AWS Kiro just hit general availability, and it’s not just another AI assistant tucked into your editor—Kiro formalizes spec-driven development and now lives in your terminal, too. Pair that with a handful of quietly shipped platform updates—Lambda tenant isolation mode, API Gateway response streaming for REST, S3 ABAC, VPC encryption controls, NAT Gateway regional mode, and a dead-simple aws login—and you’ve got a very different AWS week than you had on November 18. If you’re an engineering leader, this is the moment to turn announcements into advantage.

Why this week’s releases matter
Here’s the thing: most teams don’t win by adopting every new service—they win by picking a few high‑leverage changes, then operationalizing them fast. The updates below either reduce risk (encryption and isolation), trim latency (streaming), cut ops toil (regional NAT, aws login), or align AI coding with real software engineering (Kiro).
AWS Kiro: spec‑driven coding meets the CLI
AWS Kiro is now generally available with property‑based testing for “spec correctness,” checkpointing, a Kiro CLI, and team plans. AWS also notes more than 250,000 developers have used Kiro since the preview. That’s not just marketing—PBT plus specs pushes AI coding closer to verifiable engineering instead of vibes. (kiro.dev)
Practically, Kiro does three useful things on day one: it forces intent into a living spec that agents respect, it stress‑tests implementations against generalized properties (not just brittle example tests), and it moves the same workflow into your terminal so power users aren’t trapped in a GUI. If you manage multiple repos, multi‑root workspaces reduce context‑switching friction. For teams with compliance needs, the organizational sign‑in and centralized management are the unlock.
Does AWS Kiro replace your IDE or your process?
No. Treat Kiro as a “spec‑first pair” that can plan, implement, test, and roll back in small loops. Keep code owners, trunk‑based merges, and CI checks exactly where they are. Kiro becomes an accelerator inside the process you already trust.
6 quiet, high‑impact AWS launches to adopt now
1) Lambda tenant isolation mode—multi‑tenant without the yak shave
Lambda now lets you isolate execution environments per tenant inside a single function. You pass a tenant identifier; Lambda ensures warm environment reuse for the same tenant, while keeping /tmp, globals, and caches tenant‑scoped. This removes the classic “one function per tenant” sprawl and the bespoke sandboxing that SaaS teams hack together. Availability is broad across commercial Regions. (aws.amazon.com)
When to use it: workflows that run untrusted tenant code, per‑customer model pipelines, or anything with strict data separation. Watch out for the creation‑time setting—you can’t flip an existing function to tenant mode. Plan migrations as you would any environment behavior change.
2) API Gateway response streaming for REST—TTFB down, timeouts up
API Gateway REST APIs can now stream responses progressively. For AI and data apps, this is a double win: dramatically better time‑to‑first‑byte and extended integration timeouts up to 15 minutes, plus support for payloads beyond 10 MB without awkward pre‑signed URL detours. That’s a real user‑perceived performance lift. (aws.amazon.com)
Where it fits: server‑to‑client generation (LLM tokens, report generation), long‑running workflows returning status streams, or media delivery that previously hit size caps. Just remember: streaming changes client expectations and error handling. Update SDK usage, retry logic, and UX affordances (spinners, partial renders).
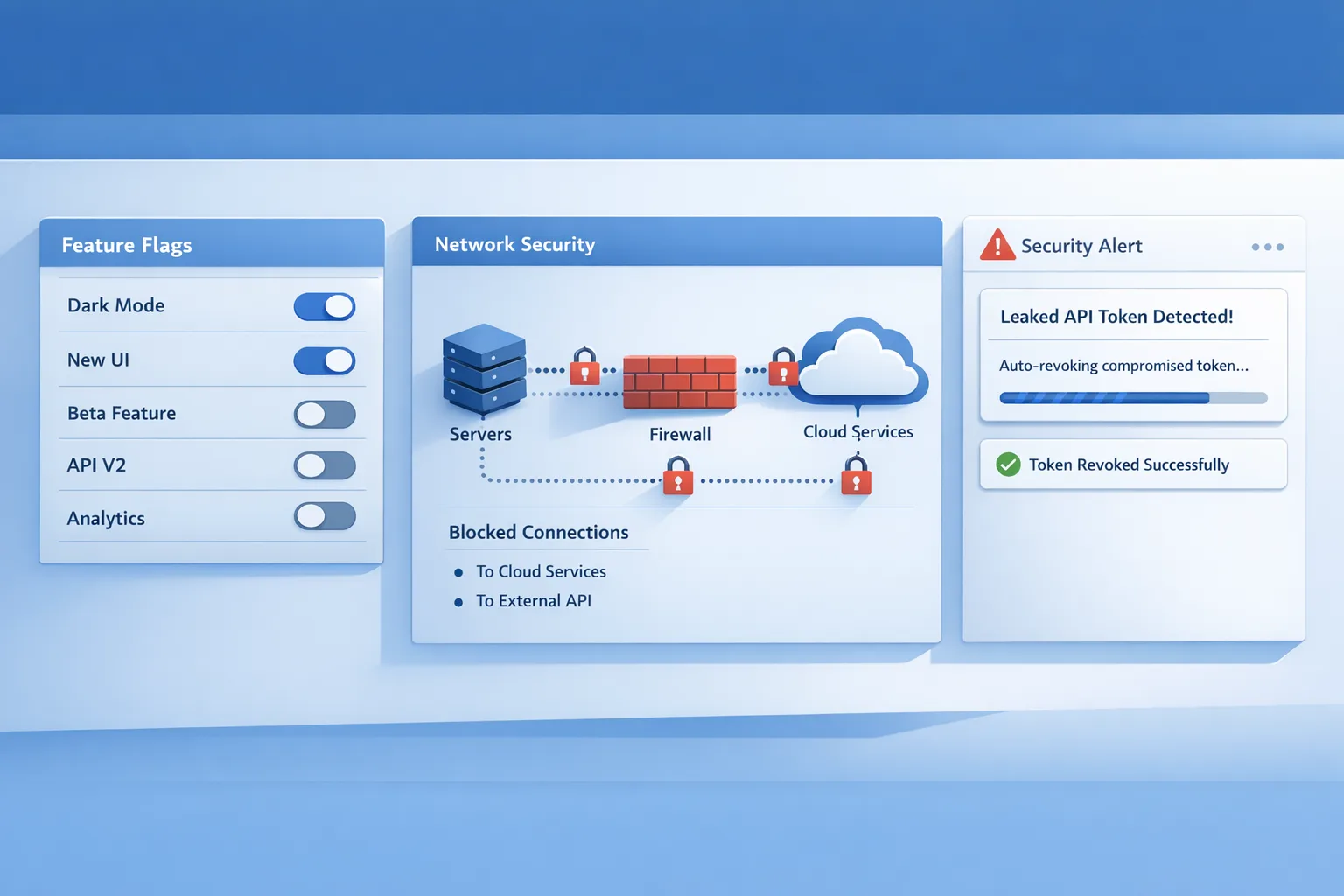
3) VPC encryption controls—click‑once compliance guardrails
This new VPC capability lets you monitor and then enforce encryption in transit within and across VPCs in a Region. It adds an encryption-status field to VPC Flow Logs and supports a monitored rollout before you flip to enforcement. It’s free until March 1, 2026, and available in a long list of Regions. If you carry HIPAA/PCI/FedRAMP obligations—or you just want fewer spreadsheets tracking TLS—turn this on. (aws.amazon.com)
Reality check: enforcement means anything not on Nitro or not using TLS will be blocked. Inventory older instance families, apply exclusions where required (internet/NAT gateways), and plan migrations. For platform teams, this is the nudge to retire legacy nodes you’ve been ignoring.
4) S3 ABAC for general purpose buckets—permissioning that scales with tags
Attribute‑based access control for S3 general purpose buckets brings first‑class tag‑driven authorization to the most common S3 model. You explicitly enable ABAC per bucket, then write tag‑aware IAM/bucket policies so access follows labels like environment, data classification, or cost center. It’s the right level of abstraction for large estates and aligns access control with the governance taxonomy you already use. (aws.amazon.com)
Gotchas: enabling ABAC switches tagging to the standard TagResource API (not PutBucketTagging), so audit existing automation. Also make sure the tags you rely on for access are protected from casual edits. Bonus: the same tags can drive cost allocation reporting.
5) NAT Gateway regional mode—fewer objects, fewer footguns
Regional availability mode lets a single NAT Gateway expand or contract across AZs automatically. You don’t need a public subnet to host it, and you avoid the route‑table churn that used to accompany AZ expansion. For a lot of VPCs, that’s simpler, cheaper to operate, and one less thing to misconfigure during a scale event. (aws.amazon.com)
Sanity notes: confirm IP sourcing when you bring your own IPs, and re‑review any compliance controls that assumed per‑AZ NATs. Update your Terraform modules so nobody provisions the old triad by habit.
6) aws login—zero long‑lived keys for local dev
There’s a new AWS CLI command that uses your existing console sign‑in method to mint short‑lived credentials for SDKs and tools. For most teams, this eliminates static access keys on laptops, supports profile switching, and rotates tokens automatically. You’ll need AWS CLI v2.32.0+ and a small IAM change to allow the new Sign‑In actions. Treat this as a Day‑0 security improvement. (aws.amazon.com)
What AWS Kiro changes in your workflow (and what it doesn’t)
AWS Kiro doesn’t magically erase system design, code review, or staging gates. What it does do is collapse the distance between intent and implementation. Property‑based tests enforce that the thing you built actually satisfies the behavior you wrote down. Checkpointing helps you prune bad agent branches without tossing good work. And the Kiro CLI means senior devs can live in the terminal while junior devs use the IDE and both share specs, agents, and guardrails. (kiro.dev)
Here’s how we’re coaching clients to adopt it:
- Write EARS‑style requirements for a single, low‑risk feature in your codebase. Keep the spec tight and testable.
- Let Kiro generate properties and run them; patch either the spec or the code until PBT goes green.
- Codify “steering rules” so agents never alter tests to pass checks—that’s the classic failure mode.
- Promote the pattern to a second team after your first sprint retrospective, not before.
Implementation playbook: 30–60–90 days
Day 0–30: secure the foundations
Security and correctness first. Turn on VPC encryption controls in monitor mode across dev and staging; add the new Flow Log field to your SIEM queries. Enable S3 ABAC on one non‑prod bucket with a clear tag policy. Roll out aws login to your engineering laptops and block static keys going forward. Create a sandbox Lambda function in tenant isolation mode to validate caching and cold‑start behavior per tenant.
Day 31–60: performance and platform hygiene
Flip a user‑facing endpoint to API Gateway streaming and measure TTFB in synthetic tests and RUM. Migrate an internal service to the NAT Gateway regional mode and retire per‑AZ NATs. For Kiro, move from one feature to one product area; publish a spec template and a PBT cookbook in your internal wiki. At this point, capture a few “this broke, and why” write‑ups so lessons survive team changes.
Day 61–90: enforce and expand
Turn on VPC encryption controls in enforce mode for one new VPC and ship a runbook for exceptions. Enable S3 ABAC on production buckets with sensitive data and lock tag writes behind a small platform team. Promote Lambda tenant isolation to a user‑facing path with clear SLOs. For Kiro, integrate CLI workflows into CI so property tests run in pre‑merge checks—and most importantly, ensure code owners approve all spec changes just like code.
People also ask
Is AWS Kiro safe for regulated teams?
It’s as safe as the controls you wrap around it. Kiro’s GA adds team management and AWS org sign‑in, but you still decide where specs and repos live, how secrets are handled, and whether agents can run shell commands. Use least‑privilege repos, restrict agent tool permissions, and tie usage into your existing DLP and audit trails. (kiro.dev)
Does API Gateway response streaming increase costs?
You’ll pay for the same API Gateway metrics plus any additional data transfer from longer‑lived connections. The real win is UX: if your TTFB drops from two seconds to 100 ms and tokens trickle in, abandonment falls. Benchmark before and after and keep an eye on concurrent connection limits. (aws.amazon.com)
Should we migrate all NAT Gateways to regional mode?
Not blindly. If you’ve got compliance controls or tooling that assume per‑AZ NATs, test first. For greenfield VPCs, default to regional mode; for brownfield, migrate one VPC and verify IP allowlists, failover behavior, and cost deltas. (aws.amazon.com)
Tradeoffs and edge cases
Lambda tenant isolation creates more execution environments in exchange for simplicity; do a cost/perf check at your memory settings. API Gateway streaming shifts complexity to the client—broken proxies and early disconnects can surprise you. VPC encryption enforcement will surface every straggler instance family you never got around to upgrading. And S3 ABAC makes tags security‑critical; protect them like code.
Zooming out: platform work that pays for itself
None of these launches are flashy on their own. Together, they reduce the “surface area for mistakes” that cause incidents and slow velocity. We’ve seen this movie with edge outages and mis‑tuned infra before—being proactive beats postmortems. If resilience is top of mind, our resilience playbook walks through blast‑radius isolation patterns you can pair with today’s VPC and Lambda features. If spend is biting, our write‑up on cutting compute costs without rewrites shows the kind of quick wins you can replicate in AWS with the NAT and streaming updates.
Want help sequencing the changes? Here’s how our cloud modernization work typically engages: short discovery, targeted pilots, then co‑delivery with your team so you keep the muscle for the next upgrade cycle. If you’re ready, talk to us—we’ll tailor a path that fits your stack and runway.
What to do next (this week)
- Pick one: VPC encryption controls in monitor mode or API Gateway streaming for your most visible endpoint. Ship it.
- Roll out
aws loginorg‑wide and start deleting static keys. - Trial AWS Kiro on a bounded feature with property‑based tests and checkpointing. Keep code owners on the spec.
- Convert one VPC to NAT regional mode and update Terraform modules so it’s your new default.
- Enable S3 ABAC on a dev bucket; write the tag policy you’ll scale to prod.
Bottom line
AWS Kiro gives you a way to make AI coding accountable to a spec. The platform updates make your network safer, your APIs faster, your IAM cleaner, and your developers less likely to leak keys. Adopt two or three of these now and you’ll roll into December with fewer risks, faster endpoints, and a team that’s shipping rather than chasing incidents.





Comments
Be the first to comment.