change your attribution picture in private browsing or managed environments where the feature is enabled—especially for third‑party embeds. Plan for less stable IP‑based geo and de‑dupe. Treat IP‑based heuristics as hints, not keys. The fix is first‑party identity and better event design, not fighting the proxy.
What about Safari and Firefox?
Safari blocks cross‑site cookies by default and encourages SAA for specific user‑initiated access. Firefox blocks tracking cookies by default and isolates others with Total Cookie Protection. Build for these stricter baselines; Chrome compatibility falls out naturally when users allow third‑party cookies.
Let’s get practical: a 30‑day, two‑track plan
Here’s a plan you can actually ship. Run Tracks A and B in parallel; don’t wait for a “big bang” cutover.
Track A: Reliability & privacy (weeks 1–4)
- Audit cookie usage. Classify every cookie: first‑party, third‑party unpartitioned, third‑party partitioned (CHIPS). Delete or convert anything that doesn’t have a documented purpose and retention.
- Implement CHIPS for embeds that need stable state but not cross‑site tracking. Add automated tests to catch regressions when attributes are missing.
- Add SAA where a user‑benefiting flow needs unpartitioned cookies (e.g., federated SSO in an iframe). Gate requests behind user actions, not page load.
- Centralize consent. Store decisions server‑side; block vendors until consent exists; log enforcement actions for auditability.
- Harden Incognito and strict‑browser paths. Ensure core journeys work with: (a) third‑party cookies blocked, (b) partitioned only, (c) no cross‑site storage without access grants.
Track B: Measurement that survives (weeks 2–4)
- Move browser tags to server‑side where feasible. Enforce data minimization, consent, and vendor contracts at the edge.
- Revisit attribution. Prefer first‑party click IDs and signed events. Reduce reliance on IP/UA fingerprints that are unstable or policy‑sensitive.
- Ship a cross‑browser QA harness. Automate Chrome normal/Incognito + Safari + Firefox runs for login, checkout, and key conversion paths with storage conditions toggled.
- Define “known‑good” dashboards. Combine technical indicators (cookie partitions, SAA grants) with business metrics so alerts track meaningful outcomes, not just noisy deltas.
Data‑backed map of what’s shipping
Key milestones to anchor your risk assessment: Chrome restricted third‑party cookies for 1% of users starting January 4, 2024 as a test milestone; on April 22, 2025, Google said it would keep third‑party cookies and skip a new prompt; on October 17, 2025, the UK CMA released Google from prior Privacy Sandbox commitments. CHIPS support is available by default in modern Chromium and Safari builds, while Storage Access API is available with browser‑specific rules. Plan your rollouts against these dates, not rumors.
Risks, limitations, and edge cases
Expect variance by browser, region, and mode (Incognito vs. normal, managed enterprise vs. consumer). SAA grant durations and prompts differ. Some enterprise policies disable third‑party state entirely. IP Protection reduces the utility of IP‑based heuristics. And privacy updates can ship behind flags, then ramp quickly. Your mitigations: feature‑flag your storage strategies; fail safe (functional UX over perfect measurement); and monitor storage outcomes, not just business KPIs.
Also, beware of DIY fingerprinting “fixes.” They’re brittle, increasingly blocked, and often out of bounds for your privacy policy. Invest in first‑party identity, not entropy hacks.
How this affects SaaS embeds and multi‑brand estates
If you vend a widget, SDK, or embedded dashboard, adopt CHIPS for persistence and offer a documented SAA path for sign‑in. Publish a one‑pager for integrators: exact cookie attributes, sandbox requirements, and how you degrade gracefully without third‑party state. For multi‑brand groups, unify auth on one login domain and move customer analytics to first‑party ingestion per brand, then standardize event schemas upstream.
Need hands‑on help modernizing your web platform? See how we ship production‑grade web platforms and real client outcomes in our portfolio.
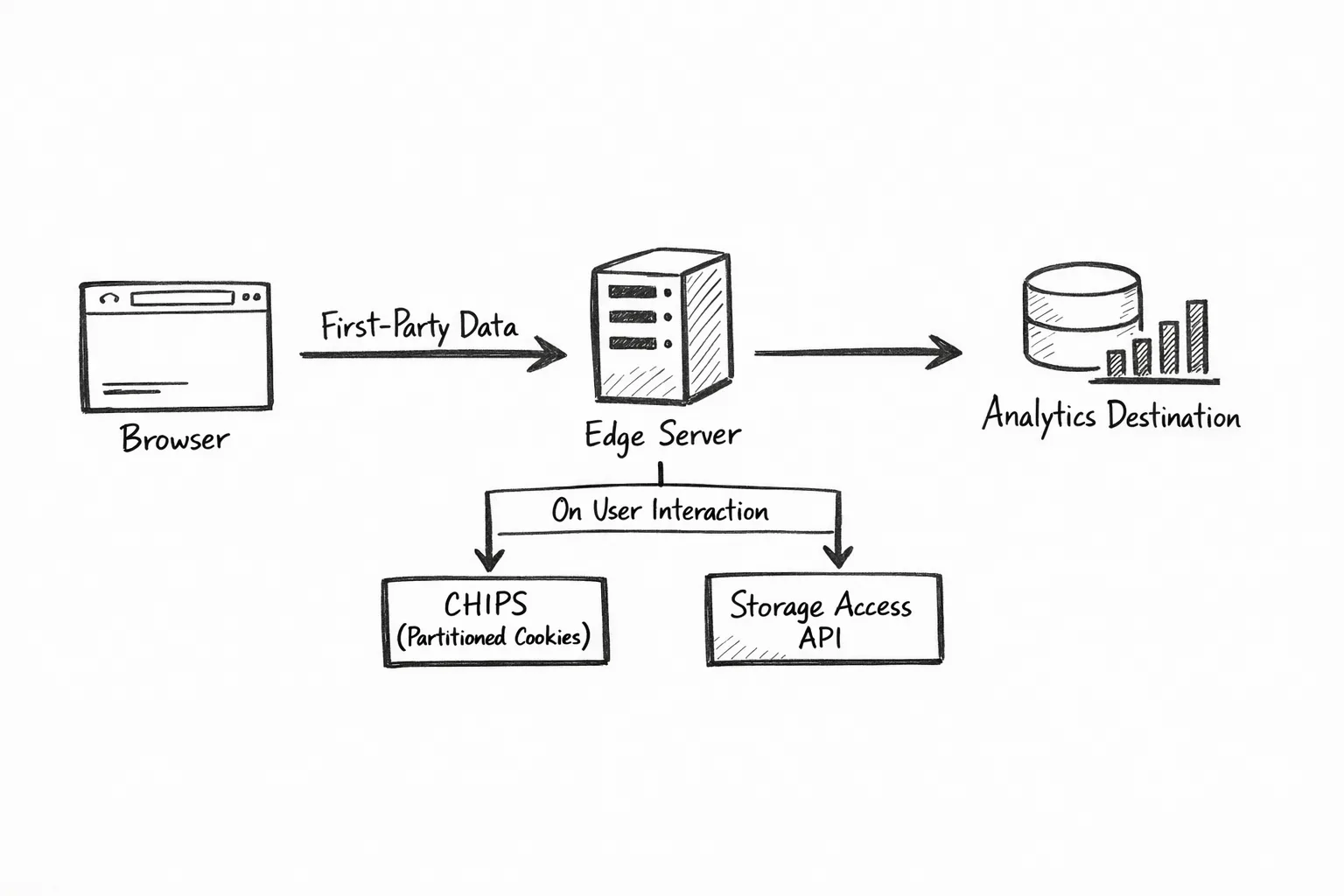
Reference implementation sketch
Here’s a minimal pattern we’ve shipped on client projects:
- First‑party session: HTTP‑only, short‑lived cookie on your domain. Rotate on privilege escalation. No third‑party reliance.
- Event collection: Browser sends events to your edge endpoint. Edge enriches only if consent=granted; otherwise, drop or anonymize. Sign requests to prevent vendor tampering.
- Embeds: For chat/payment/BI iframes, set a CHIPS cookie scoped to your site. For sign‑in in an iframe, request SAA after the user clicks “Continue.”
- Attribution: Prefer first‑party click IDs and link decoration you control, validated against consent. Avoid IP/UA as join keys.
- QA: Automated journeys for cookie states (blocked, partitioned, granted via SAA). Alert when partitioned reads fail on key pages.
If you’re also upgrading your front‑end this quarter, align this work with your framework upgrades. For example, when you upgrade your Next.js and React stack, wire the consent and analytics refactor into the same sprints to limit duplicative testing.
What to do next
- Week 1: Inventory cookies and tags. Decide: first‑party, CHIPS, or SAA—or delete.
- Week 2: Implement CHIPS for embeds; add SAA for user‑initiated access only. Turn on server‑side collection with consent enforcement.
- Week 3: Build automated cross‑browser tests for three storage states. Instrument success/failure on SAA requests.
- Week 4: Review dashboards. Replace IP‑based heuristics. Socialize the new data caveats with marketing and BI.
Chrome’s decision extended the runway, not the destination. Ship for a world where cross‑site state is gated, partitioned, or absent—then you’ll work everywhere. If you want a partner to stand up this architecture, talk to our team, or explore our broader capabilities on the Bybowu blog and services page.




Comments
Be the first to comment.